Release notes archive
2024-09-27: Request count and sessions chart temporarily removed
The request count and sessions chart have been temporarily removed. They will be reenabled once data issues have been addressed.
Resolved issues
- CSS fixes of signing options in OIDC and SAML provider settings.
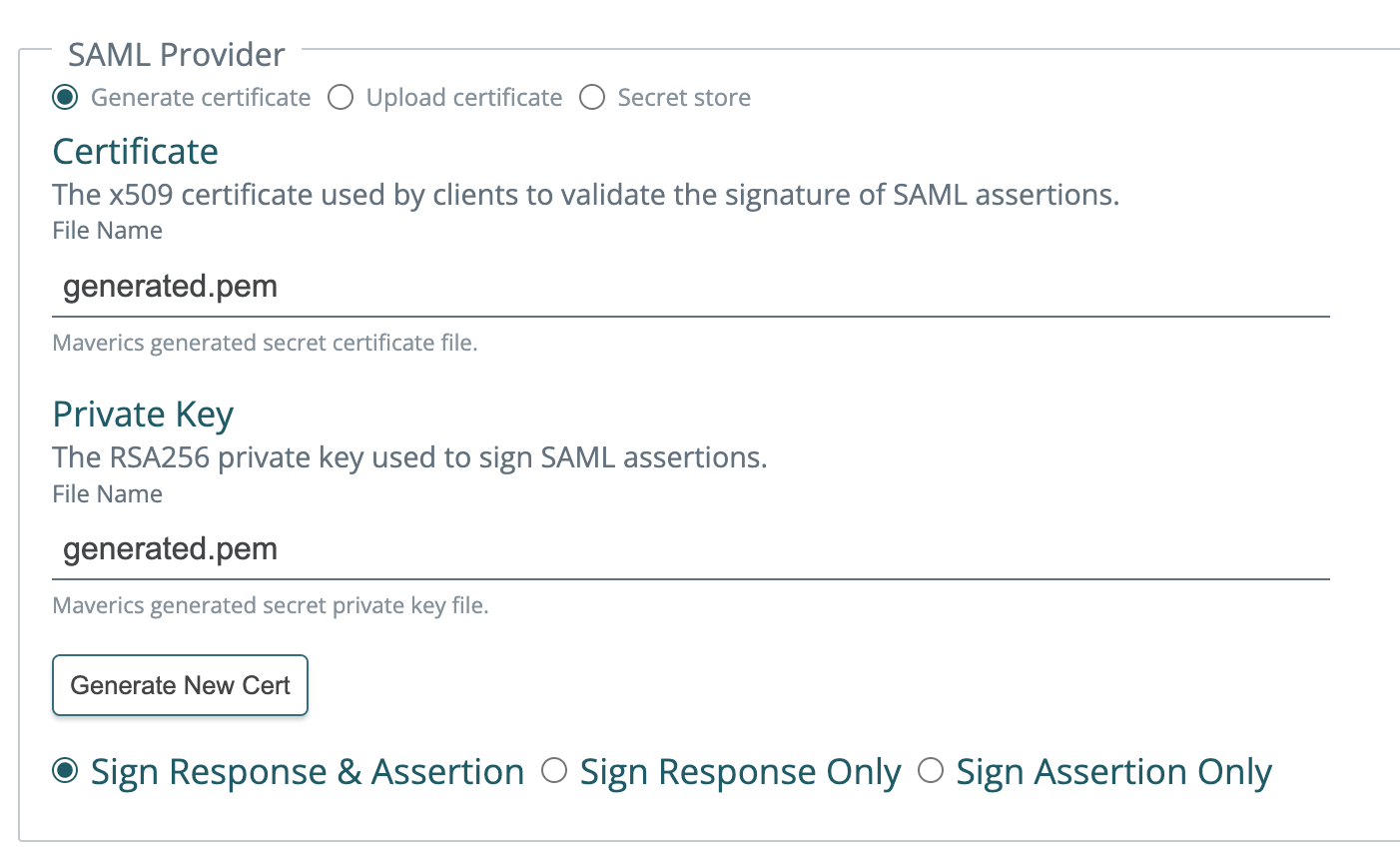
2024-09-16: Improved layout of SAML signing options, bug fixes
The choice between signing responses vs assertions now has a radio button that matches the new SAML app type options.
Resolved issues
- Idle timeout settings will now persist between edits.
- Orchestrator uptime is correctly appearing on the Orchestrator Telemetry page.
- The Request Count chart is now appearing when viewing an Orchestrator’s Telemetry.
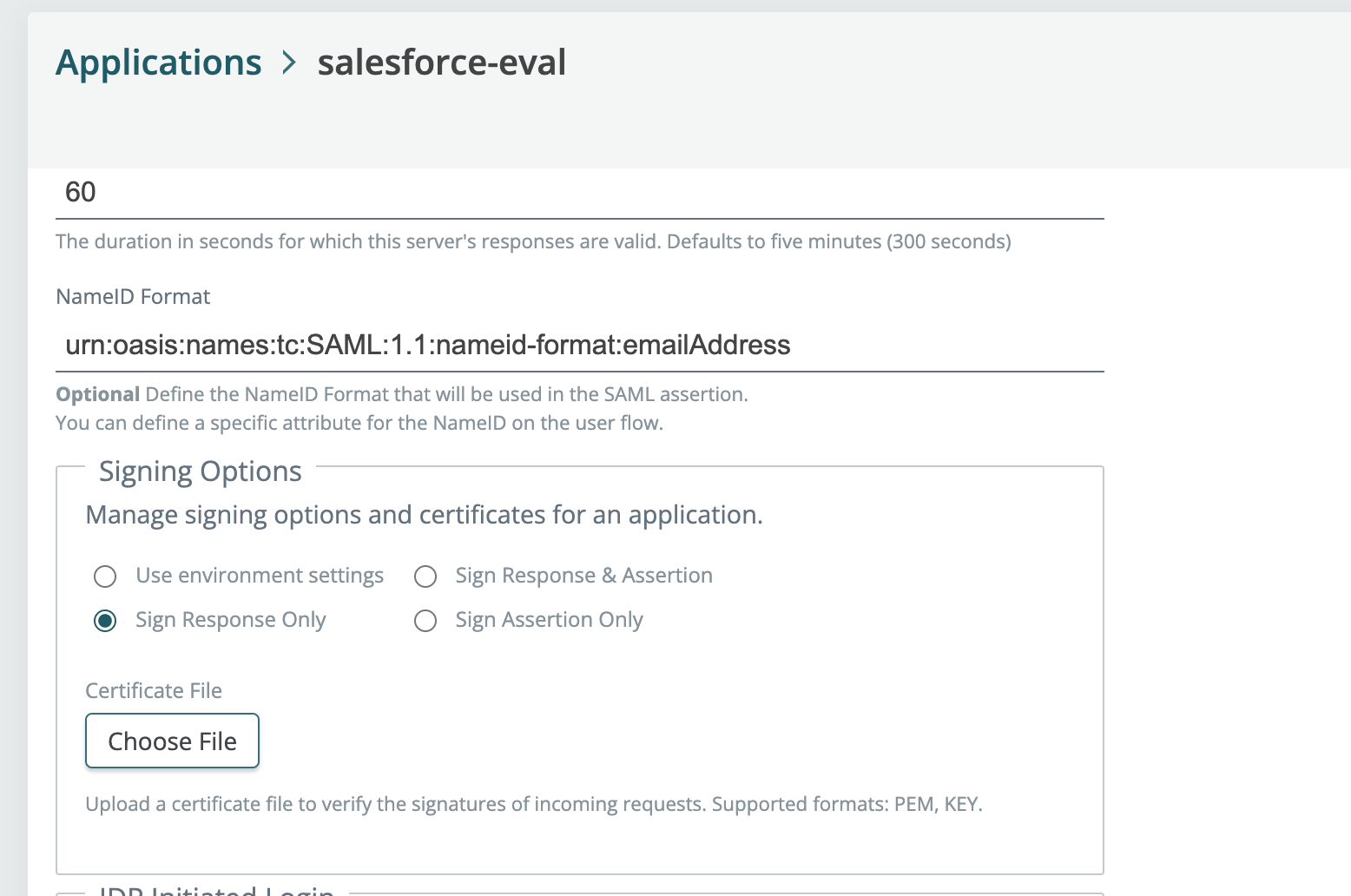
2024-09-12: New SAML app signing options, use secret variables for certs
Set signing options per SAML app
You can now override environment-level SAML provider signing options to either disable signing assertions or responses.
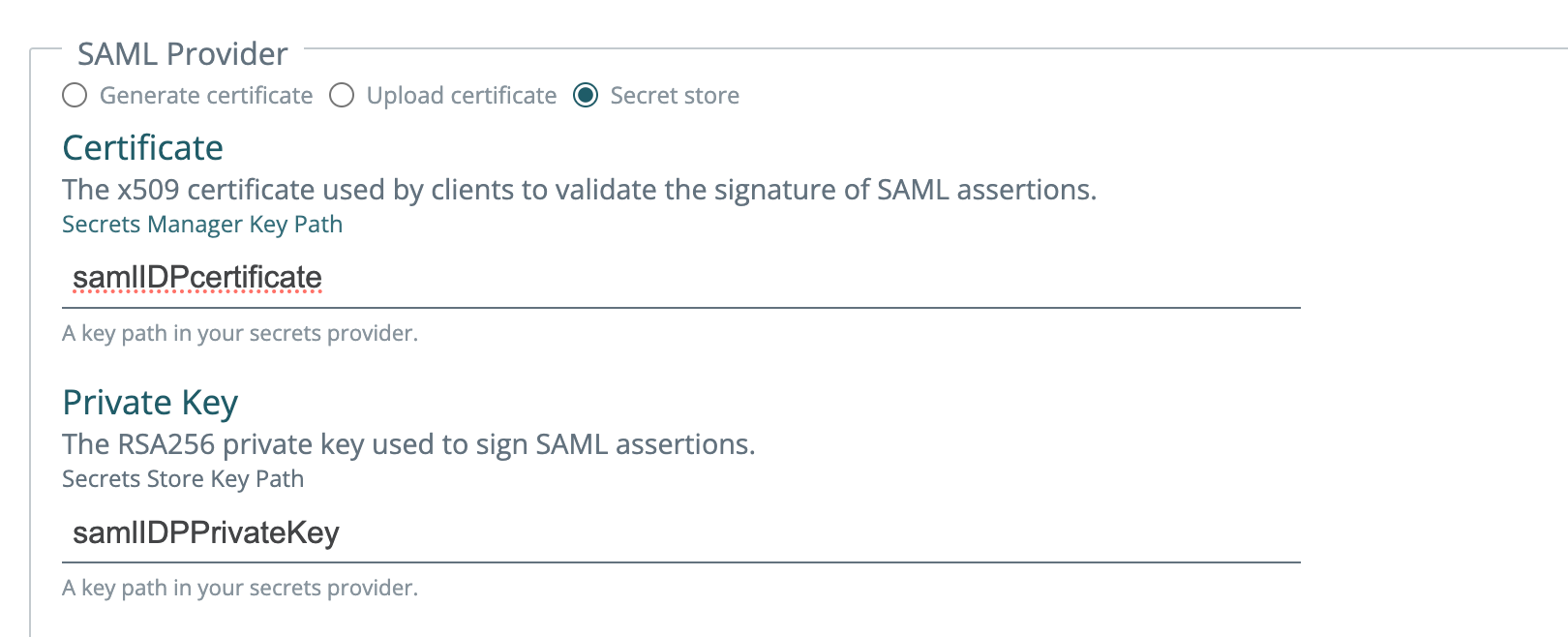
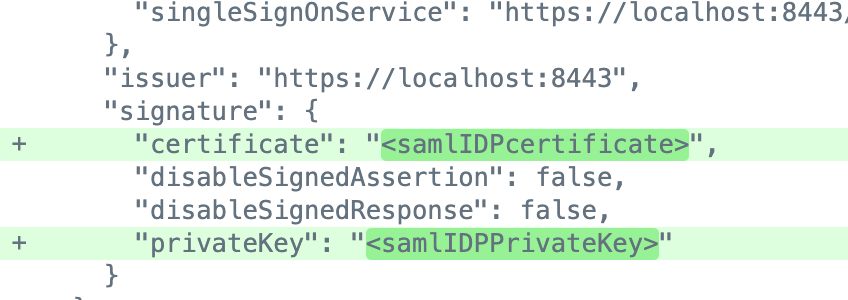
Use a hardware security module (HSM) for SAML and OIDC certs and keys
You can now specify a secret ID to pull a cert or key from an HSM.
2024-09-09: Continuity: ADFS support, support for HYPR QR code authentication, regenerate certs bug fix
Continuity: ADFS Support
You can now add Identity Service Health Monitoring to ADFS and use it in a continuity strategy.
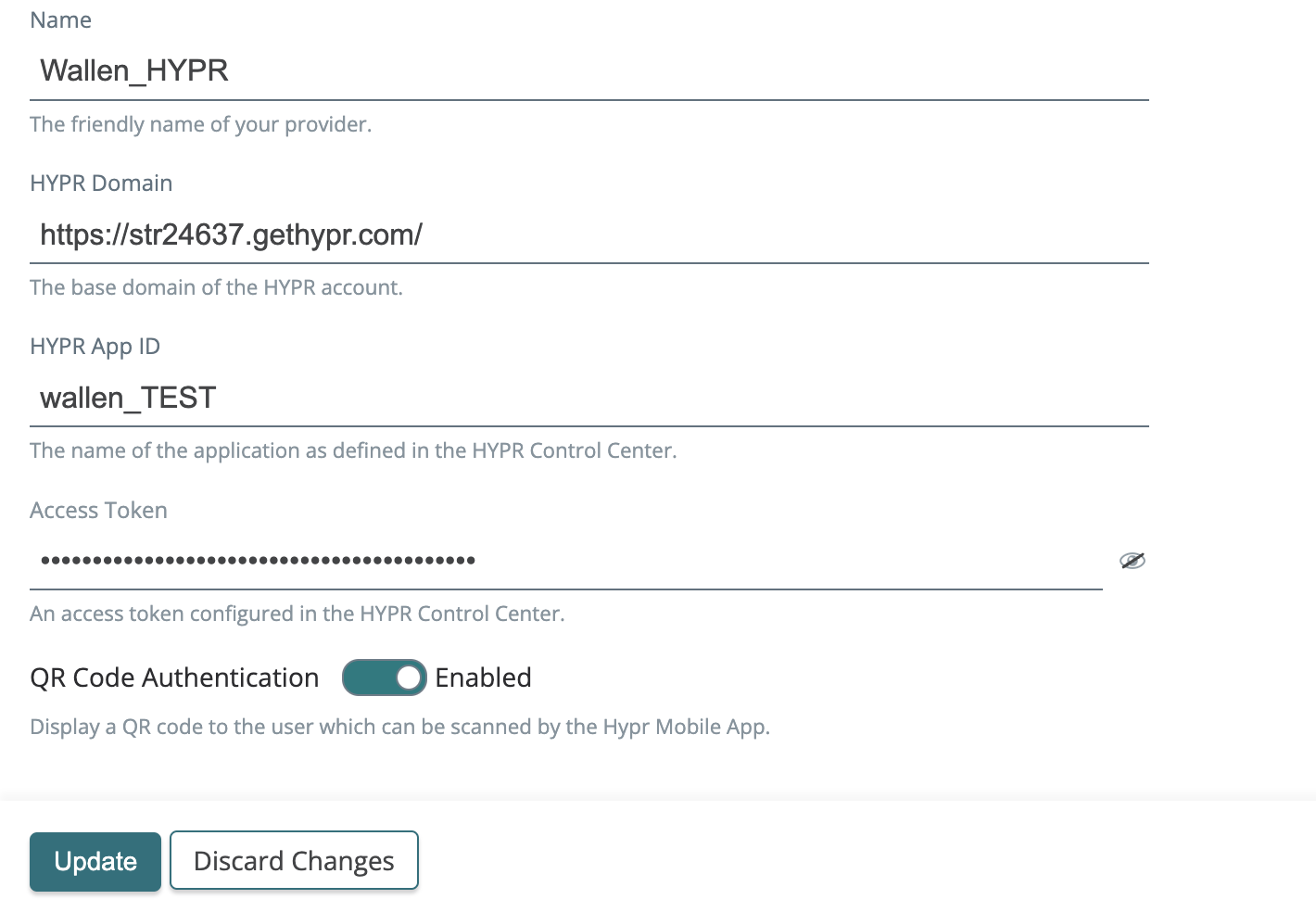
Support for HYPR QR code authentication
You can now enable HYPR QR code authentication when defining HYPR as a IDP.
Resolved issue
- When you upload and delete custom certs in OIDC or SAML provider settings, they will now revert back to regenerating certs.
2024-08-29: OIDC authorization rules, LoadAttributesSE for SAML and OIDC app type user flows
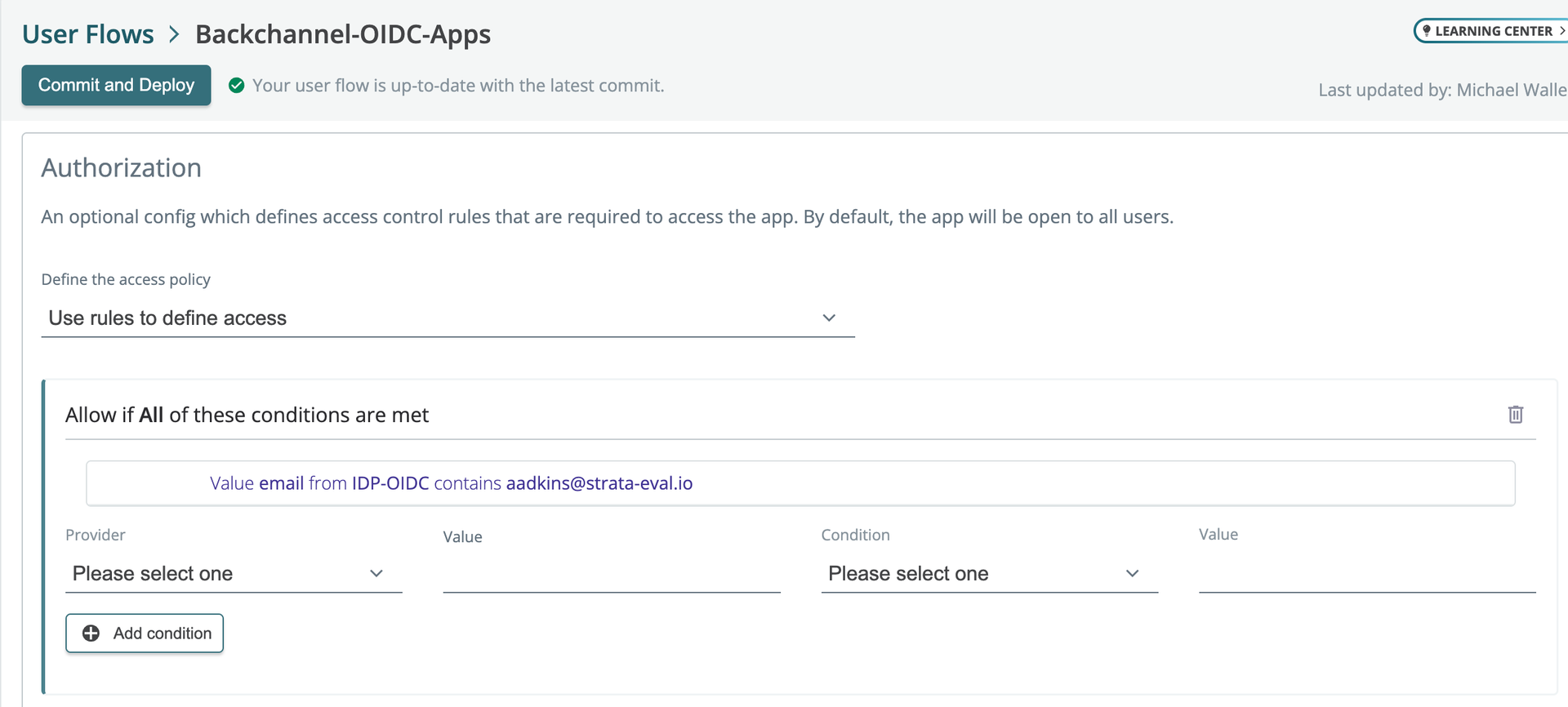
OIDC authorization rules
You can now define authorization rules in OIDC app type user flows.
LoadAttributesSE
You can now attach and use a LoadAttributeSE with OIDC and SAML app user flows. The user experience is now consistent across all app types.
To use a LoadAttribute SE:
- Define a LoadAttribute SE from the service extensions area
- In your OIDC or SAML app type user flow, scroll to attribute providers and select the service extension in the drop down.
- Use it in a authorization rule when building a claim.
Resolved issues
- You can now directly reference an asset used in a API app type user flow.
- Incident resolved: Orchestrator telemetry is back for the Canadian instance.
2024-08-22: Support for multiple OIDC secrets, new telemetry date range
You can now define multiple secrets for OIDC clients.
Orchestrator telemetry
You can now define a date range longer than 15 minutes when viewing Orchestrator Telemetry.
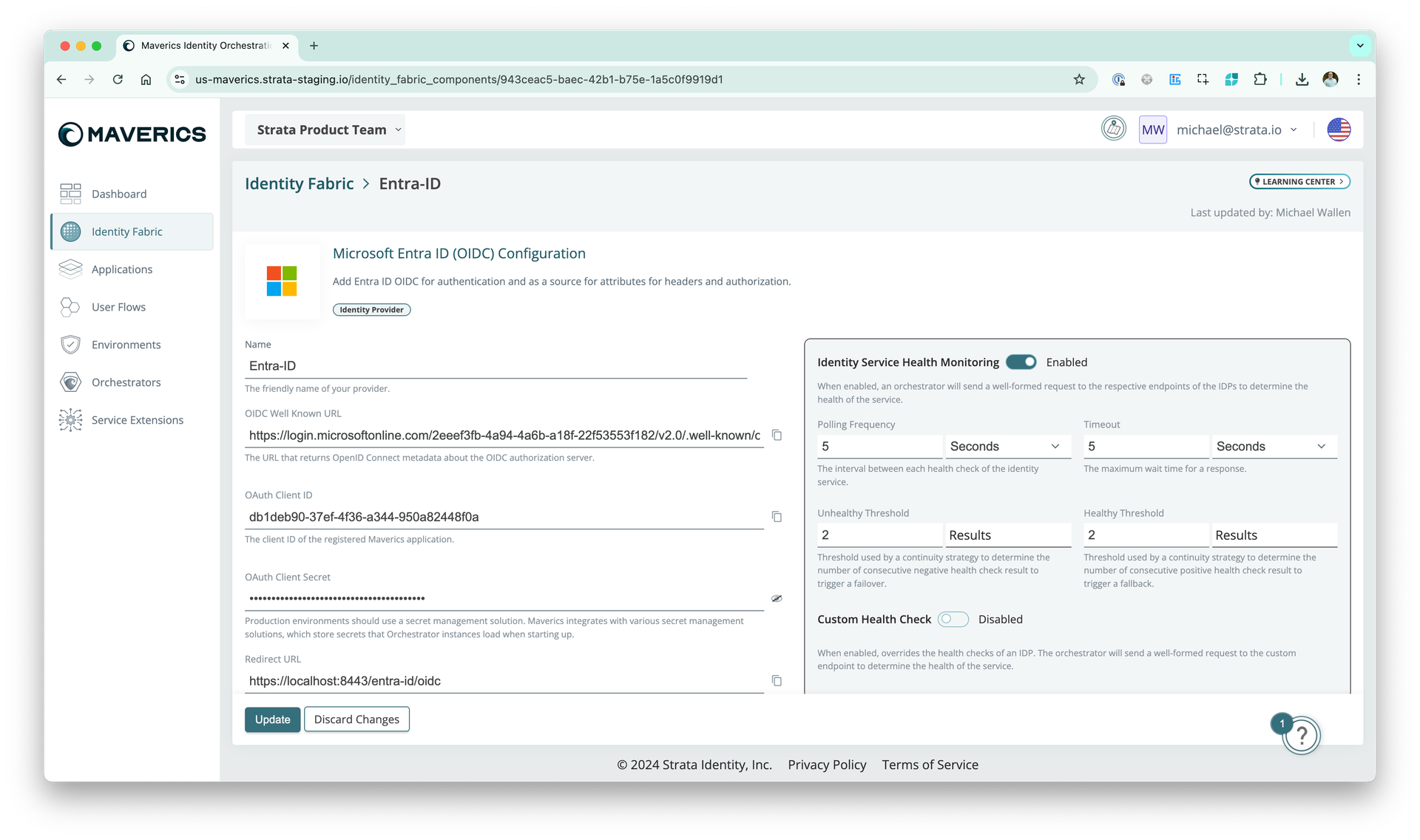
Identity fabric
We’ve improved the Identity Fabric page with a cleaner layout and wider fields.
Resolved issue
- Deploying a user flow will no longer include identity health monitoring config unless it has been specified.
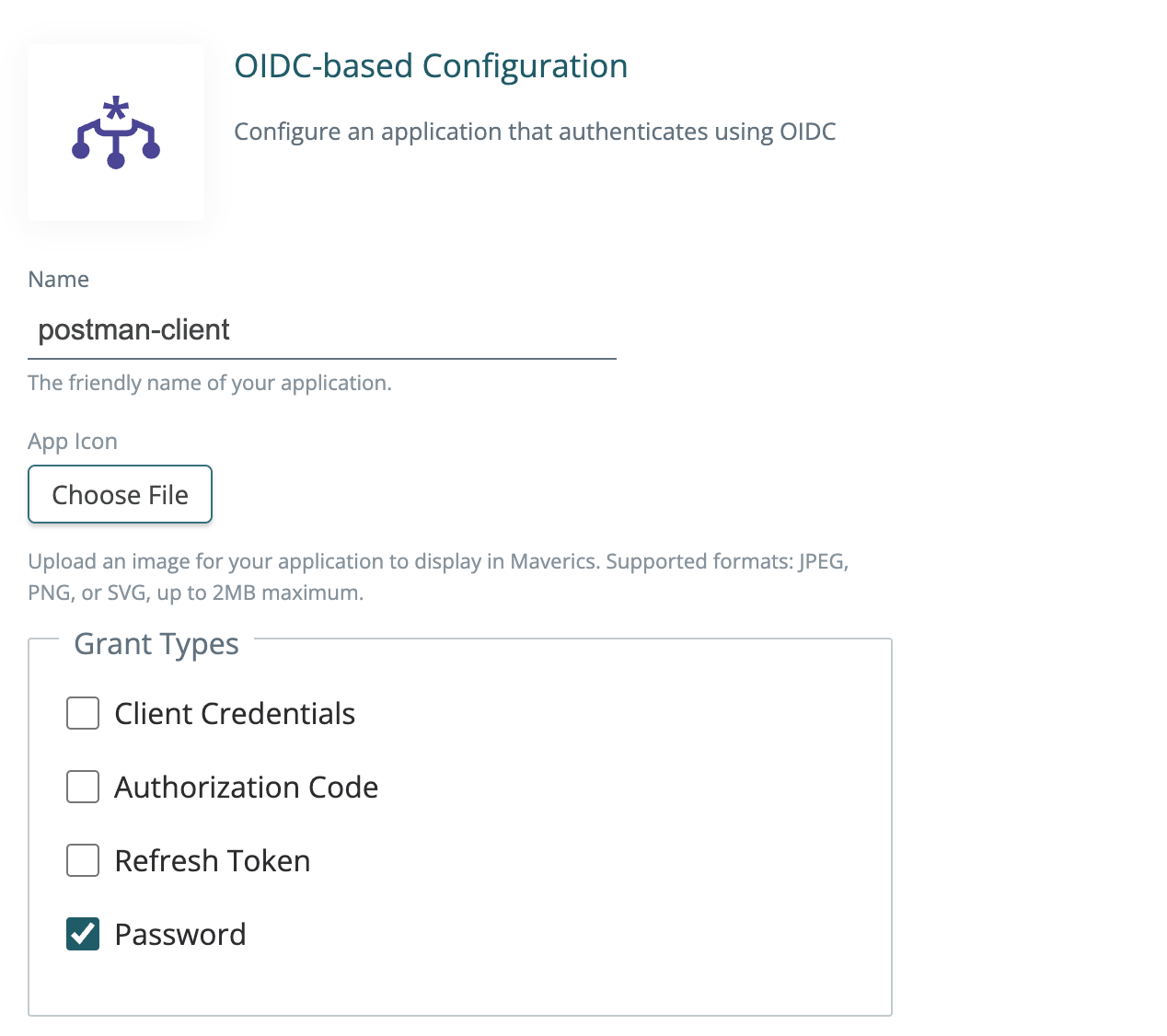
2024-08-19: OIDC grant type updates and bug fixes
We’ve added more details on OIDC grant types to help guide you in configuration.
Resolved issue
- A user flow will now correctly show a status of up to date if it references a IDP with a custom health check endpoint and TLS settings.
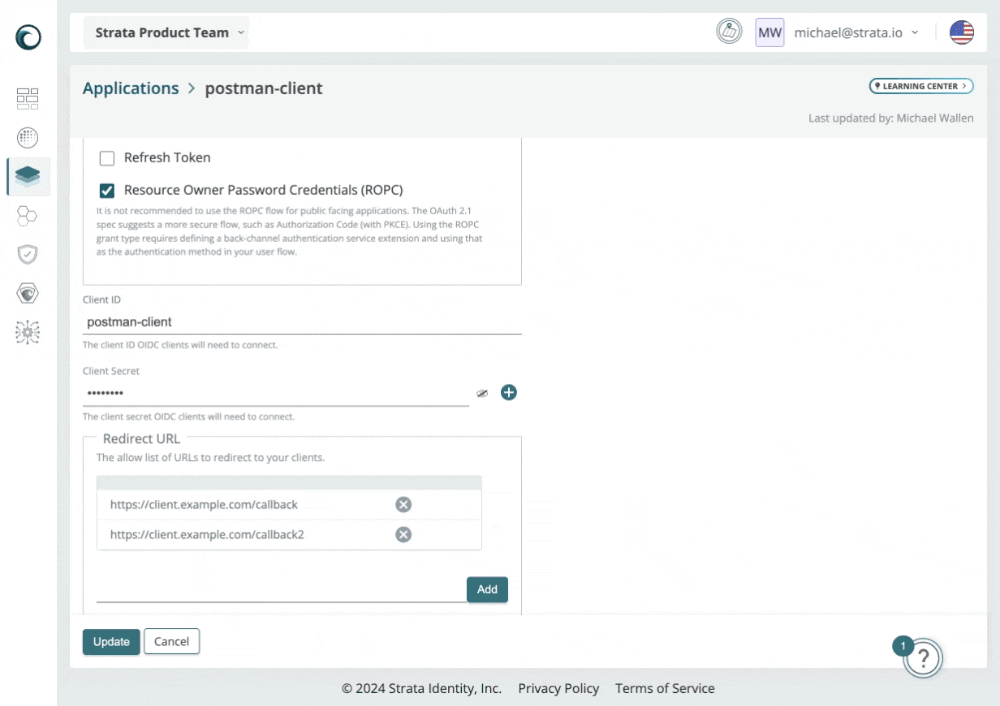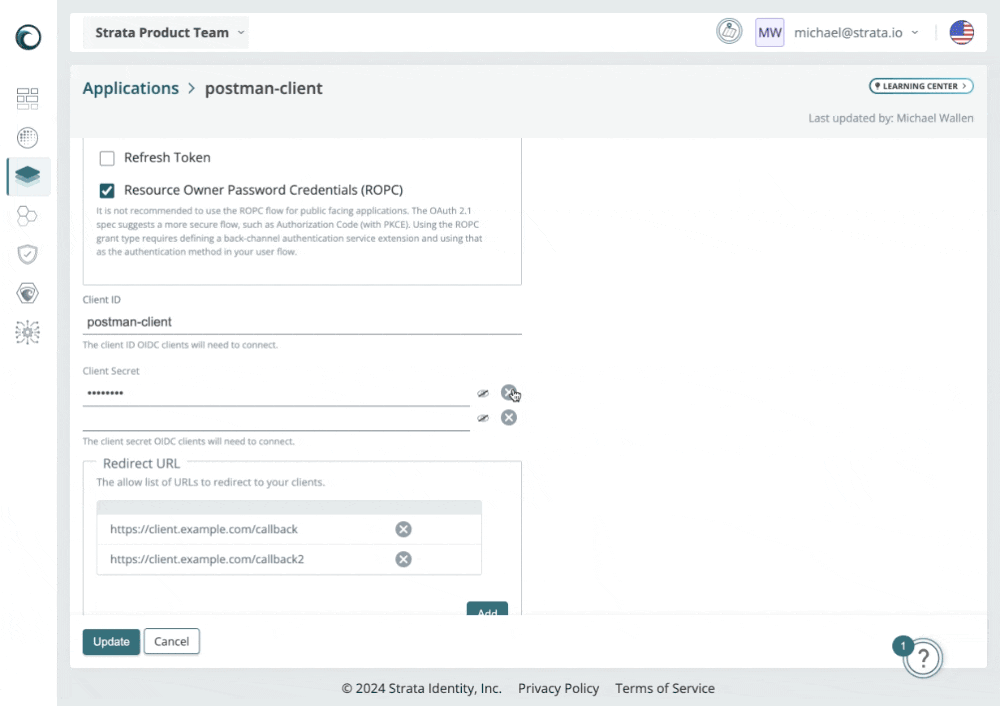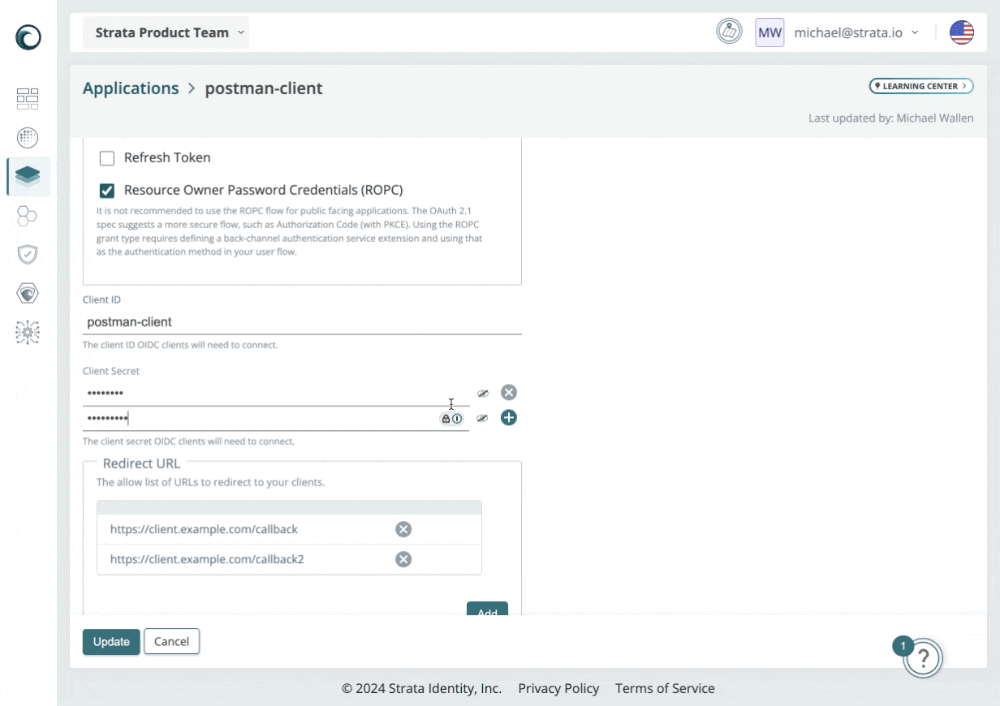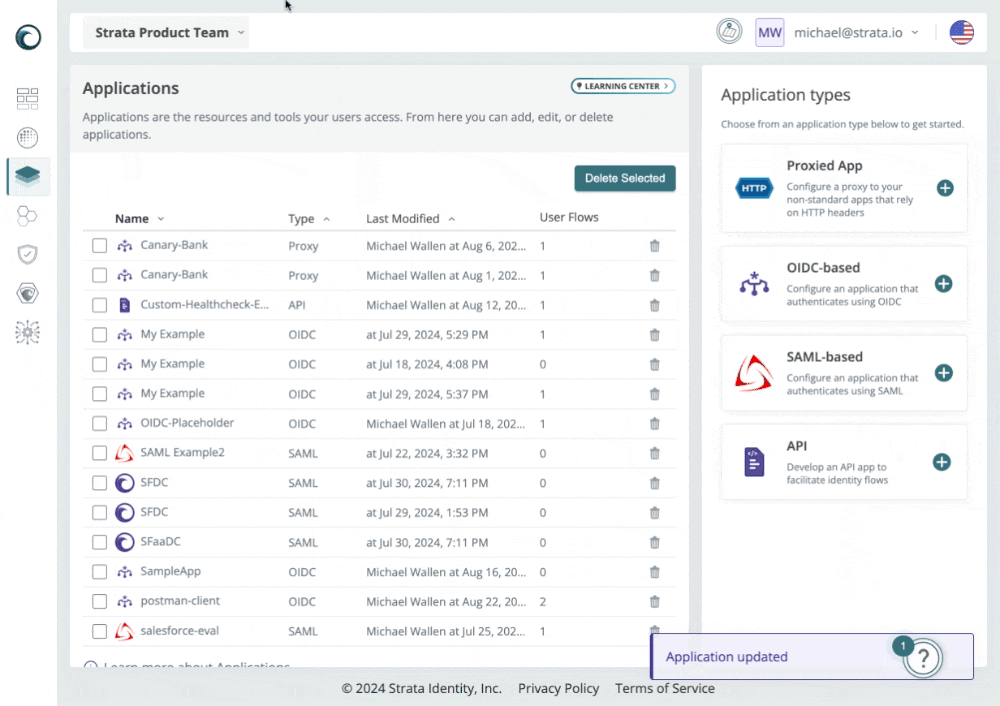
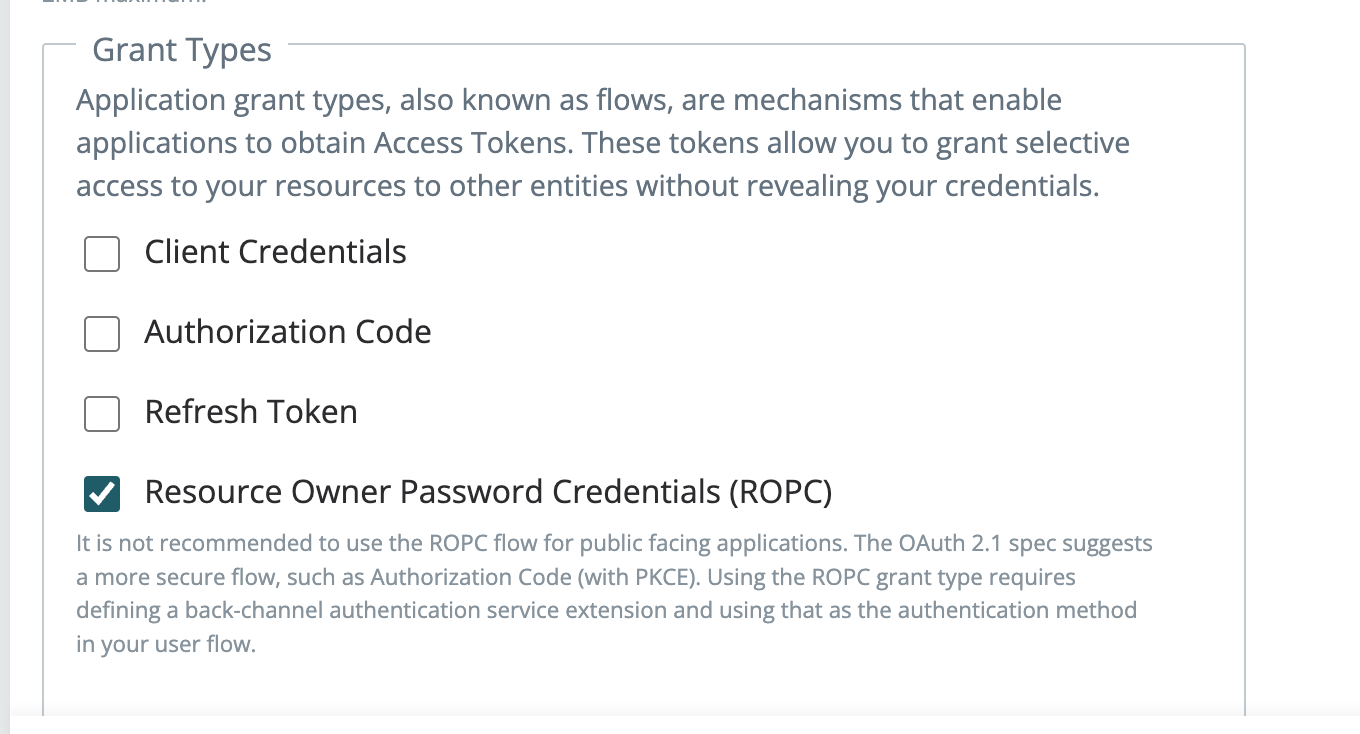
2024-08-15: Resource Owner Password Grant Types (ROPC)
Maverics now supports the Resource Owner Password grant type through a new Backchannel Authentication service extension. This allows Maverics to support OIDC flows that rely on this grant type for highly-trusted clients.
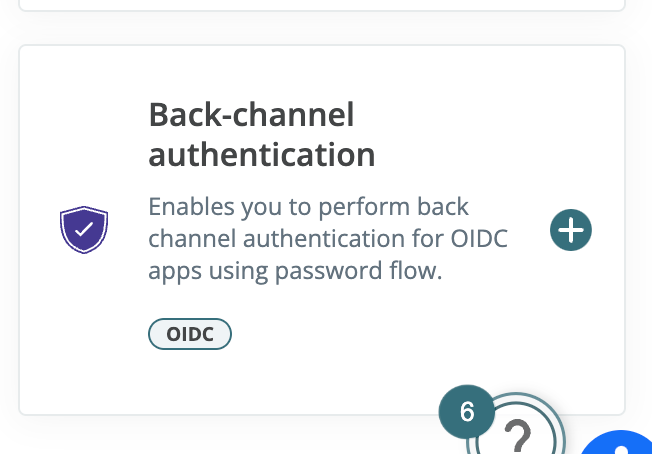
Selectable Grant Types on Application Definition
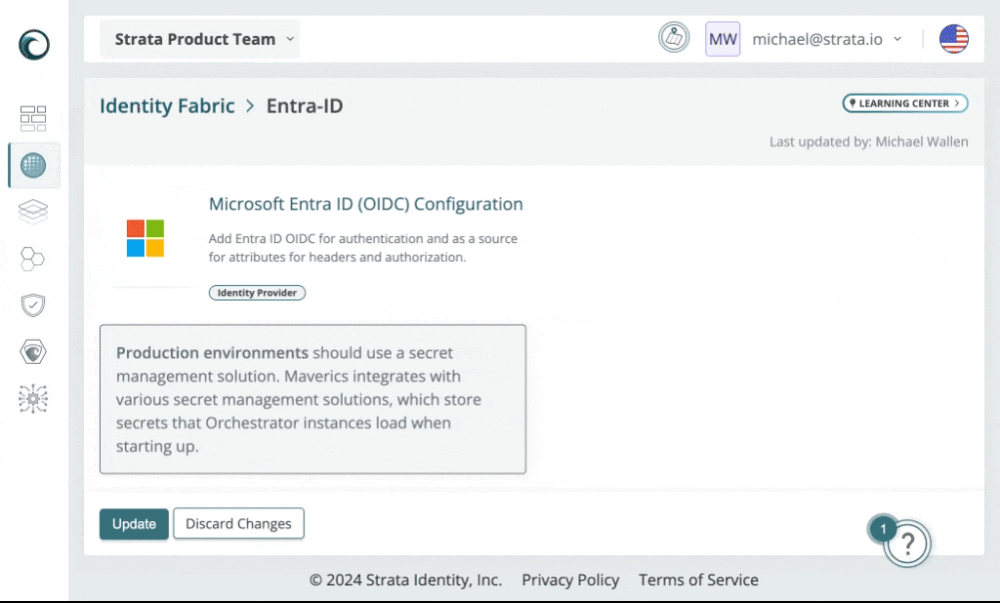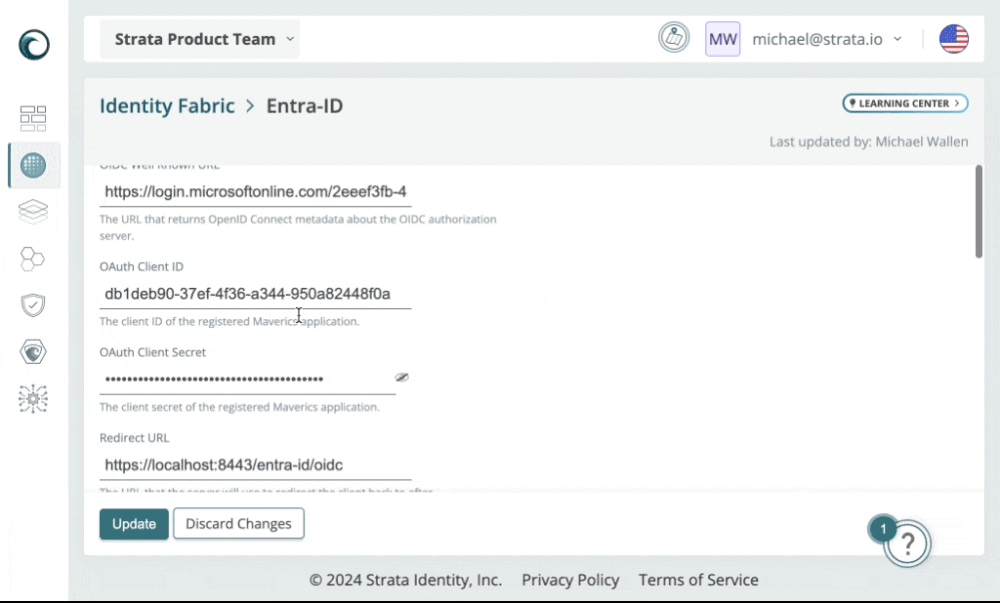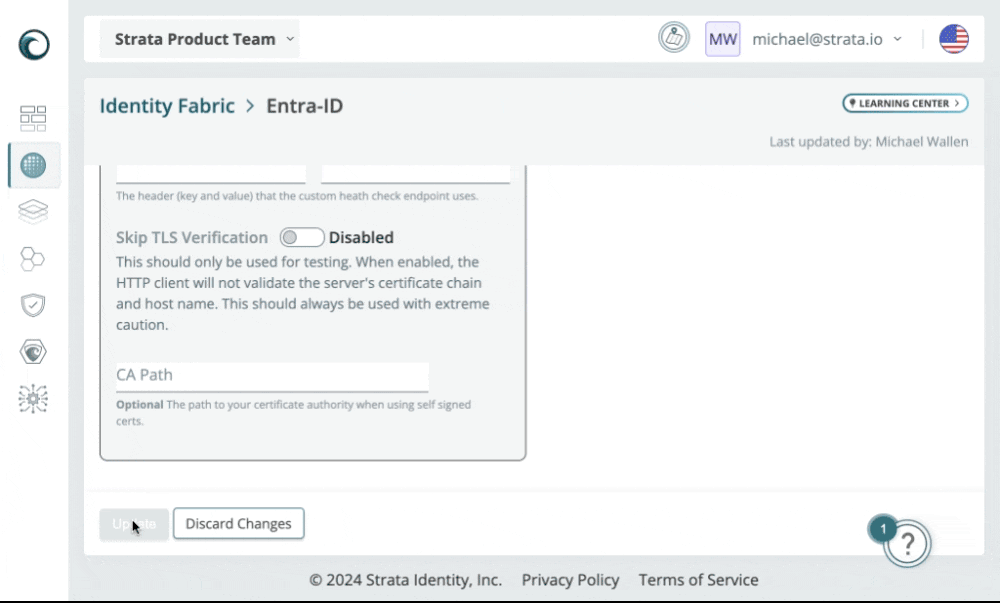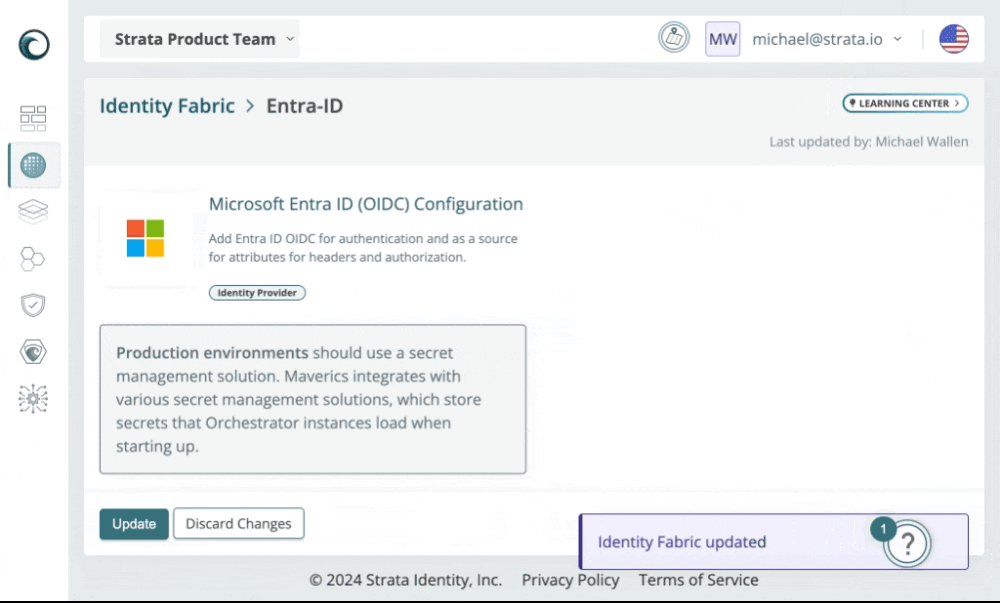
2024-08-12: TLS for custom health checks
You can now specify TLS for custom health check endpoints.
Additionally, when editing full page forms such as Identity Fabric the update and cancel button are now pinned to the bottom of the screen while you scroll for easier access.
Resolved issues
- Selecting OS packages in an API app type are now correctly nesting the config on deploy and will no longer cause the orchestrator to error on startup.
- The click target for providers on custom drop downs no longer requires focus to click.
2024-08-07: Custom health check endpoints, support for isAuthorized SE on SAML app type user flows, French 🇫🇷 translations
Continuity: custom health check endpoints
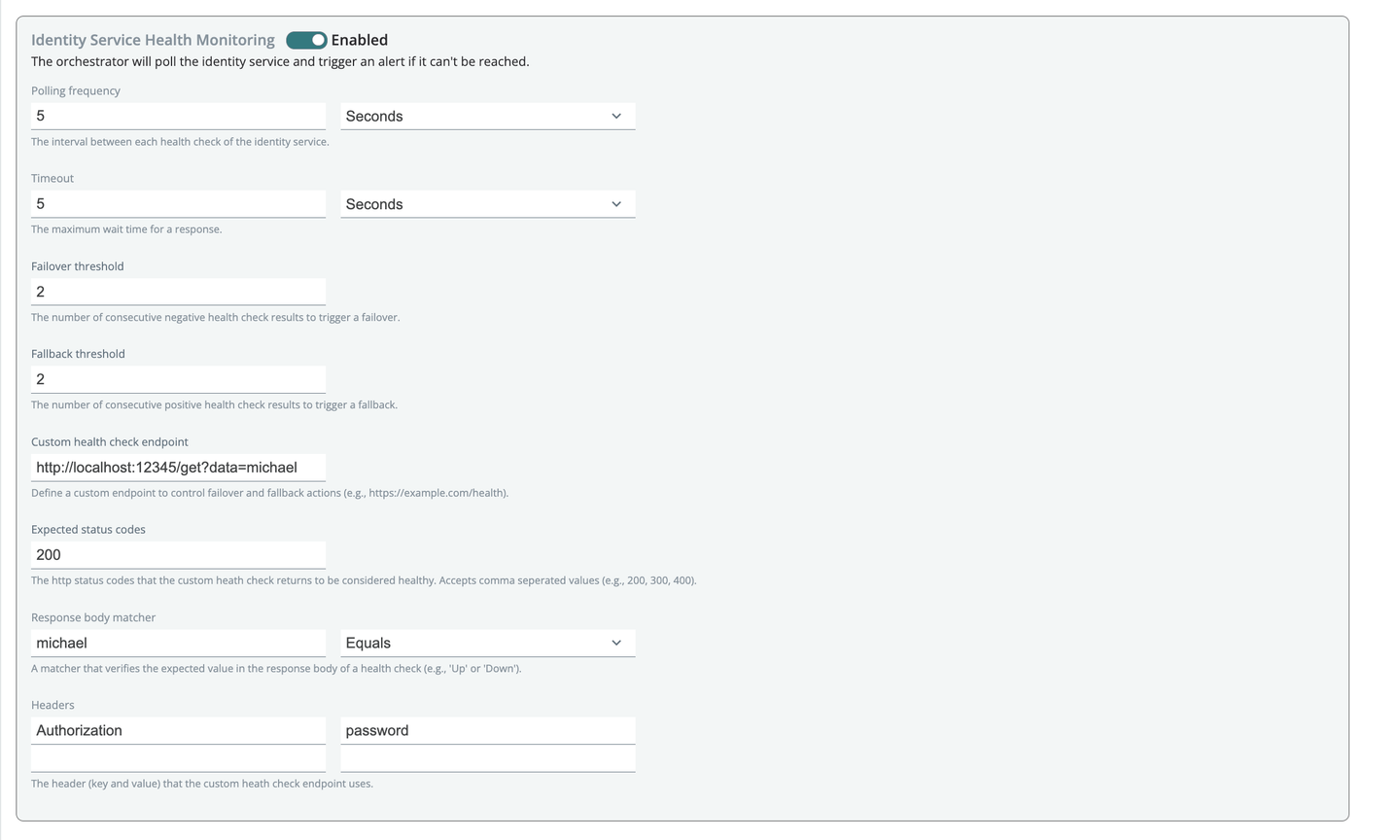
Custom Health Check Endpoints for Continuity enables you override the built-in health check behavior, providing greater control over failover and fallback processes. You can now programmatically mark an Identity Provider (IDP) as down to trigger failover or up to trigger fallback, offering complete control over your identity management processes.
Key Benefits:
- Enhanced Control: Define custom endpoints to control failover and fallback actions based on specific conditions relevant to your operations.
- Customizable Monitoring: Set parameters like polling frequency, timeout, failover (unhealthy), and fallback (healthy) thresholds to meet your unique requirements.
Use Cases:
- Signals, Incident Report and Response Integration: Organizations can leverage their monitoring tools that look at a broader array of internal conditions, such as networking, to manage controlled failover and fallback actions. You can now integrate with platforms like ServiceNow to automate incident reporting and response. For instance, you can configure the events emitted from the orchestrator health check services to trigger automatic tickets in ServiceNow when a failover occurs.
- Disconnected Mode: Utilize custom health check endpoints to manage disconnected mode scenarios effectively. For example, during sea voyages where ships rely on onboard Microsoft Active Directory, custom endpoints can ensure seamless failover to local IDPs, maintaining access even without a continuous connection to primary IDPs.
- Downtime Simulation for Continuity Demos & Testing: Stand up a custom endpoint to manually control downtime simulations. This allows you to test your failover and fallback mechanisms under controlled conditions, ensuring appropriate system responses during actual incidents.
- Compliance and Audit: Utilize custom health checks to demonstrate compliance with regulatory requirements by ensuring continuous monitoring and documentation of IDP health and failover events.
For detailed information on configuration and usage, see our developer documentation and continuity guide.
Other updates
- You can now use a authorization service extension when defining a access policy in a SAML app type user flow. For more information, see Set up a SAML app.
- Simulation settings have been removed from identity service configuration. It is now only available when you deploy a user flow with a continuity strategy.
- The Maverics Console and documentation is now available in French.
2024-08-02: Resolved issues
- You can now specify NameID mapping when using a continuity strategy on a SAML app user flow.
- Policy lifetime settings in proxy app user flows is moved below a rule definition.
2024-07-30: Access tokens and authorization for SAML app type user flows
Maverics Console API
We’ve released a new flow for generating access tokens to use with /register endpoints. This can now be done on the Developer settings page. For more information, visit our new and improved docs for using the Maverics API to automate SAML and OIDC app type user flows.
Additionally, you can now define authorization rules for SAML app type user flows.
Resolved issue
- User flow errors are now more clear and include discoverable tool tips.
Known issues
- Currently you are unable to delete access tokens.
- Orchestrator logs do not contain authorization policy event as they do for proxy apps.
2024-07-22: SAML app onboarding POST API
The new /register/saml endpoint allows you to set up a new SAML application or Service Provider (SP). This endpoint facilitates the automation of onboarding and deployment of SAML app user flows, streamlining the integration process.
For more information, see Use the Maverics API to automate deployments.
Resolved issues
- “Microsoft” has been prepended to all Microsoft fabric items as per Microsoft brand guidelines.
- Added support for additional orchestrator session settings in environments: cache size, cookie settings.
2024-07-18: Resolved issue
- NameID format settings on SAML fabric types are saved upon update and will persist empty on deploy.
2024-07-16: Resolved issues
- The Calendly onboarding widget will now appear in account sign-up.
- The prompt to save edits before navigating away will appear in more places where you need them (for example, when editing identity fabric), and less when you don’t want them (for example, when you delete list items).
2024-07-15: Bug fixes
You will now be prompted by the browser if you make an edit to a user flow and have not otherwise confirmed your changes.
Resolved issues
- Publishing a new deployment to a GitHub repo no longer results in an error.
- Validation on service extension metadata field now prevents you from entering empty keys and values.
- Service extension fields now have descriptions.
- When the Telemetry option is disabled, both metric and health fields are also disabled.
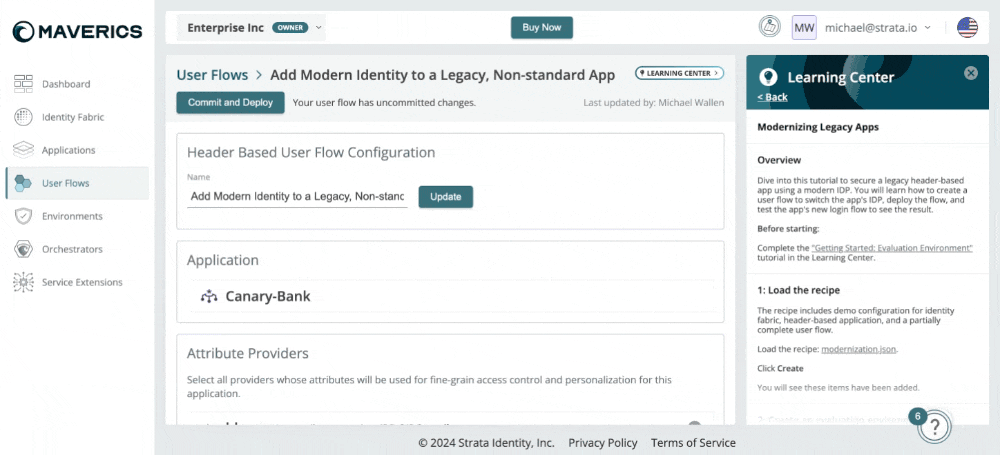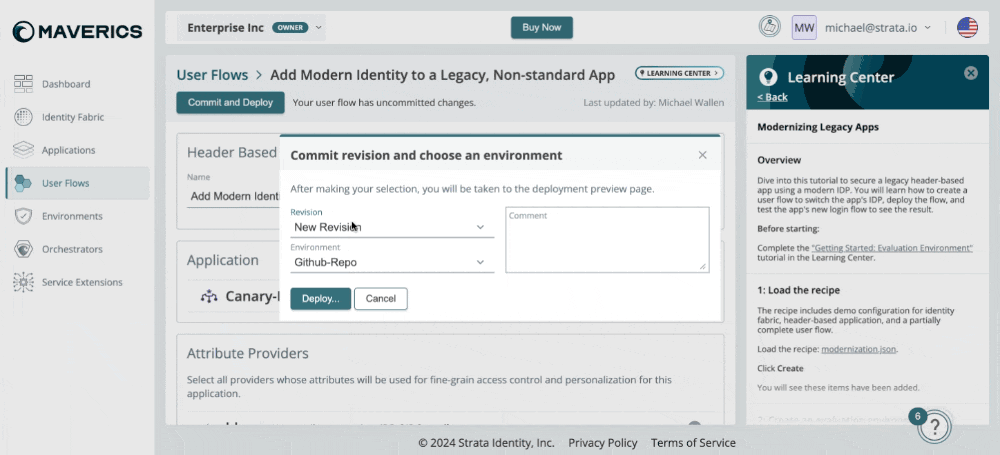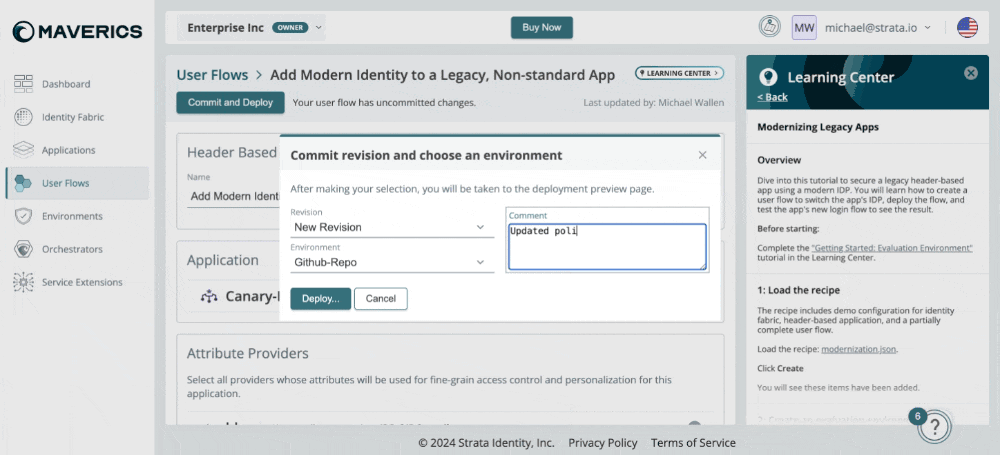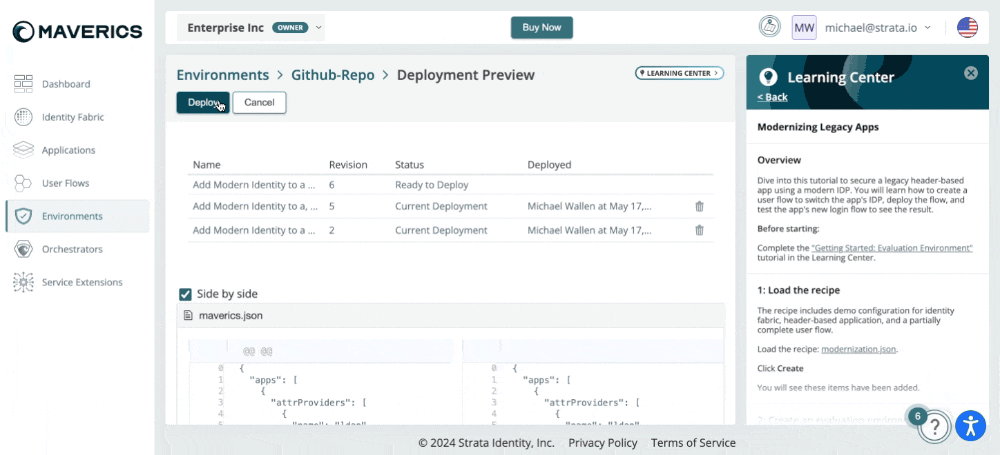
2024-07-03: Commit and Deploy
Commit and deploy can now be done with one action! The modal has been improved with the following updates:
- Commit a new revision to deploy
- Larger text area to add commit comments
- Deploy a previous revision
Resolved issues
- We’re excited to share today’s update, where we’ve squashed numerous bugs to enhance usability and improve your overall experience.
2024-07-01: Bug fixes
You can now navigate and enter data with a keyboard into fields in the headers, claims, and attribute mapping tables.
Resolved issues
- Disabled submit buttons after clicking to prevent duplicate requests (account creation and import)
- Fixed an issue where IDP config was not being updated on deploy when used by two different user flows.
- Fixed an issue where importing a SAML app type user flow was not being deployed.
- PKCE toggle on OIDC based IDPs is now persistent.
- Fixed several issues related to using the browser back button.
Known Issues
- When performing SP-initiated SSO and authenticating with an Entra OIDC IDP, the orchestrator inserts the SAML Request in the state parameter. This parameter is rejected by the Entra ID IDP due to its size. We are currently working on a resolution.
2024-06-20: Service Extension Policy Lifetime
You can now specify when policies for proxy app type user flows will be re-evaluated by service extensions. This requires updating your orchestrator to v0.27.42 or higher.
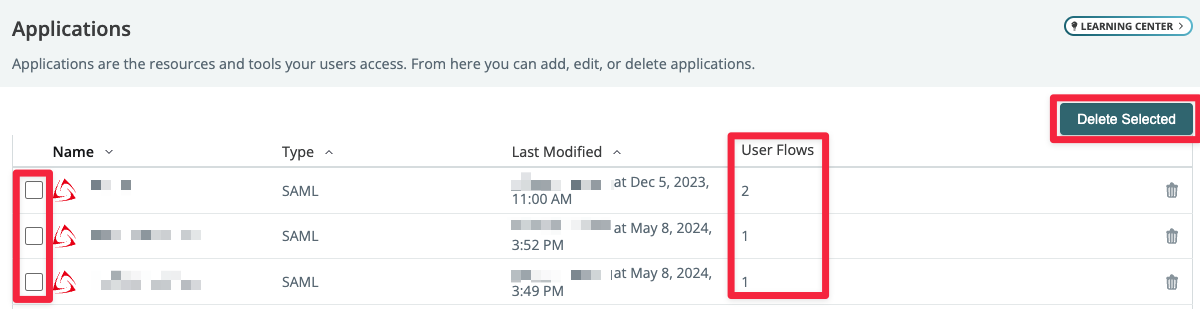
2024-05-17: List view improvements
Introducing batch actions on list views! You can now multi-select items and delete from lists on the Applications, Identity Fabric, Environments, and User Flows pages. Additionally, on Applications and Identity Fabric lists, you can view the count of user flows associated with the object.
Resolved issue
- If an environment is configured with a token that has incorrect permissions, it will now show you the correct error message when it fails to deploy.
2024-05-10: Single Logout (SLO) for SAML
You can now define a single logout (SLO) URL in SAML apps.
Resolved issues
- Orchestrator telemetry graphs are now rendering properly.
- You can import app type user flows that define a Relay State Service Extension.
- Orchestrator Release - v0.27.24 - hot reload fixed for SAML app user flows.
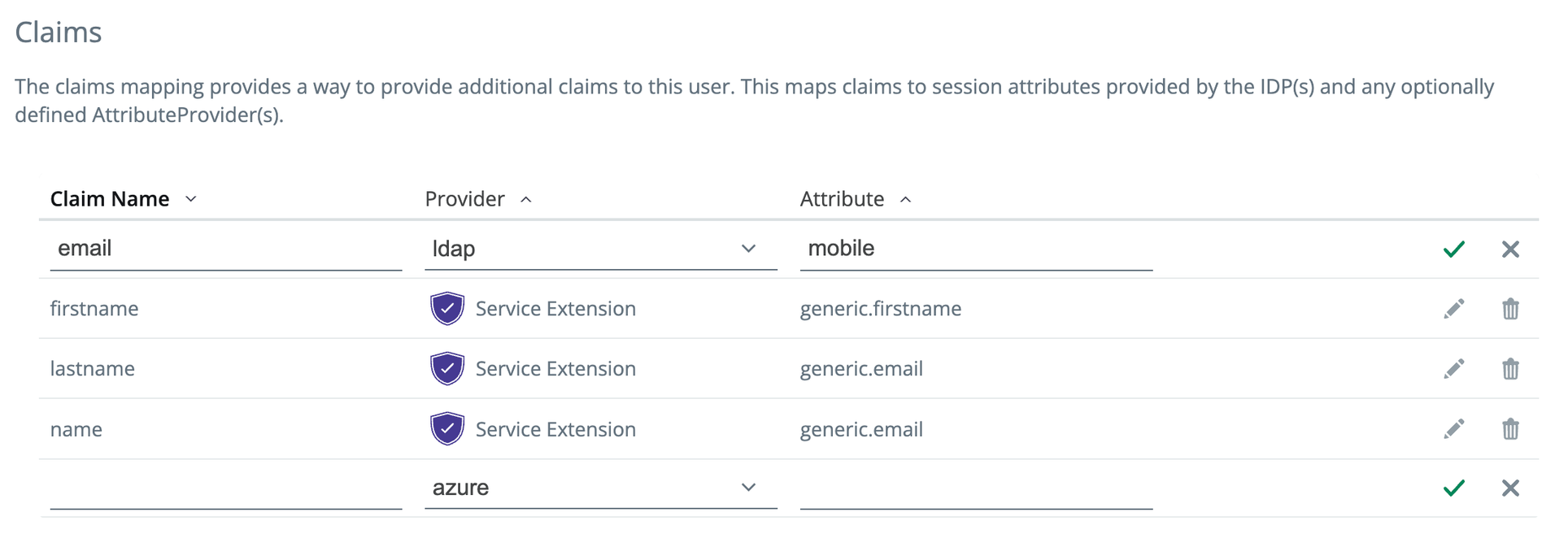
2024-05-07: New editors
New editor for claims and headers
You can now add, edit, and delete claims for SAML & OIDC app user flows, and headers for Proxy app user flows.
API app type uses the new Service Extension editor
The API app type editor has been upgraded to use the new Service Extension editor.
2024-05-07: Updated Windows installer
Our new orchestrator installer for Windows makes it easier to set up and configure your storage and variables. You can find the Windows installer for download by going to Environments, selecting one of your environments, and clicking Windows in the Orchestrator section.
For step-by-step instructions on installing the orchestrator on Windows, see Install on Windows Server.
2024-05-02: Editing headers and batch actions
You can now edit headers inline, as demonstrated below!
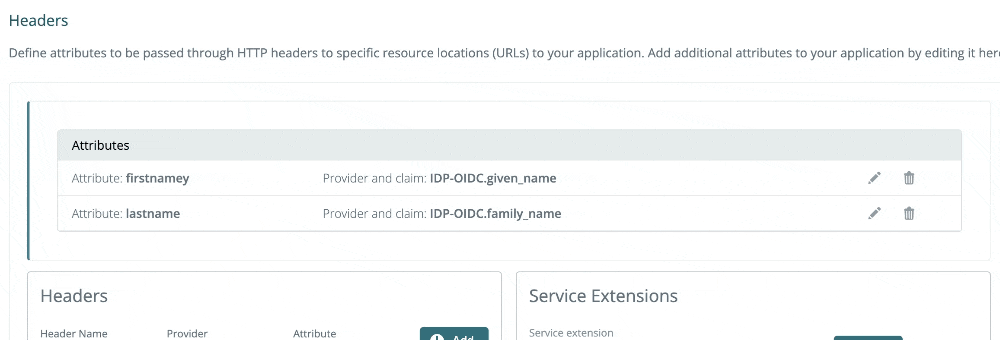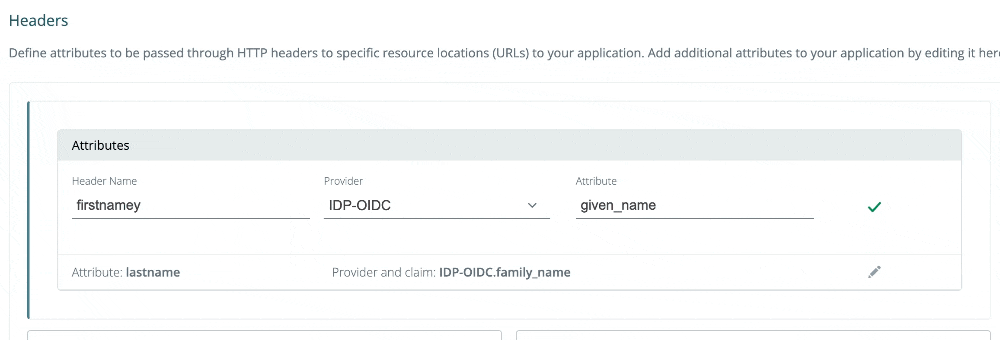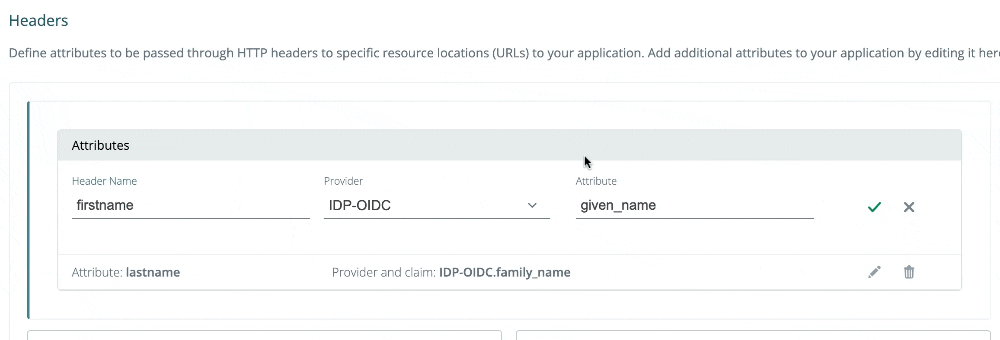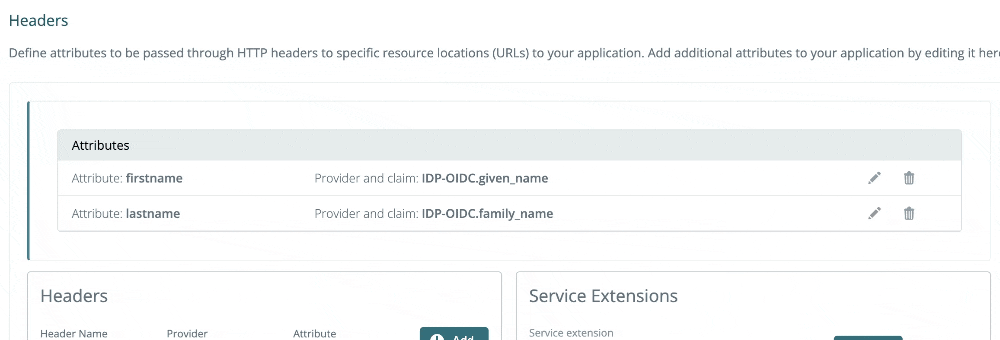
We are also gradually rolling out batch actions on list views. Today, in the Applications list view, you can multi-select applications and delete. This feature is coming soon to other list views.
Resolved issues
- Fixed line height clipping in service extension settings.
- User Flow list title now renders correctly.
- Build Relay State SE: the configuration has been corrected and is removed properly when deployed with a SAML app type user flow.
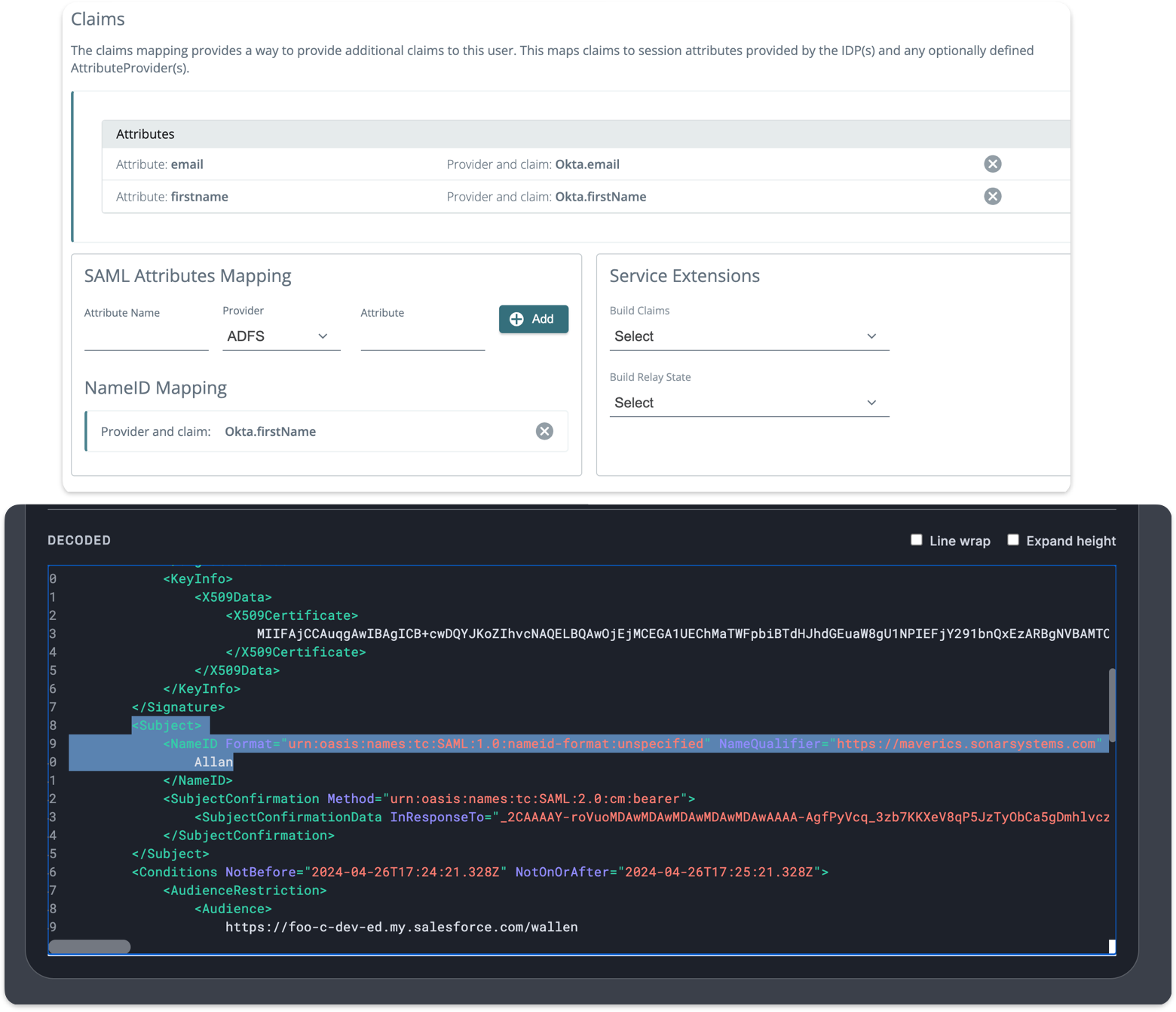
2024-04-26: NameID mapping for SAML user flows
When using Maverics as a SAML identity service, you can now define custom NameID mappings in SAML responses. This new feature enhances interoperability and ensures seamless integration with different identity providers (IDPs) and service providers (SPs).
Benefits
- Increased Flexibility: Customize SAML assertions to align with unique requirements of service providers and IDPs.
- Improved Integration: Ensure compatibility and ease of integration with third-party services, which may require specific NameID formats.
- Enhanced Control: Gain precise control over user identity attributes shared during the SSO (Single Sign-On) process.
- Streamlined Identity Management: Simplify the management of user attributes across different platforms, reducing administrative overhead.
To create a NameID mapping:
- Follow our user guide to create a SAML user flow.
- After creating the user flow, open the user flow and find the NameID Mapping section under SAML Attributes Mapping.
- Select a provider and define the attribute you want to define. Click Add.
- Re-deploy the user flow, and test the login with a service provider. To verify that the NameID mapping is working correctly, use your browser’s developer tools to view the SAML response.
Resolved issues
- Service extension settings updates were not being deployed.
- Service extensions that are added to user flows now have a common look and feel.
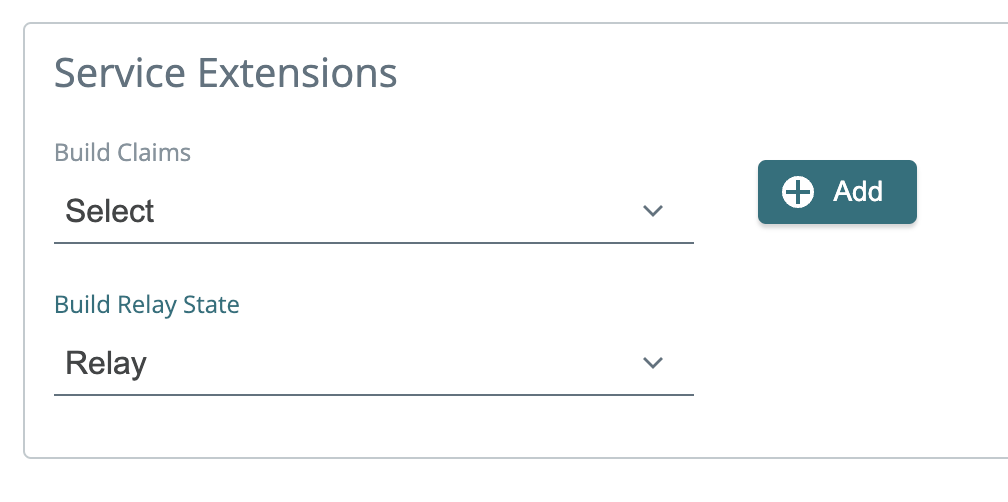
2024-04-23: Build Relay State SE, service extension experience, and docs updates!
Build relay state service extension
The dynamic RelayState URL for SAML app type user flows can now be customized with the Build Relay State Service Extension. This extension enhances the flexibility and user experience of Single Sign-On (SSO) processes by enabling customizable redirections post-authentication.
Key highlights:
- Feature overview: Allows for dynamic customization of redirection URLs after user authentication, maintaining seamless user states.
- Target application: Specially designed for SAML app type user flows to dynamically direct users based on their roles or initial access contexts.
- Customization capabilities:
- Personalized user redirects: Directs users to role-specific or contextually appropriate URLs immediately after login.
- Flexible application integration: Easily integrates into existing SAML workflows for tailored navigation based on predefined criteria.
To use:
- Follow the guide to create a SAML app user flow.
- Go to service extensions and click Relay State from the list on the right.
- Add your own or customize the example code.
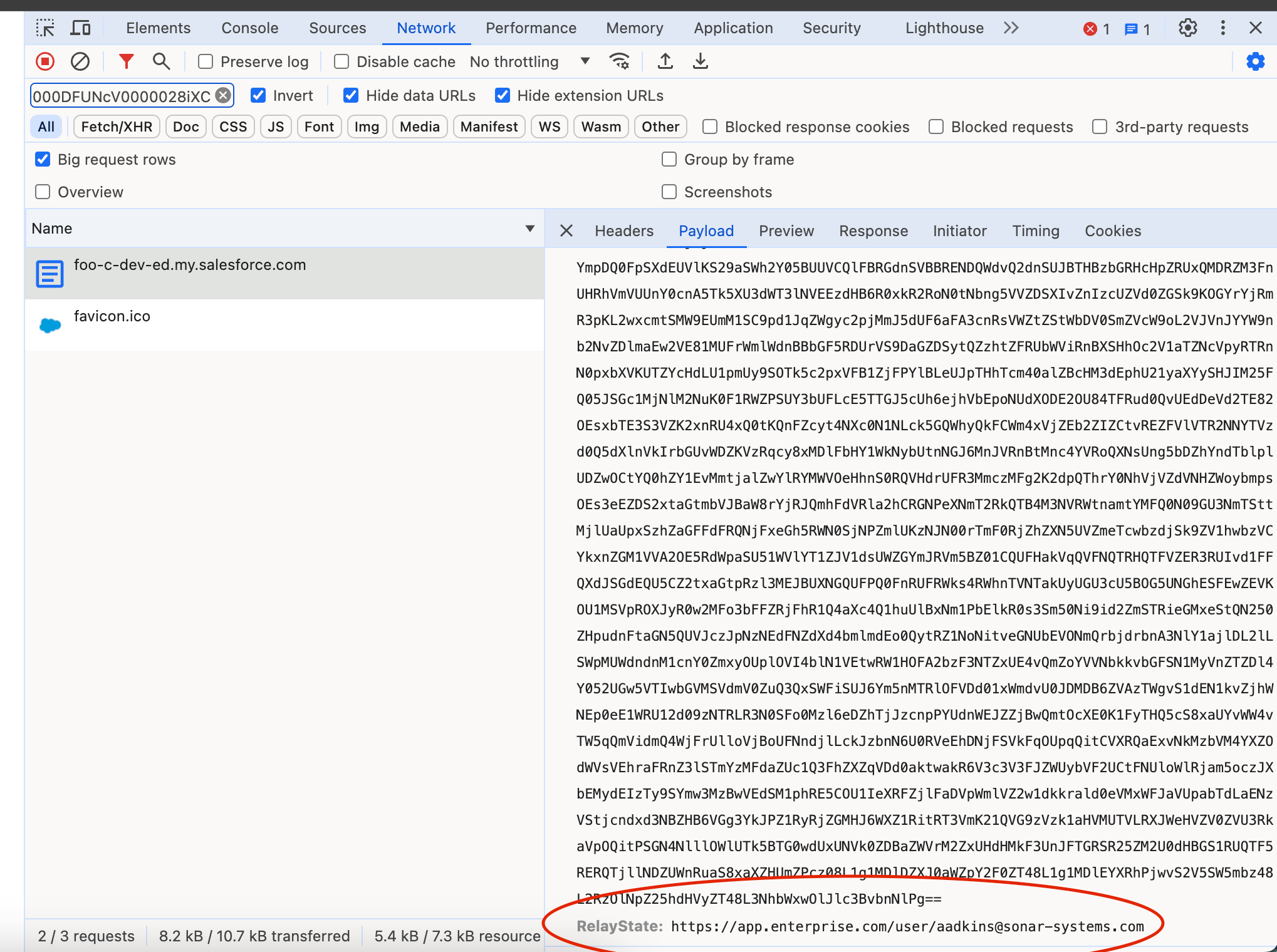
- Open a SAML app user flow and scroll to the bottom to the service extension area. Under Build Relay select the service extension you created in step 2. This service extension will override the relay state URLs defined in the associated SAML app definitions.
- Deploy the user flow.
- To try the user flow, start an IDP initiated login flow to your application. Open the developer tools in your browser and from the network tab, inspect the SAML payload.
Improvements with the service extension experience
Our new editor is out of preview and now available to use. Improvements include:
- Larger code editing.
- Faster return of compilation errors
- Upload, view, and edit (non-binary) assets to use with your service extensions.
These improvements are not yet available for editing API app type (ServeSE).
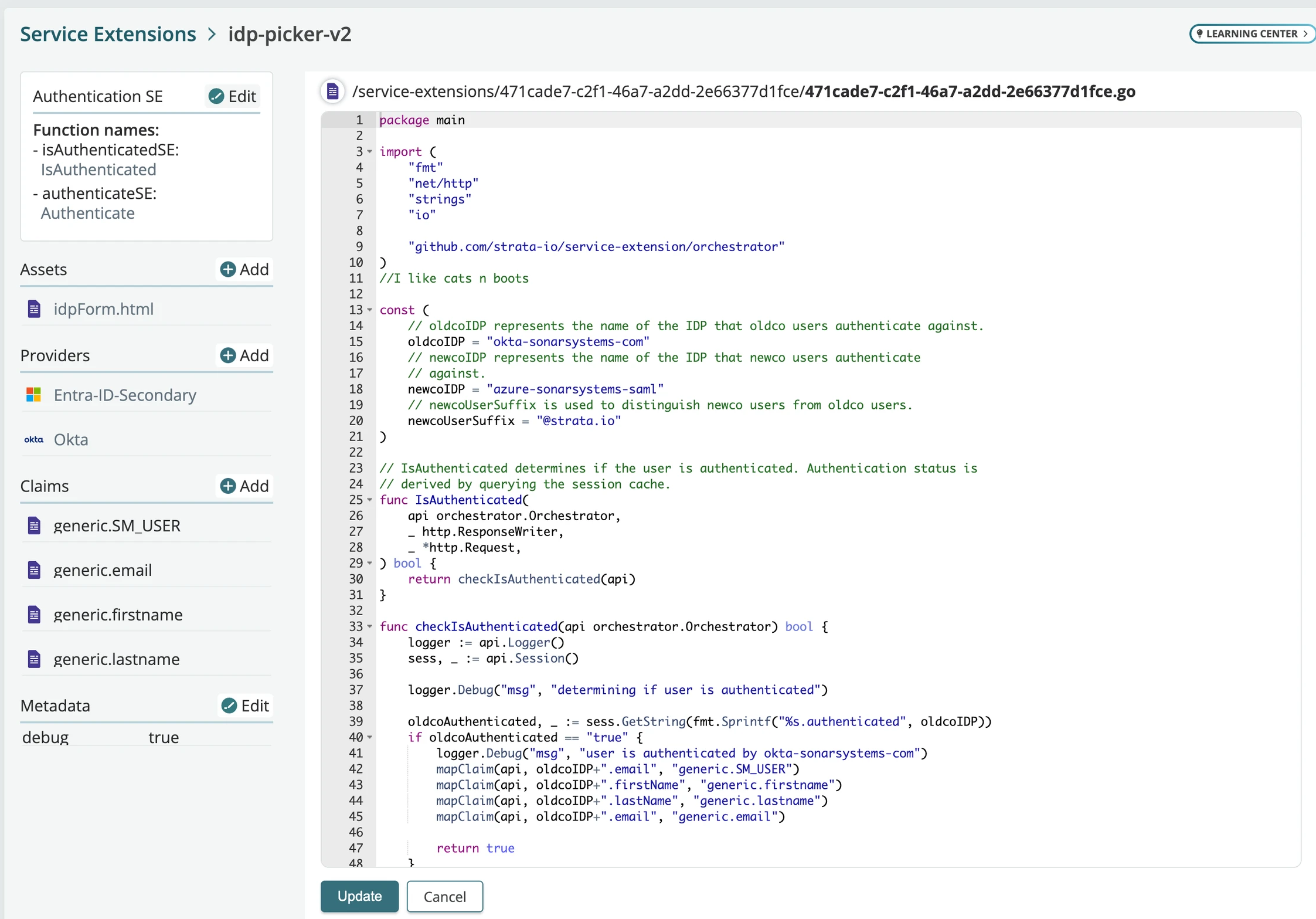
Additionally, the service extension list is now reordered and tagged by app types supported (All, Proxy, SAML & OIDC, SAML).
New documentation improvements
We have new guides to walk you through the end-to-end process of deploying proxy, SAML, and OIDC user flows.
Additionally, you can now browse docs and release notes from the Resource Center. Click the question mark icon in the lower right corner of your screen for access.
Resolved issues
- Keycloak fabric now has the correct
oidctype set on deploy.
2024-04-19: Service extension editor fix
The service extension editor will now show errors when attempting to compile malformed code.
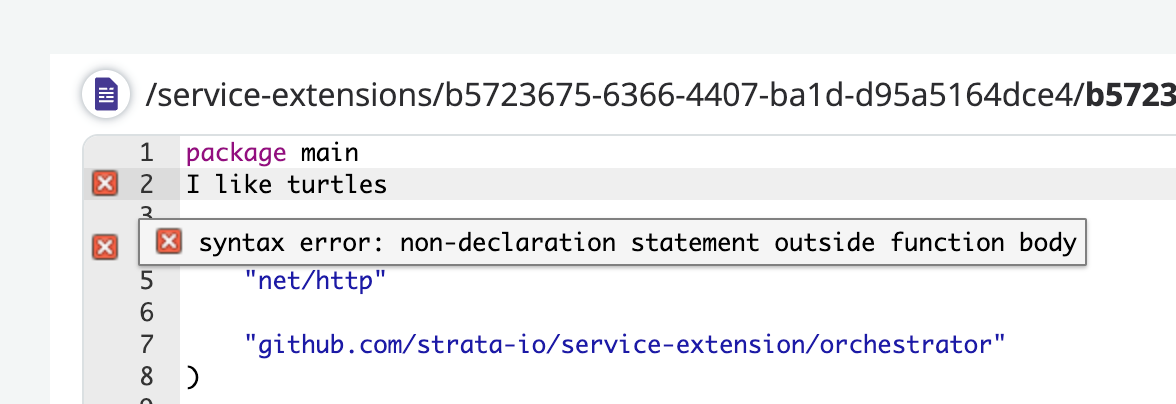
2024-04-17: Restrict access by http request methods for modernizing header based apps
By restricting certain operations (like DELETE or PUT) to only authorized users based on their HTTP method, Maverics helps in mitigating potential security risks such as unauthorized data modification or deletion.
Granular Access Control: Maverics now allows administrators to define access policies for modernizing header based apps that are specific to the HTTP methods used in requests, such as GET, POST, PUT, DELETE, etc. This granularity enables more precise control over how resources are accessed depending on the action being performed.
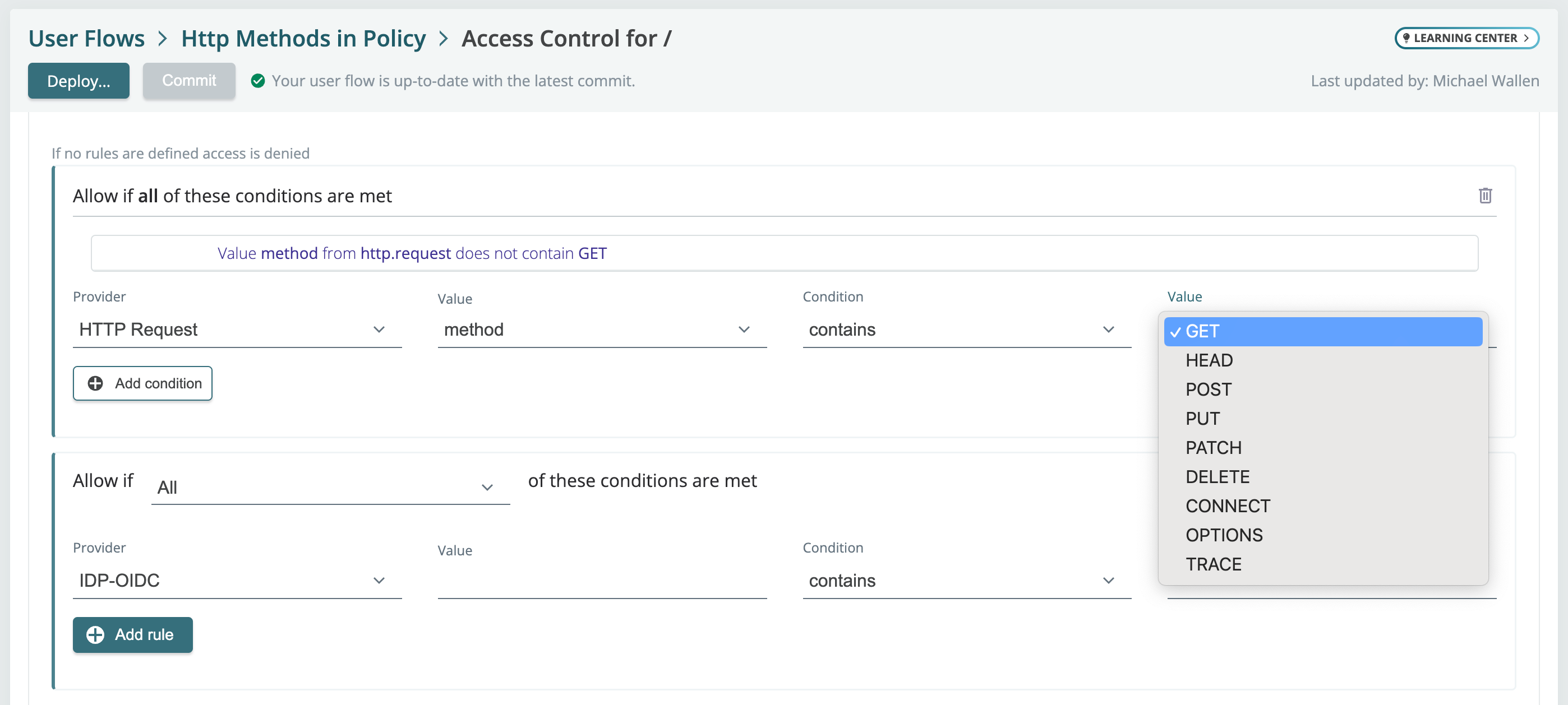
Condition-based Policy Definition: When setting up location policies in Maverics, you can specify the HTTP method in the authorization rules. This means you can create different access rules for reading a resource (using GET) versus modifying it (using POST or PUT).
2024-04-16: Fit and finish updates
Country flags now display when selecting a Maverics region.
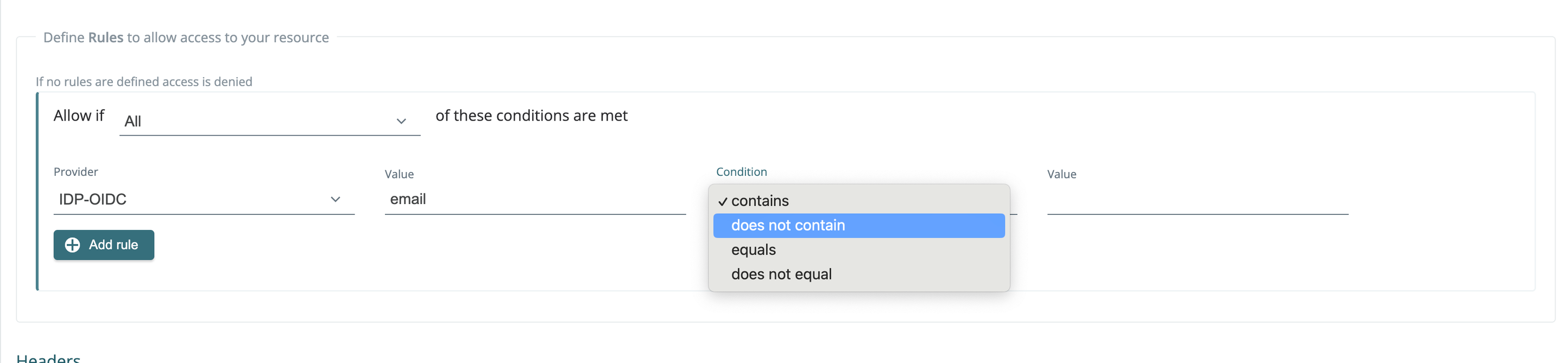
Additionally, when defining a rule in a location policy, you can now select does not contain or does not equal.
Resolved issues
- You can now delete a header and add a header back with same name to a location policy without an error.
- A location policy page will render properly when adding a header service extension.
2024-04-10: UX updates and bug fixes
We’ve updated toggles to enable IDP initiated login on SAML fabric types, and to enable PKCE for OIDC fabric types.
Resolved issues
SameSite=Laxis now properly set on login call back cookies.- When you deploy a Proxy App type with an Upstream Login service extension, the service extension is now properly nested under upstreamLogin.
- In SSO flows, email addresses are no longer case sensitive. (For example, if an IDP sends
[email protected]and[email protected], these accounts will be treated as the same user, and the user will not be prompted to create a new account). - OIDC fabric types will no longer show blank default values for scopes.
2024-04-04: Service extension fixes
Resolved issues
- You are now prevented from deleting service extensions that are referenced in a user flow.
- Adding a Create Header service extension will no longer render incorrectly.
- You can now delete service extensions that have assets.
2024-03-25: Fit and finish, and feature enhancements
- Added Entra ID & Okta (OIDC) health check preferences for interval and time in seconds.
- Hover legends, graph smoothing, scaling, request counts with response codes, and improved behavior and accuracy for orchestrator telemetry.
- You can now select a provider or static when defining headers in a user flow.
- You can now add headers when creating/editing user flows in Safari.
2024-03-19: Resolved issues
- When you import service extensions now the providers are included in the import.
- Continued fit and finish to orchestrator telemetry and graphs.
- Fixed an issue where in regions outside of the U.S. the deprecated header app types were available and the incorrect fabric options were showing.
2024-03-15: Telemetry chart update
New charts have been added with hover tips to reflect data points.
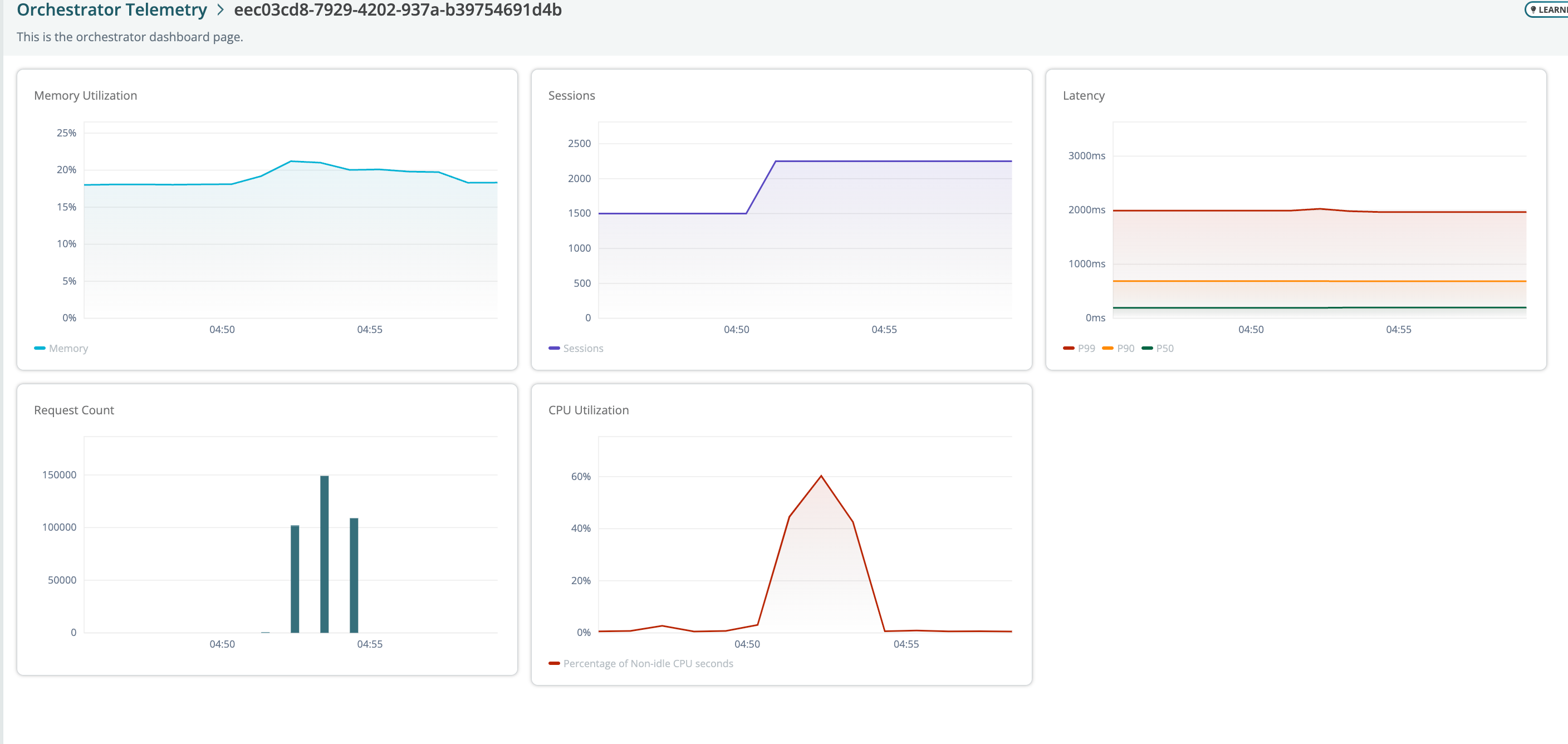
Resolved issue
- Importing a bundle with a service extension now supports importing the metadata.
2024-03-08: Support for .tar.gz bundles
You can now import *.tar.gz bundles that contain service extensions with assets.
2024-03-07: Orchestrator settings in Environments
When updating Orchestrator settings in Environments, you must manually restart your orchestrators in order for the changes to take effect. We’ve added a banner to remind you to start your orchestrators on the edit section. We’ve also improved the description for the Orchestrator URL setting.
2024-03-06: Fix for API app type updates
Fix for duplicate service extensions (SEs) not included in a deployment bundle
This issue corrects a scenario in which a deployment that contained two user flows referencing the same service extension resulted in (“…Service Extension: unable to read file…”) in the orchestrator logs. In order to correct the bundle, you need to do one of the following:
- Go to the environment and click “Redeploy" OR
- Commit and deploy the new user flow.
With this release, new deployments and re-deployments will generate a bundle that includes the duplicate SEs.
2024-03-01: Support for upload/deploy of binary assets in service extensions
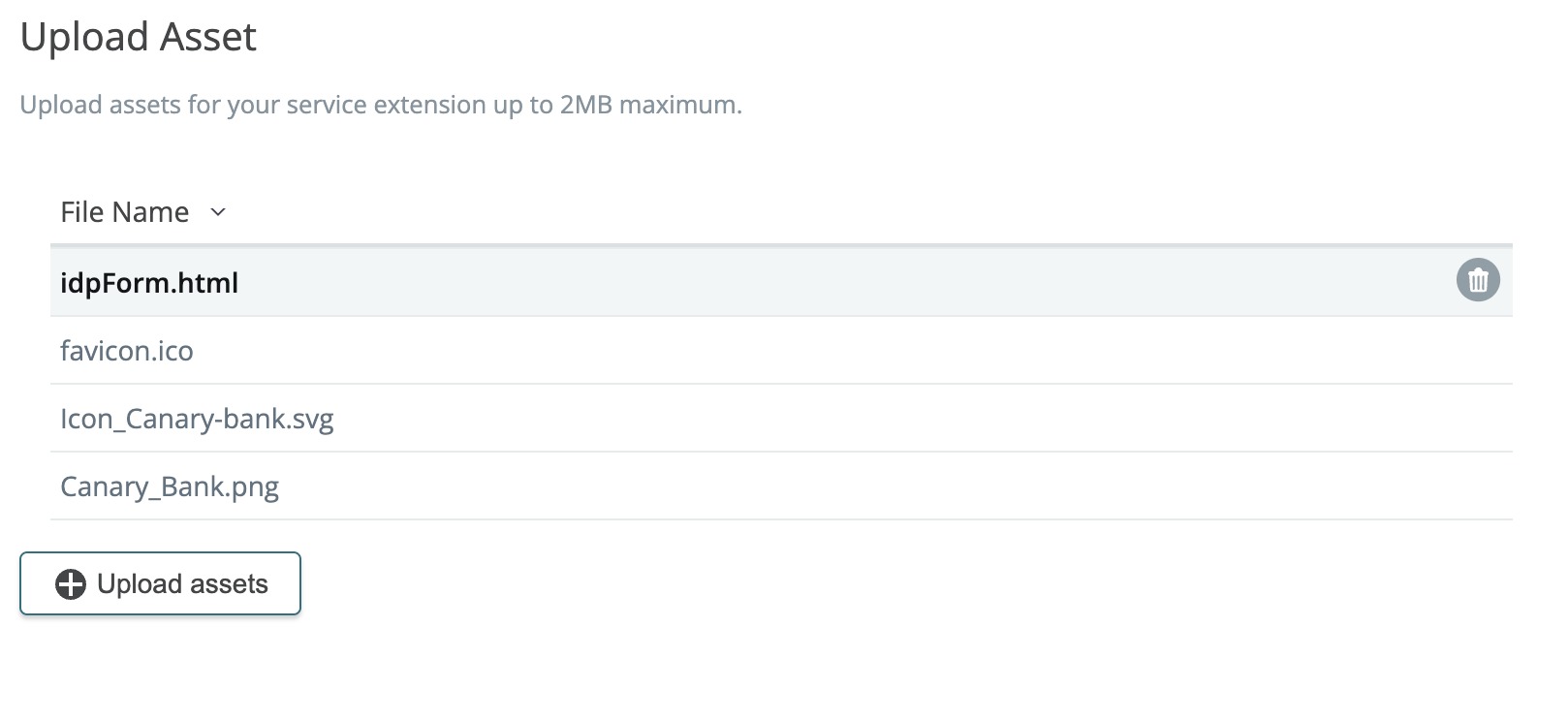
You can now upload and deploy binary file types as assets with your service extensions. These assets can be used for API app types.
Known limitations
- The user flow list may appear slower to render when including references to service extensions with assets.
- Import does not currently support bundles that include service extensions with assets.
2024-02-29: Service extension assets and a fix for SE metadata updates
You can now upload and deploy assets that can be used as ancillary resources in your service extensions.
Resolved issue
- Updates to service extension metadata are now properly deployed.
2024-03-08: Support for .tar.gz bundles
You can now import *.tar.gz bundles that contain service extensions with assets.
2024-03-07: Orchestrator settings in Environments
When updating Orchestrator settings in Environments, you must manually restart your orchestrators in order for the changes to take effect. We’ve added a banner to remind you to start your orchestrators on the edit section. We’ve also improved the description for the Orchestrator URL setting.
2024-03-06: Fix for API app type updates
Fix for duplicate service extensions (SEs) not included in a deployment bundle
This issue corrects a scenario in which a deployment that contained two user flows referencing the same service extension resulted in (“…Service Extension: unable to read file…”) in the orchestrator logs. In order to correct the bundle, you need to do one of the following:
- Go to the environment and click “Redeploy" OR
- Commit and deploy the new user flow.
With this release, new deployments and re-deployments will generate a bundle that includes the duplicate SEs.
2024-03-01: Support for upload/deploy of binary assets in service extensions

You can now upload and deploy binary file types as assets with your service extensions. These assets can be used for API app types.
Known limitations
- The user flow list may appear slower to render when including references to service extensions with assets.
- Import does not currently support bundles that include service extensions with assets.
2024-02-29: Service extension assets and a fix for SE metadata updates
You can now upload and deploy assets that can be used as ancillary resources in your service extensions.
Resolved issue
- Updates to service extension metadata are now properly deployed.
2024-02-23: Bug fixes
Resolved issues
- You are no longer able to set an evaluation environment for Production use.
- Proxy apps that contain rules in access policies can now be imported and displayed properly.
2024-02-20: Fix for environments and enhancements
In a proxy app user flow, you can now select a service extension in an access policy rule and use the claims defined in the service extension.
Instances of Azure AD have been updated to Entra ID (per Microsoft branding updates).
We’ve also improved consistency and clarity to identity fabric card names and descriptions.
Resolved issue
- Fixed an issue that prevented users from being able to create or edit an existing environment
2024-02-15: Canary Bank and service extension deployment improvements
All five of our Learning Center recipes have been updated to use Canary Bank instead of Sonar. This update also includes clearer names of imported fabric, apps and user flows.
Service extension snapshots created when deploying user flow revisions
When you commit and deploy a user flow, a snapshot of the service extension code is saved with the revision. This enables you to roll back to that snapshot when you deploy a previous revision.
If you deploy multiple user flows that reference an updated service extension, all of them must be committed and showing a status of “Up-to-date” to get the updated SE.
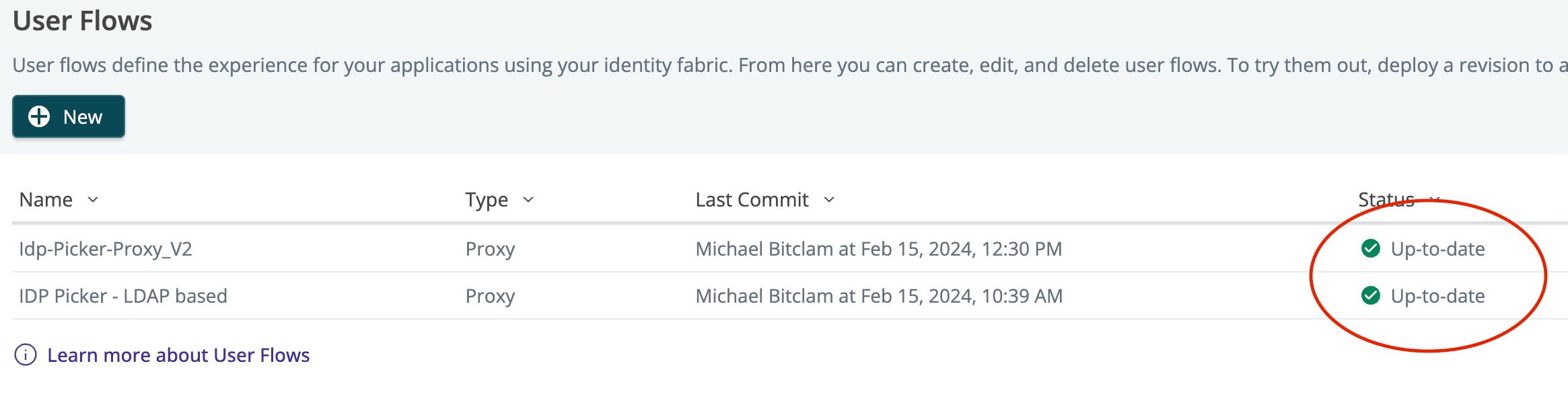
Resolved issues
- Attribute providers can now be more reliably be selected when creating an access policy rule in a proxy app type user flow.
- On import, you are now required to add environment name when selecting local or eval environment.
2024-02-12: Resolved issue
The previous release included a change that moved service extensions into subdirectory in the deployed bundle. The deployed JSON config did not include this path and resulted in an error on Orchestrator startup where the service extension could not be found. We’ve introduced a fix to incorrect SE subdirectories in bundle and config paths. With this fix you can now re-commit/deploy user flows with service extensions.
2024-02-08: CyberArk now available in Identity Fabric
You can now add CyberArk as an IDP to your identity fabric. You can use a either a SAML or OIDC connection to CyberArk’s Workforce and B2B identity offerings with Maverics. Follow the new Learning Center guide to get started.
We’ve also updated descriptions in user flows to read more clearly.
We made some behind the scenes fixes so you can now import/export proxy app type user flows that contain location policies with rules. However when importing, they do not appear on the policy page.
2024-02-06: Bug fixes
- We’ve resolved an import issue where bundles that contain a combination app types and service extensions would fail to import.
- We’ve also resolved an issue where evaluation bundle content (for example, maverics.env) was malformed while an eval environment was being created asynchronously. Now, access to certain actions are safely disabled while the eval environment is being created, and a status is shown as “Creating environment.” Wait a few moments before refreshing the page, and the actions will be made available again.
2024-02-04: Regex bug fix
- We’ve added a fix for regex location policy names with a backslash character.
2024-02-02: Fit and finish updates
- Some error messages will be displayed to user due to environment misconfiguration when deploying configuration.
- An additional inspection warning has been added to user flow configuration and deployments to catch some common configuration errors.
- Applications can no longer be removed if they’re attached to a user flow.
- All list views now use the updated design.
Resolved issue
- Fixed a panic due to invalid configuration that resulted in a Cloudflare error page.
2024-01-29: New Learning Center lesson for Microsoft Entra ID and other improvements
Click the Learning Center icon in the upper right side of the Maverics screen to find our new lesson, Extend Microsoft Entra ID to Legacy, Non-Standard Apps. You will need access to an Entra ID tenant to integrate and create a test user for the login flows.
New list views
List views have a new easily selectable and sortable look and feel.
Updated default list for access policies
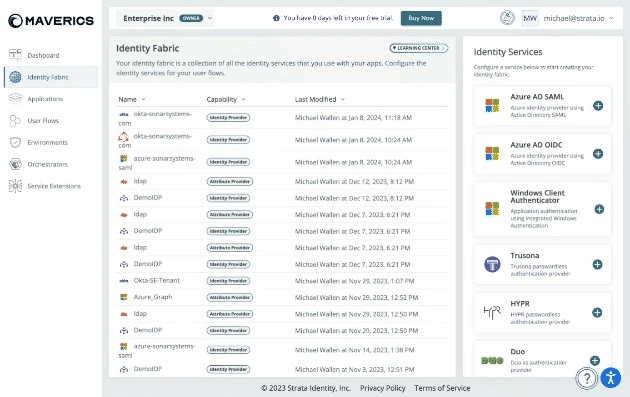
Previously, new location policies would default to an invalid policy that would cause an orchestrator to error and fail to start up. Now, when a new policy is added you must select a valid authentication (allow unauthenticated, require auth by IDP, or service extension) and authorization policy (allow all access, use a rule, or service extension).
Evaluation environment improvements
- Users can now only have one evaluation environment at a time.
- Creating an evaluation environment is now faster.
- Using port :443 for Linux eval was a problem because it was a reserved port. Now the default port for evaluation content and lessons has changed from :443 to :8443.
- maverics.env file has been updated to use :8443
- Learning Center demo urls and identity fabric definitions have been updated to 8443
2024-01-19: Single Sign On (SSO) for accounts
Account owners can now secure access to their Maverics accounts with single sign on! View our documentation here.
User flow deployments
When you deploy a user flow you now have the ability to preview everything in a deployment bundle. This includes other user flows deployed to the environment, orchestrator configuration specific to that environment and any service extensions.
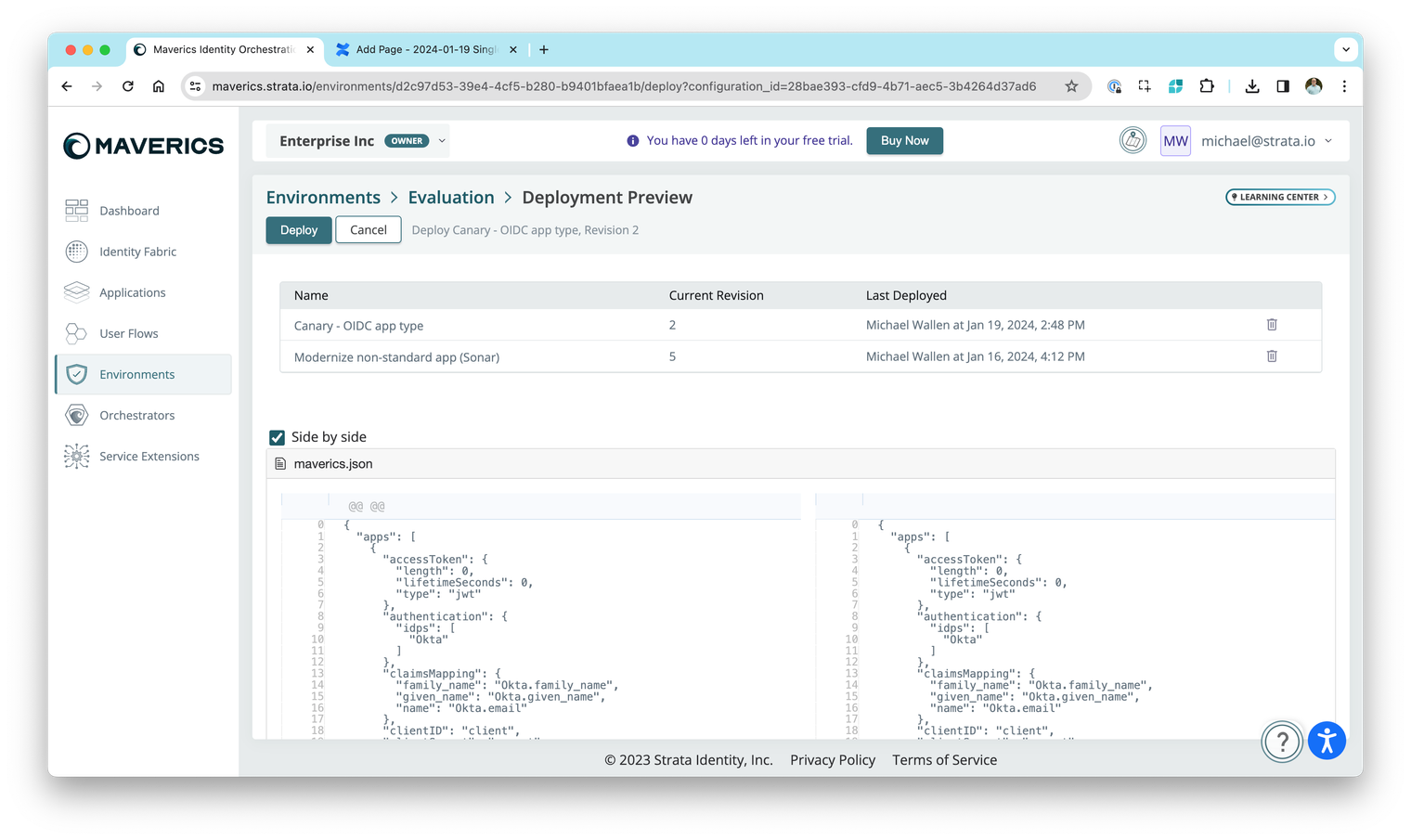
Resolved issues
- You can no longer mark an evaluation environment for production.
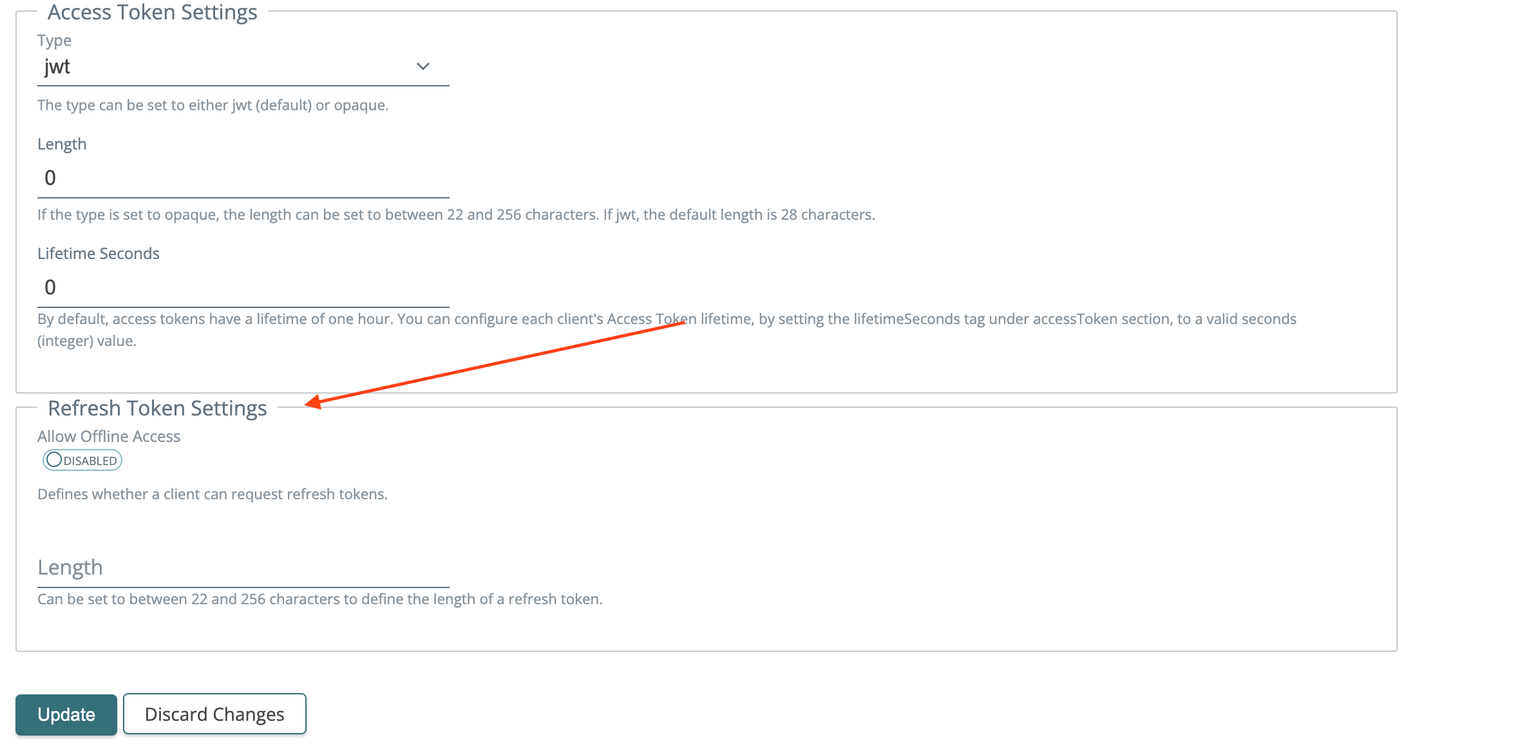
2024-01-02: OIDC app refresh token settings
When defining a OIDC app type you can now specify refresh token options.
2023-12-20: Optional fields for SAML-based identity fabric, cache config fixed
We’ve updated Azure SAML, ADFS, Duo and Generic SAML fabric by adding SP Cert Path/Key, Name ID Format, and IDP-initiated login options.
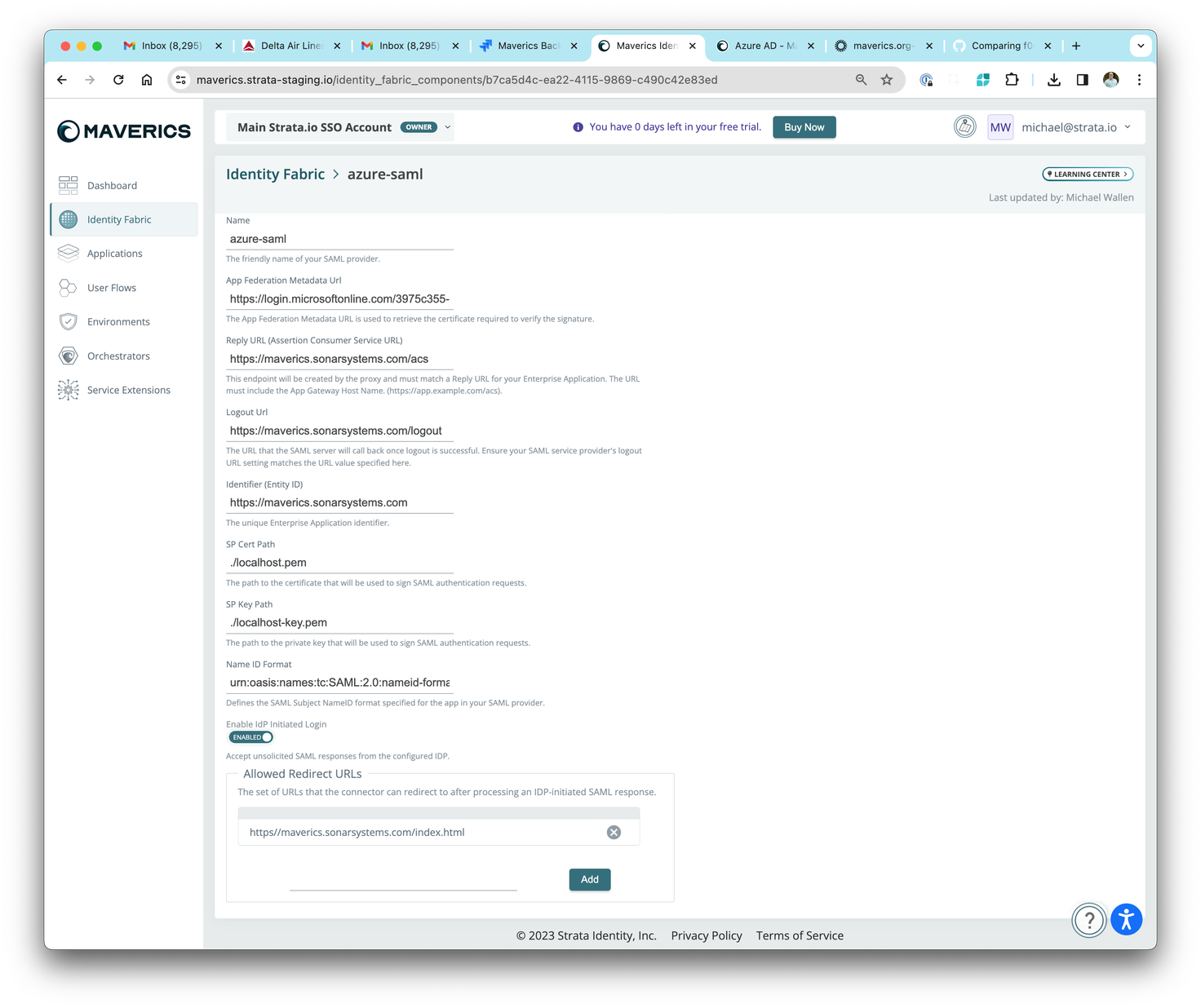
Resolved issues
- TLS block for cache config is now properly formatted for deployment
2023-12-19: Windows client authentication
You can now add Windows desktop authentication to your identity fabric. The Windows Client Authenticator App for Maverics allows Windows/IIS users to validate their identity to Maverics Orchestrator using their Windows desktop credentials. The app can be downloaded from any environment.
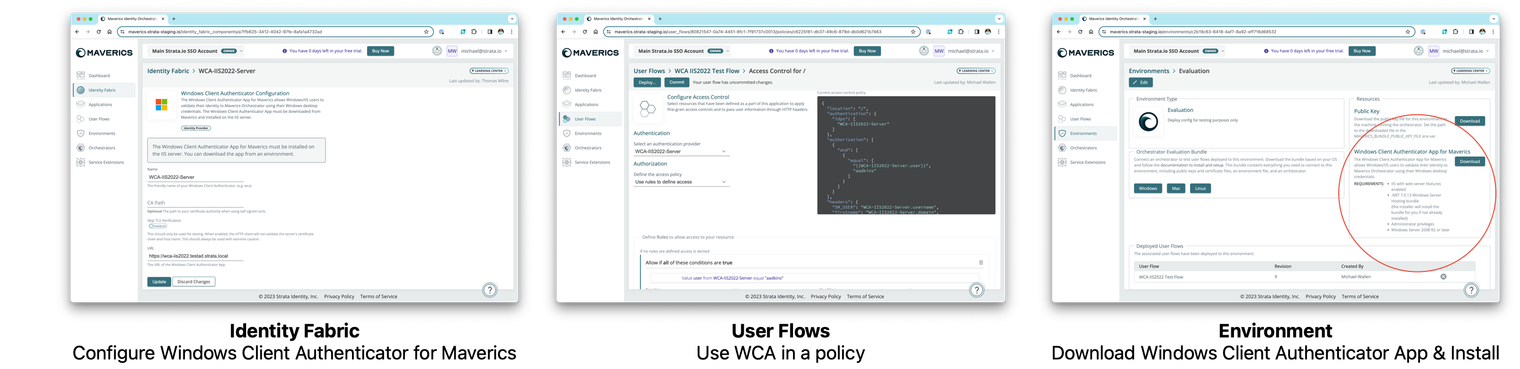
Resolved issues
- Resolved an issue where policies that use
equalswere not being deployed. - Resolved an issue where service extension claims values where not appearing on first page load.
2023-12-13: Fixed missing metadata on deploy that includes a Build Claims SE
We’ve released a partial fix to an issue where metadata entered in a build claims SE was not deploying with a user flow.
2023-12-07: Improved import of service extensions and deployment of updated service extensions
This release includes continued improvements to the import process. You can now import user flows that reference service extensions. Deployments now include additional metadata in the JSON for the import process to execute correctly, however the metadata is completely ignored when read by the orchestrator.
Note: To use this update, you will need to redeploy a user flow that contains service extensions, then download the maverics.tar.gz file and re-import using the button on the dashboard.
Resolved issue
- Fixed an issue where the the latest edits of a service extension were not being deployed in a user flow. This condition was found when two user flows were being deployed that reference the same service extension. Now in this scenario Maverics will always deploy the latest service extension. This is consistent with how identity fabric (Connector) config is deployed when referenced by more than one user flow.
2023-12-05: Canada region selector, import enhancement, and Learning Center update
New accounts have the ability to sign up and login to the new Maverics Canada instance. Accounts in the US and Canada are completely separate. Features and fixes are deployed at the same time as the US.
To use the region selector, go to https://maverics.strata.io and select Canada from Available Regions. You will then be redirected to https://ca.maverics.strata.io to sign up for a new account.
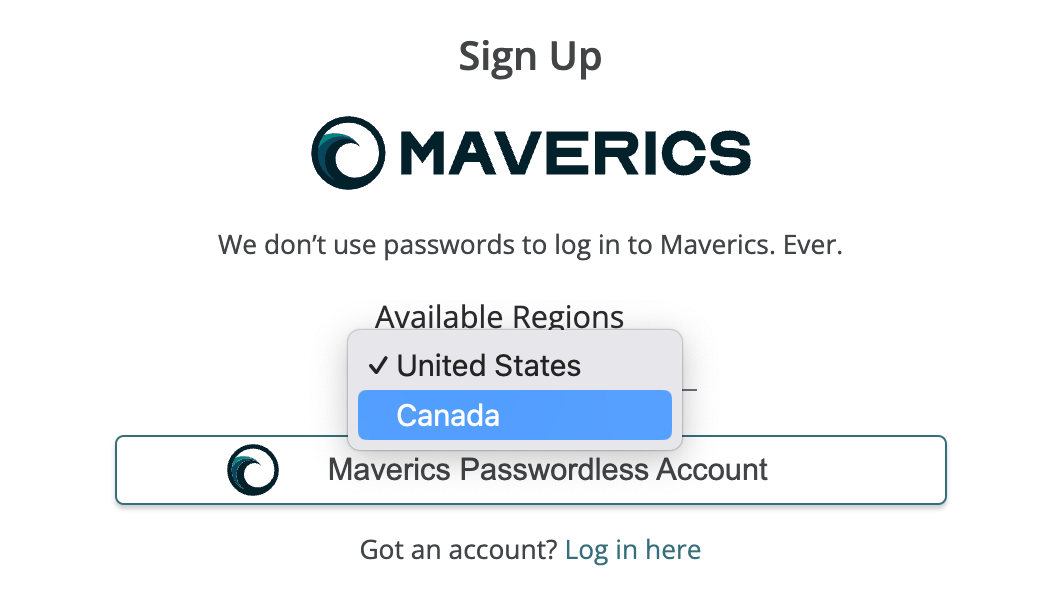
Existing customers who would to use the Canadian region instead of the US region need to manually migrate their data to a new Canadian account. Maverics has import capabilities that can help facilitate migrating user flows, app fabric, application definitions, and environment settings to a new account.
Import configuration to existing environments
When you import configuration, creating a new environment is now optional by default. This enables yyou to easily deploy user flows to existing environments without creating unnecessary environments.
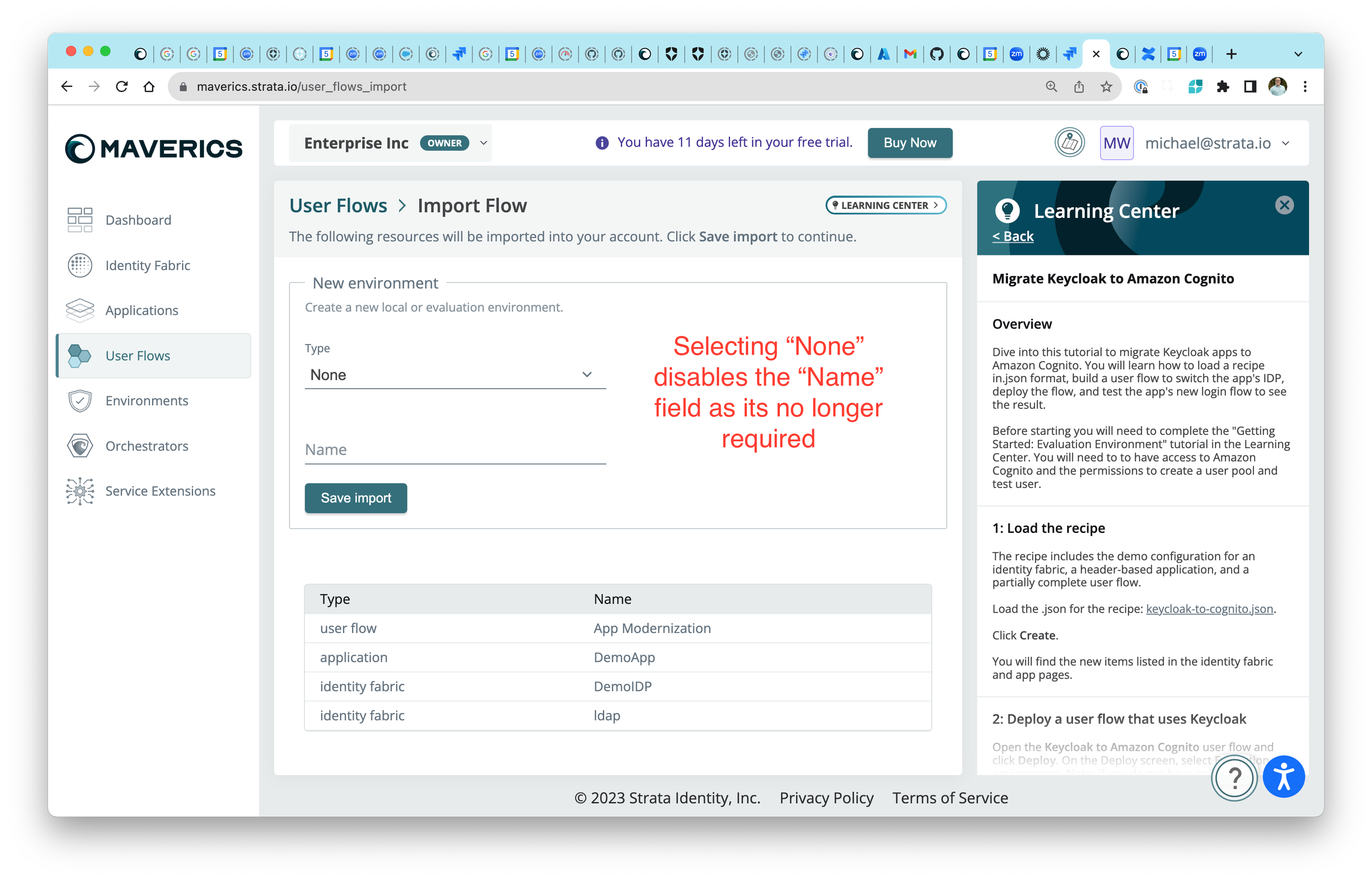
Recipe formats included in the Learning Center have also been updated to use Proxy type apps.
Resolved issue
- Empty IDP-initiated login fields are no longer being set in the deployed config.
2023-11-29: nameID format for SAML app type
You can now specify the nameID format of your choice in the SAML app type setup.
Resolved issue
- You can now specify the OIDC well-known endpoint in the Azure AD attribute provider configuration. This will enable you to use Azure as a standalone attribute providers with other IDPs.
2023-11-28: Attribute provider bug fix
Resolved issue
- Fixed an issue where if an attribute provider was included in a rule, an inspection error was shown that prevented you from being able to commit and deploy.
2023-11-21: Resolved SAML issue
- If you set up custom certs in the SAML auth provider settings, the SAML cert you download from an Environments page now displays the correct cert (*.pem file).
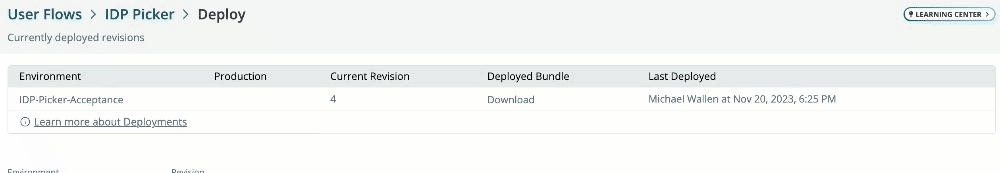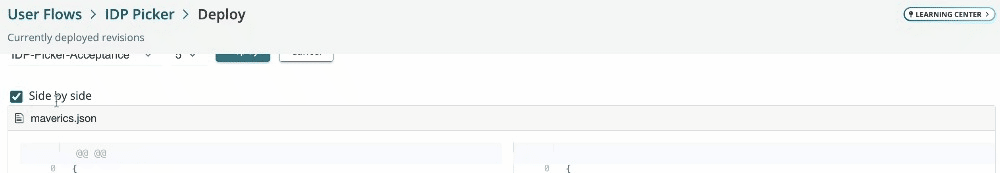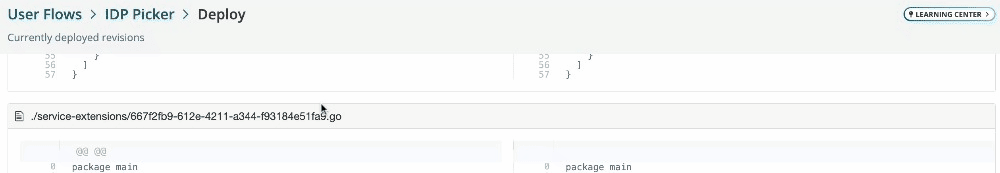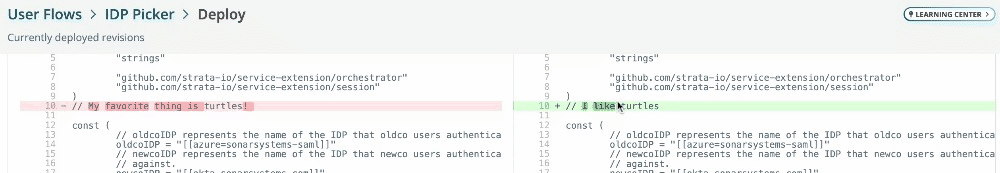
2023-11-20: Service extension code editor improvements
The service extension code editor will now show compile errors as you type.
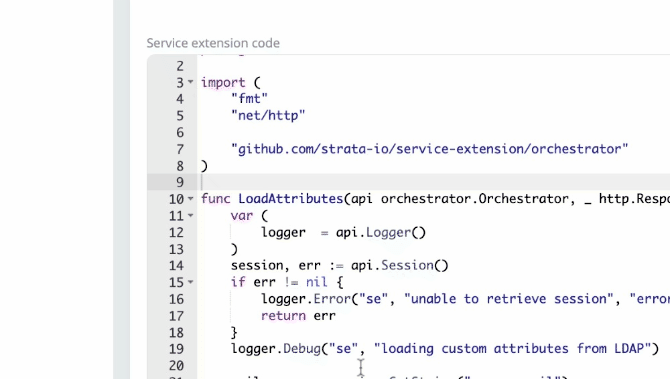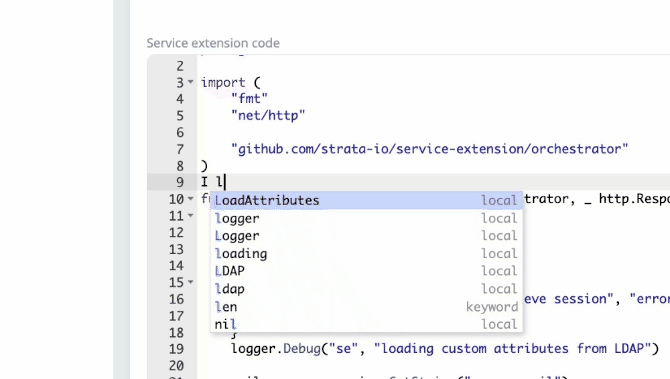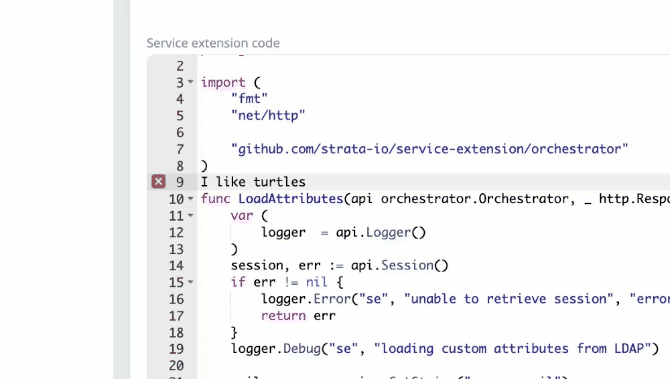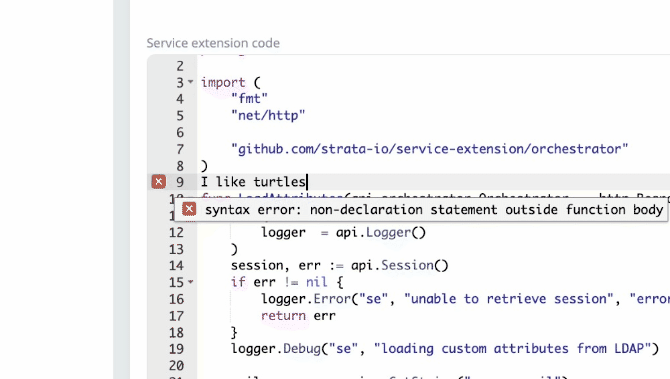
Additionally, the deploy screen will now show service extension diffs.
Resolved issues
- When an account owner deletes an account, it will only delete the selected account and not delete the user. When a user logs in that has no accounts they will be shown the Oops Octopus error. From here they can be invited to another account or delete their user from the profile menu.
- Fixed an issue where the import of service extension names came through as ids. Now all service extensions deployed will include the name field.
- When editing an environment, a breadcrumb to go back to the environment now appears.
2023-11-16: Sonar OIDC test app!
To test OIDC auth flows, we have an updated image in Docker Hub and documentation on how to use it to spin up your own local running version of Sonar.
Resolved issues
- Orchestrator telemetry is now off by default when creating any non-evaluation environment
- Audited all default service extension examples to ensure they can deploy without error to orchestrators. Added a specific note about using claims SE with SAML apps.
- Fixed cert issues when downloading a SAML metadata file
- Fixed edinvite sign-up flow when user has already started sign-up
- Fixed a validation on static headers that prevented you from using a
or a period in a value.
2023-11-14: Proxy app: static headers
When creating a proxy app user flow, you can now send any static header without having to source it from the session.
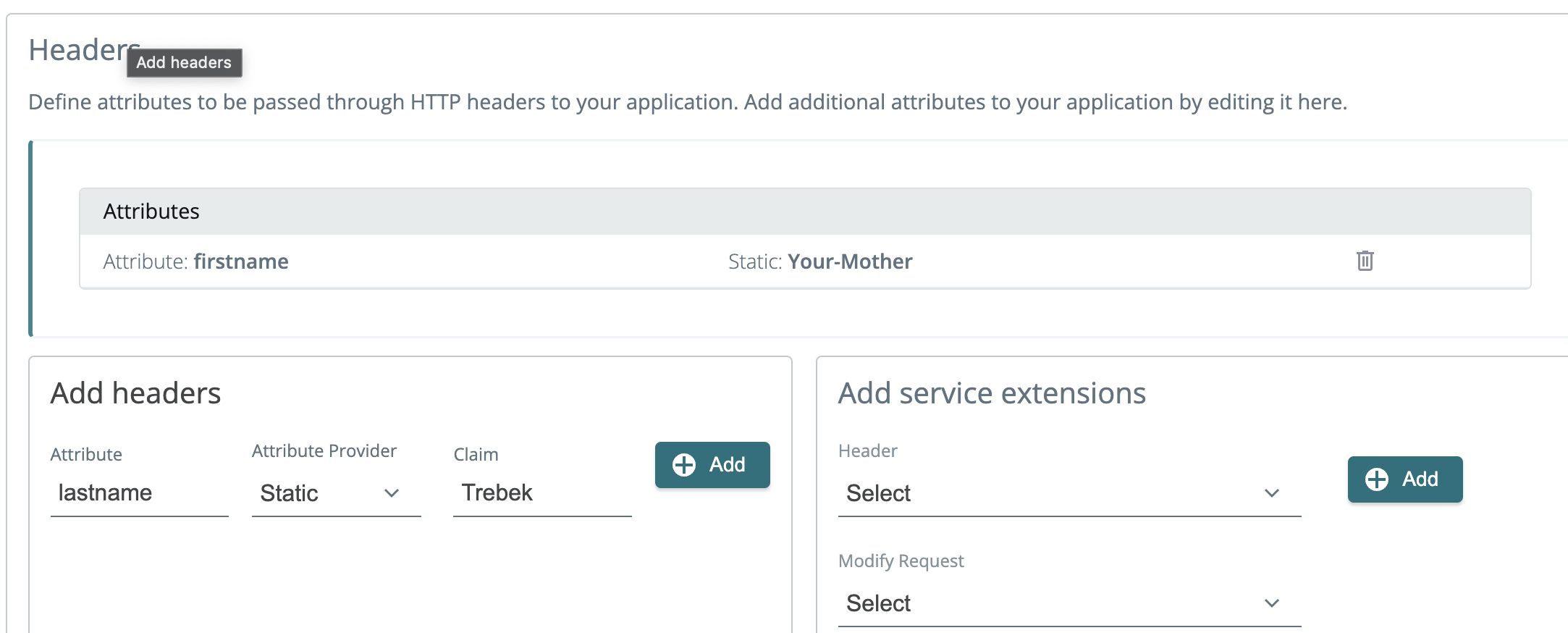
Set your attribute, and choose Static as the attribute provider. The header will be sent to your favorite proxy app.
Resolved issues
- Duplicate accounts are no longer created if a user attempts to sign up multiple times through PLG or SLG sign up flows.
- The Calendly scheduling widget will now render properly on Safari.
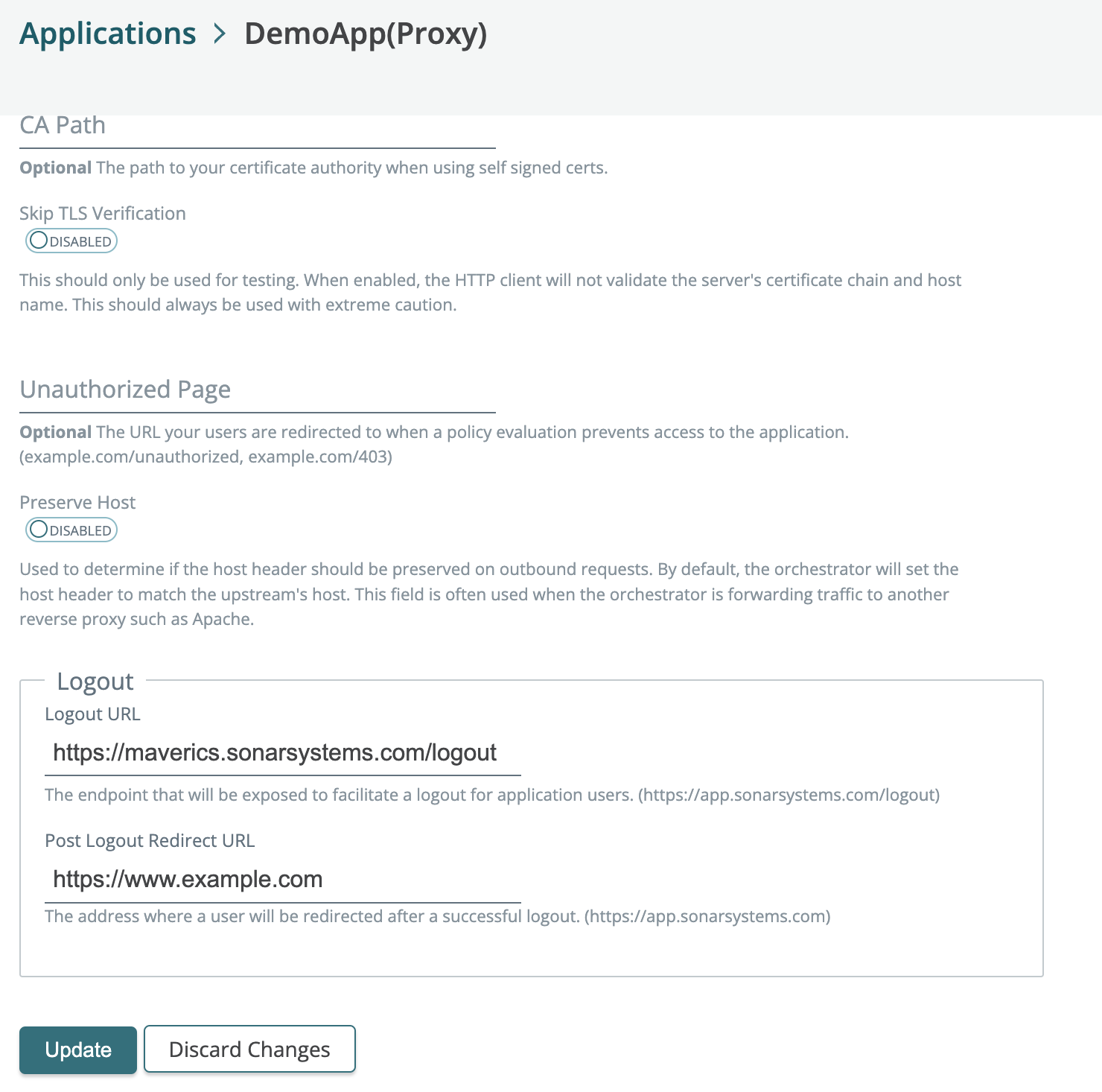
2023-11-10: Proxy app specific logout
You can now add a proxy app logout URL and post logout redirect URL to proxy apps. See our docs.
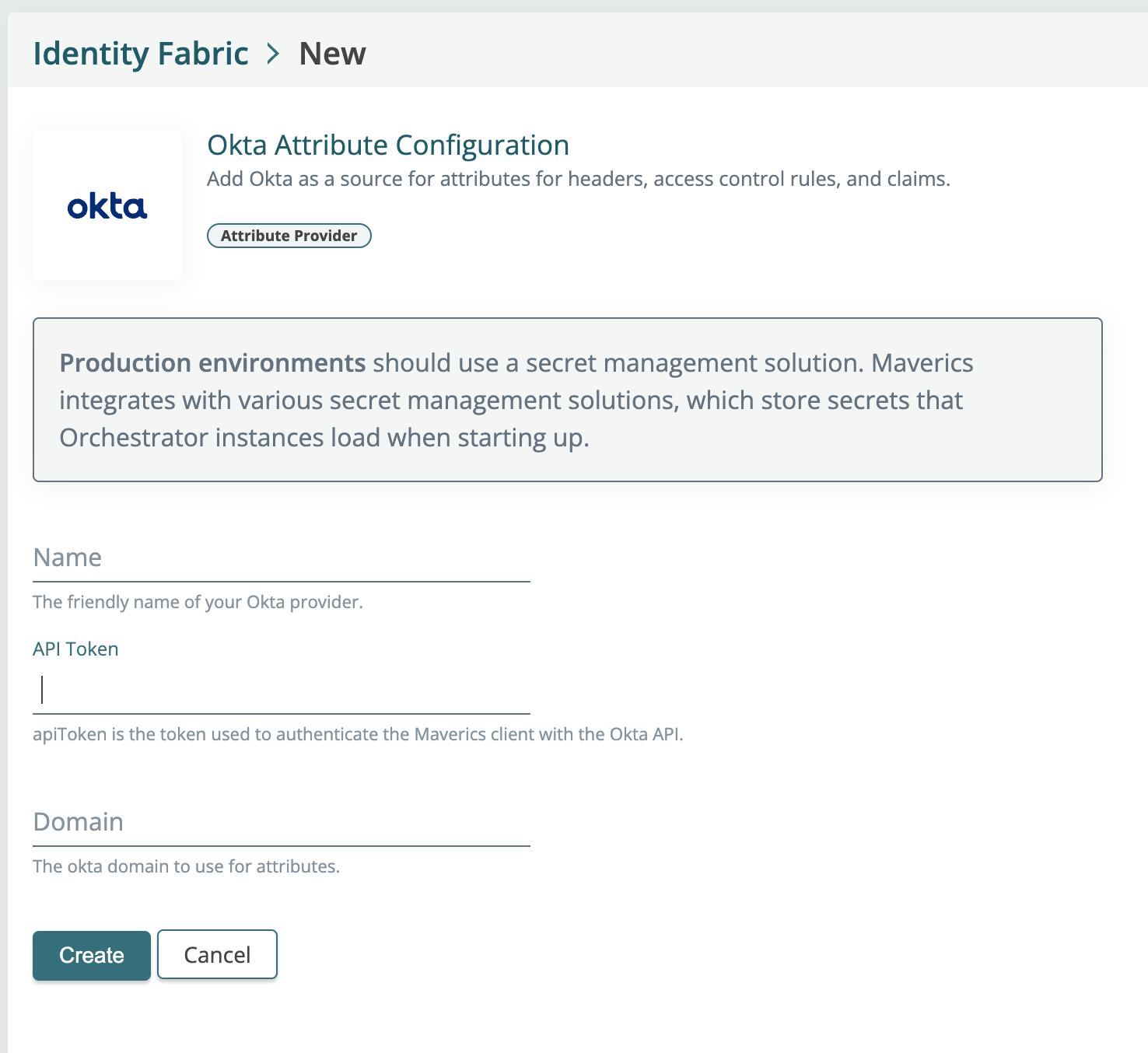
Additionally, if you need to make a query to Okta to add custom claims to your session you can now do this by using Okta as a attribute provider.
Resolved issues
- Metadata from service extensions persists and are now properly deployed.
- Claims set in service extensions can now be properly selected and deployed for OIDC and SAML apps.
- Partial fix for sign up issues causing duplicate accounts.
- Fixed an issue where attribute providers username mapping configuration was malformed for proxy apps.
- No longer missing last commit date/time for user flow list
- Resolved an issue where the orchestrator would fail to start up a SAML or OIDC app type service due to a configuration mismatch when a service extension is present. Maverics will now omit claimsmapping if empty when deploying SAML or OIDC app type user flows.
2023-11-06: Service extensions metadata
You can now define key-value pairs for additional context, such as environment variables, in your service extensions.
Resolved issues
- Updated logos on signup.
2023-11-02: IDP initiated login for SAML app user flows
Maverics now enables you to set up an IDP-initiated login flow for a SAML app type.
Resolved issues
- Addressed an issue where headers were missing or not properly generated for proxy app deployments. (Note: This is still an issue for existing header-based apps. To utilize the fix, create a new proxy app. The fixes to existing header-based apps will be released soon.)
2023-11-01: Introducing proxy apps!
Header apps are now called proxy apps. You will still be able to edit and deploy existing header app type user flows, however you will no longer be able to create new AppGateway-based configuration in Maverics. Instead, you can create proxy apps.
We have also released a new service extension format and updated our service extension examples.
Resolved issues
- You can now successfully add headers to location policy.
- You will no longer get orchestrator errors due to the extraneous empty cache config.
2023-10-24: Updated invitation email
We’ve updated user invitation emails to specify the user who sent the invitation and the account you’ve been invited to.
2023-10-23: Transfer ownership of an account
In the Accounts section, you can now transfer ownership of an account to another member of your team. Owners of accounts can invite members, make payments, or delete the account. To transfer ownership of your account, go to Profile > Accounts.
2023-10-16: Resolved issue
- You can now delete your user profile without error.
2023-10-12: API app type support
Import now supports API app types. You can now download a deployment bundle that contains a API app type user flow and import that configuration into a new local or evaluation environment.
User profile page
Users now have a Profile page where they can view their name and email, and delete their profile. If the user is an account owner, it will delete the account. If the user is a member of another account, it also will remove them as a member of another account.
Resolved issues
- Updated the build claims service extension code example
2023-10-05: Member invitations
When inviting a member to your account, the invitee no longer has to sign up for a personal account. They become members managed by another account owner.
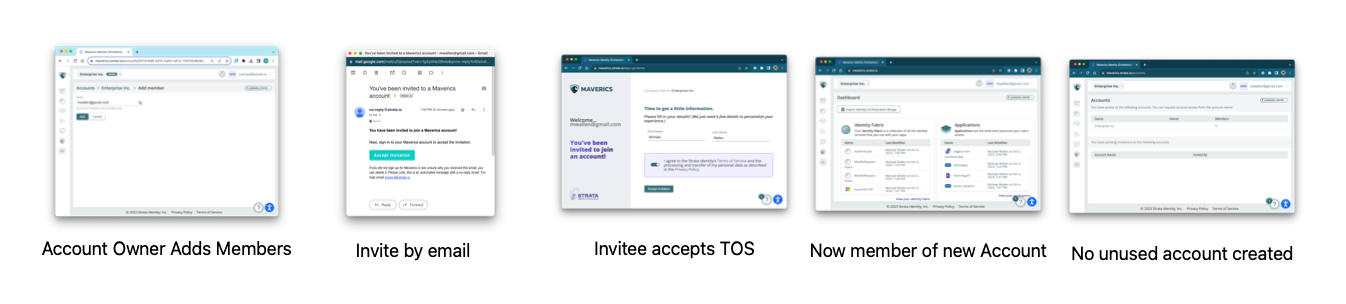
Additionally, import options now support orchestrator settings.
Resolved issues
- The new IDE now shows up properly for API app types.
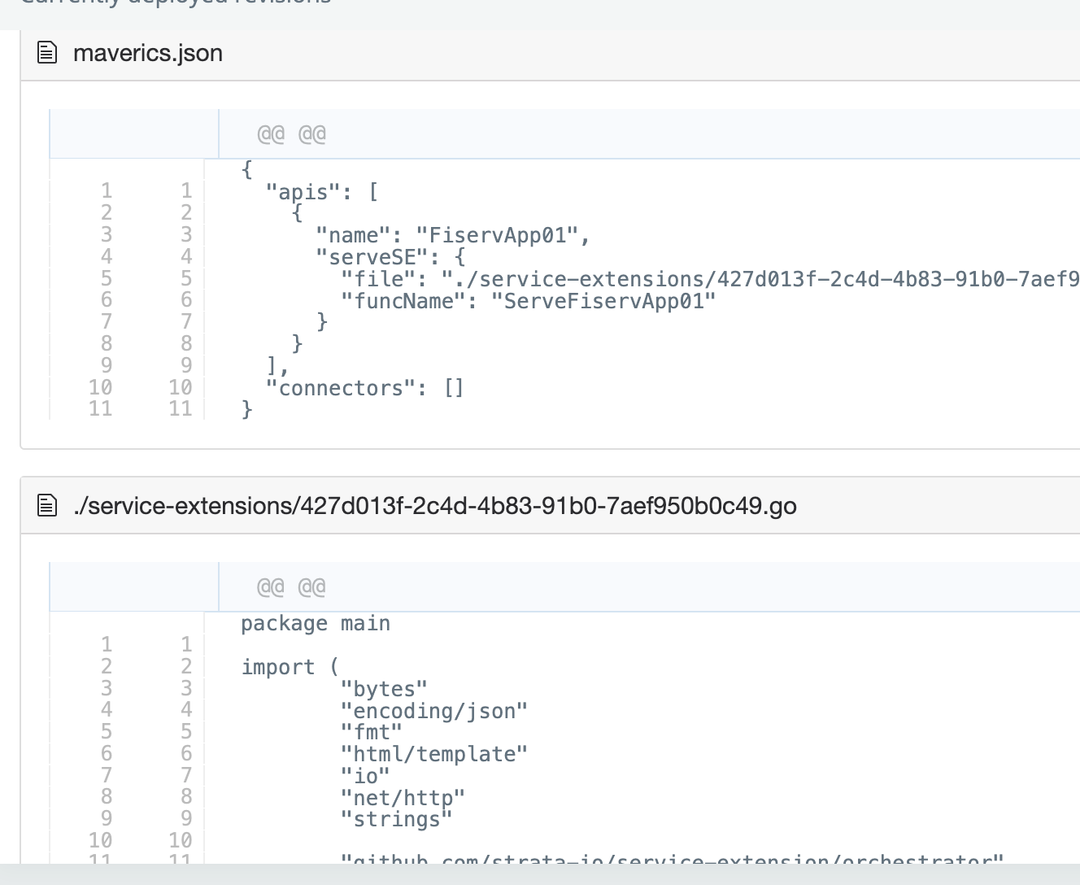
2023-10-04: Splitting the main configuration and service extensions for API app type user flows
When deploying a configuration, the deploy preview can now show code changes in the main configuration separately from code changes in the bundled service extensions.
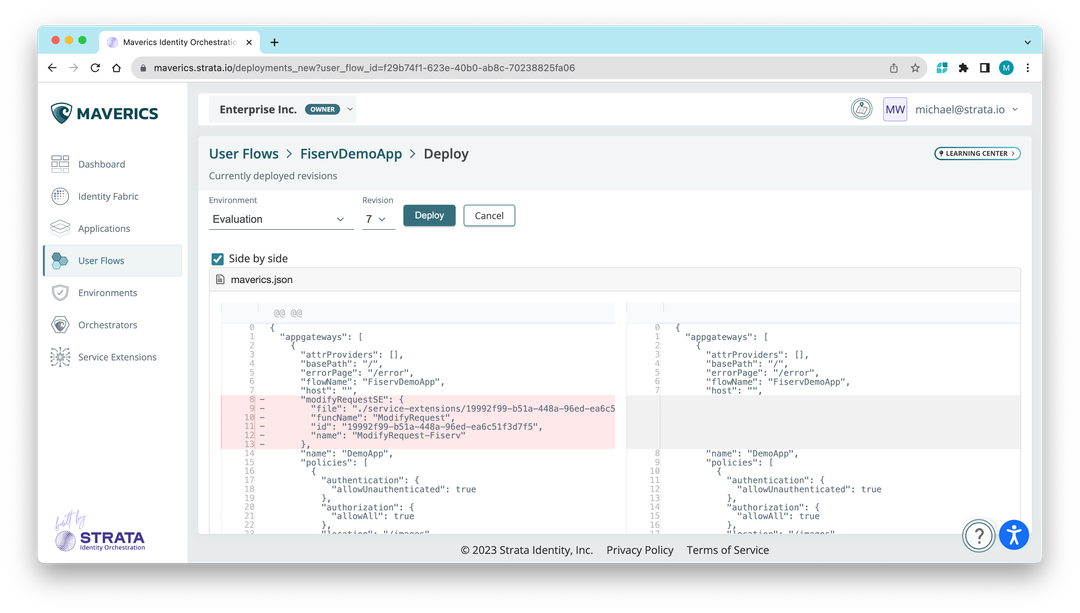
Note: This feature is currently limited to API app type user flows.
Additionally, we now offer a side-by-side comparision view in the deploy preview.
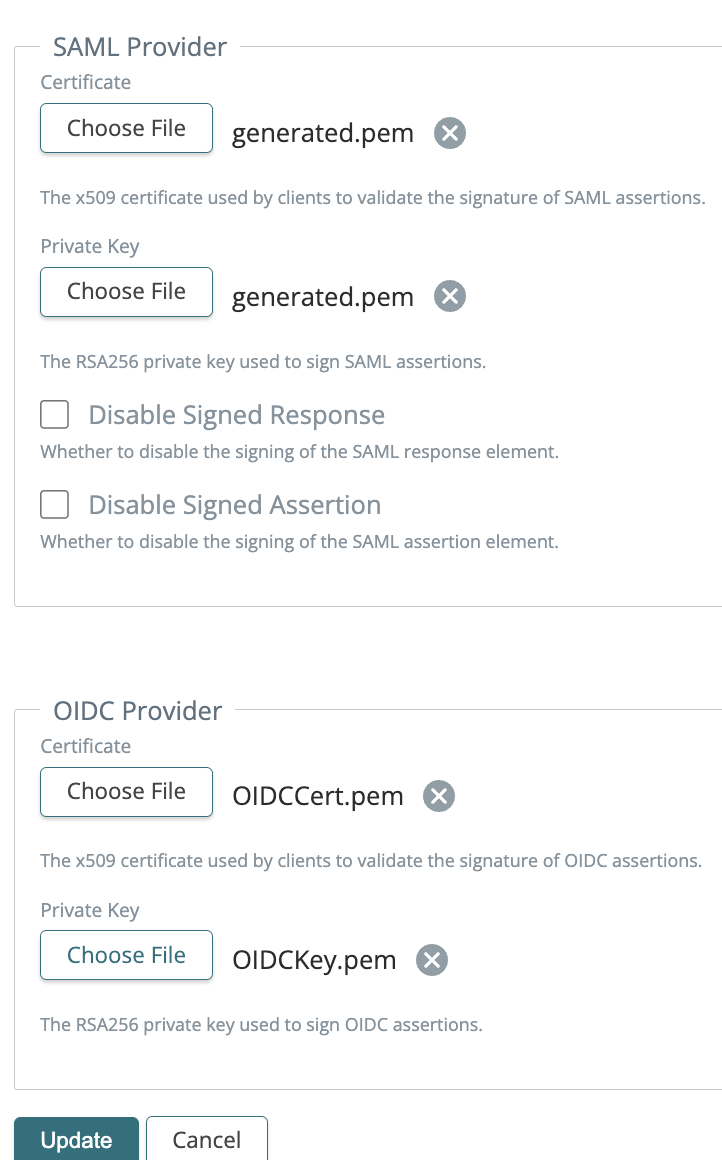
2023-10-02: SAML and OIDC Auth Providers settings in Environments
You can now upload independent key pairs used for encryption for SAML and OIDC Auth Providers. To use this, open an environment and click Edit. Scroll down and upload your key pairs.
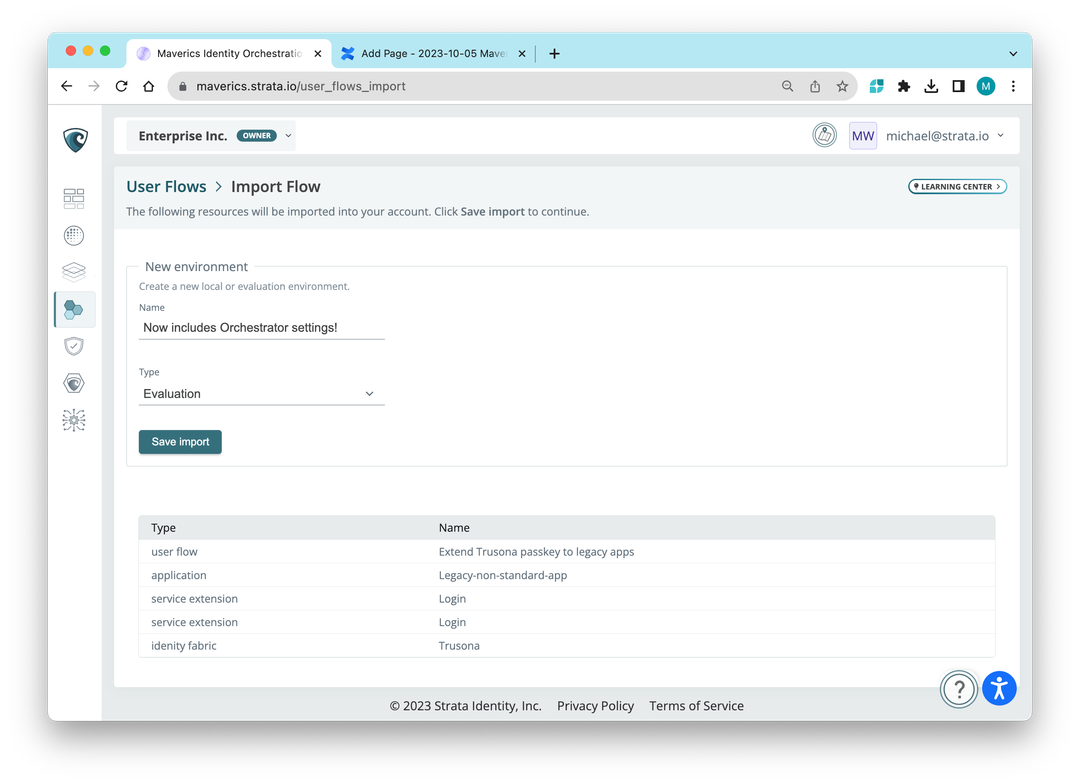
Additionally, the Import function now shows a preview of ingredients being imported, and a new tutorial to extend Okta to a legacy, non-standard app is now available in the Learning Center.
Known issues with SAML and OIDC Auth Provider certs
- After you have uploaded custom key pairs, you are unable to revert back to use generated certs
- When using a custom cert for SAML and generated Cert for OIDC, the deployed config has invalid name values in the OIDC config (workaround: use custom certs for both key pairs in the unlikely event you deploy both of these app types to a single environment)
Resolved issues
- A portion of the Learning Center no longer appears on the first step of signing up with HYPR.
2023-09-29: Handle unauthorized service extension
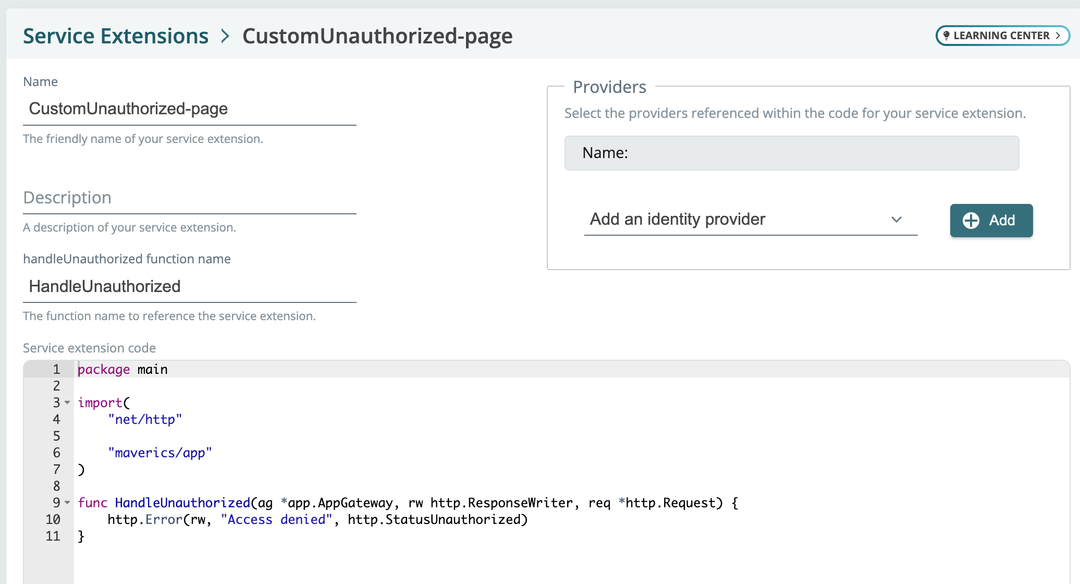
Our new CustomUnauthorized service extension enables you to provide a custom experience when a user is not authorized to access a resource.
2023-09-27: SAML app encryption options
When defining a SAML app, you can now upload a cert to verify the signatures of incoming requests.
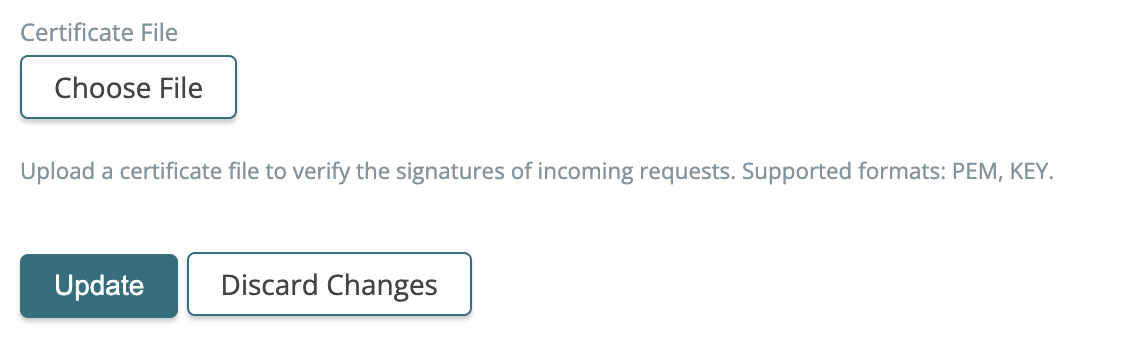
When there is no cert uploaded the resulting config will now include: "requestVerification": { "skipVerification": true
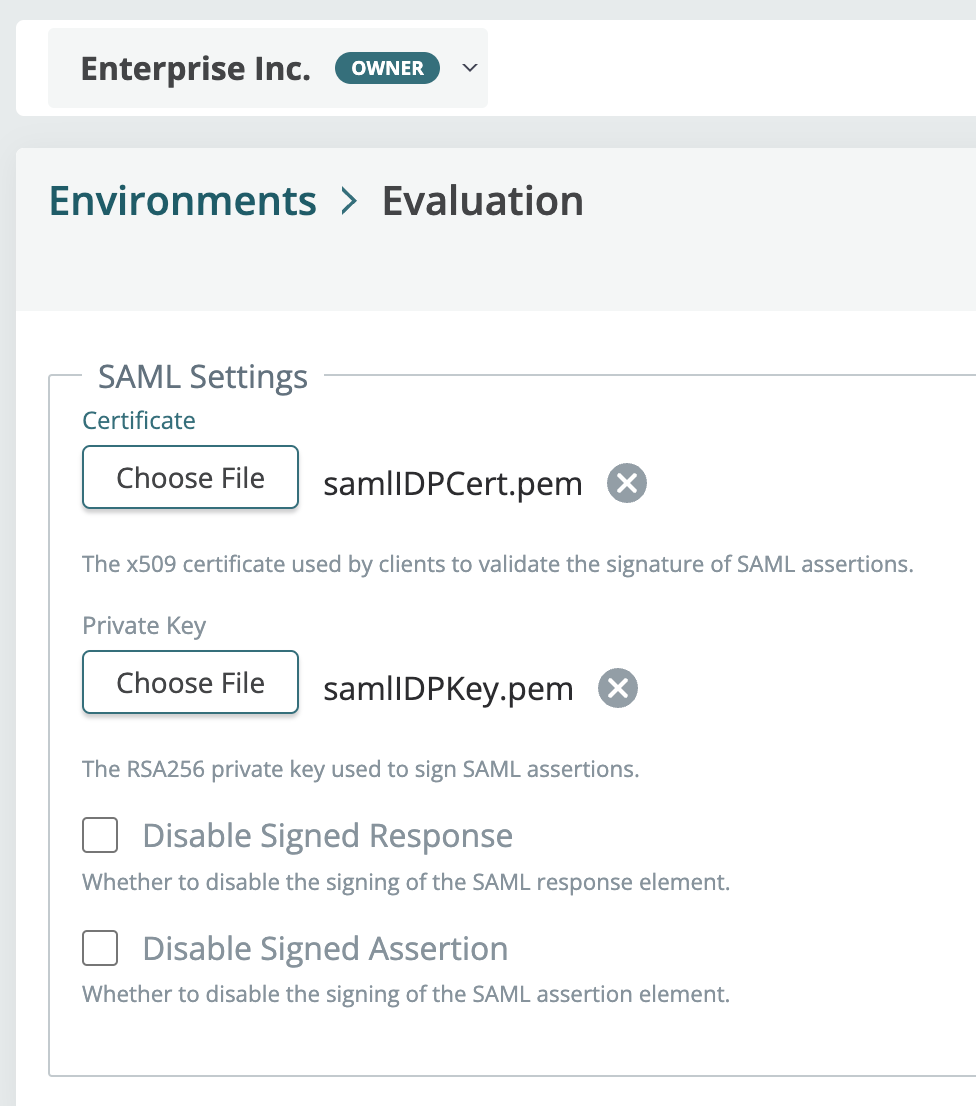
- Create/edit environments: SAML provider encryptions options are available when you create and edit an environment.
- Custom key pair: You can now override the automatic generation of certs/keys and upload a custom cert and key pair.
- Disable signing: You can now disable signed responses and assertions.
Known issue
- Checking both Double Signed Response and Double Signed Assertion will result in an error from the Orchestrator. They are meant to be used one at a time, however this will be addressed in a future update.
Import enhancements: Service extensions
You can now import tar.gz files. These can contain app definitions, identity fabric config, user flows…and now user flows that contain service extensions.
To use it:
- Deploy a user flow that includes service extensions.
- Download the configuration either from the deploy screen or from the environment.
- Go to the Dashboard and choose Import using a tar bundle.
Resolved issues
- Fixed an issue where you could not import json from the Learning Center tutorials.
2023-09-26
Import config: expanded to support OIDC and SAML app type and user flows
The import config capability now has a number of use cases that it supports.
- In-application tutorials: It is used to import recipes in our tutorials
- Application Onboarding: After a deal is signed, a discovery process launches during a kick-off with our customers. They often complete an inventory of hundreds of applications with technical information that we need to define in config. Now you can construct a JSON file from this data and import it directly into Maverics taking a once manual input process and automating it completely.
Other import enhancements include:
- “Flow” is no longer appended to the name of an imported flow.
- Flow names are supported on import/export with the flowName key in the json.
- You can now import OIDC and SAML app type and user flows
To use it:
- Deploy a SAML or OIDC app type user flow.
- Download the .tar.gz bundle from the Environments page
- Unzip the bundle and open the maverics.json in a text editor. Copy the code.
- Go to Import Identity Orchestration Recipe Import https://maverics.strata.io/user_flows_import
Policy editing refinements
You can now add add identity fabric to a policy location without having to specify it on a user flow. The radio buttons are now gone and replaced with drop-downs. We also took the opportunity to polish the titles and descriptions with terms that are more straight-forward.
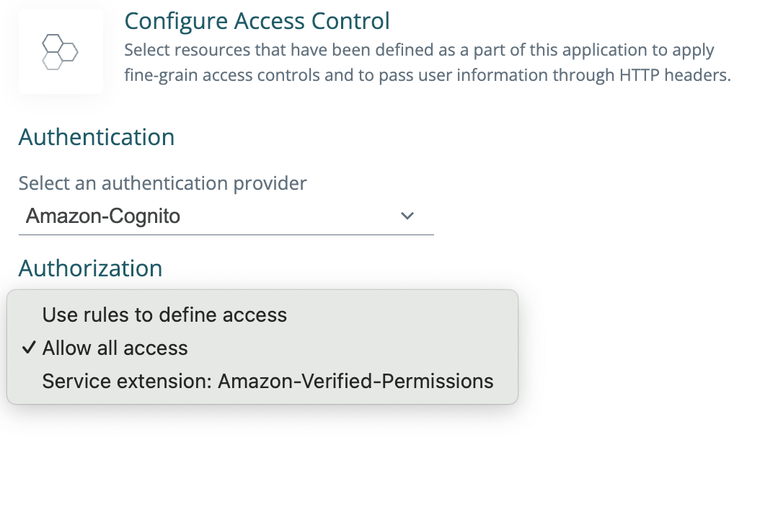
Note: The authentication section no longer appears on the user flow definition page for a header based app. This is not an error. It has moved to a policy definition drop down.
Keycloak to Amazon Cognito tutorial in the Learning Center
The newest tutorial available in the Learning Center helps on-prem Keycloak customers extend to Amazon Cognito.
To use it, you will need a Cognito User Pool and test user. You will be adding a client and creating a test user. To try the tutorial, go to https://maverics.strata.io/learn/redirect?context=keycloak-to-cognito-recipe
Service extensions: code editing enhancements
The new GO code editor for service extensions provides an enhanced syntax formatting autocomplete. The editor provides a lightweight editing experience, and is not intended to be used like a full IDE.
To use it, start editing service code a drop down will automatically appear with suggestions. You can also ctrl+space anywhere in the code editor to manually envoke the code editor.
Other resolved issues
- When importing a recipe, application icons will no longer appear as broken images.
2023-09-14: Duo Single Sign-On is now available!
Using Duo and Maverics together has become even easier. You can now set up Duo Singe Sign-On (SSO) as part of your identity fabric, and use it for authentication in your user flows.
Other features
- You can now sort user flows by the last commit date.
2023-09-12: Several feature enhancements
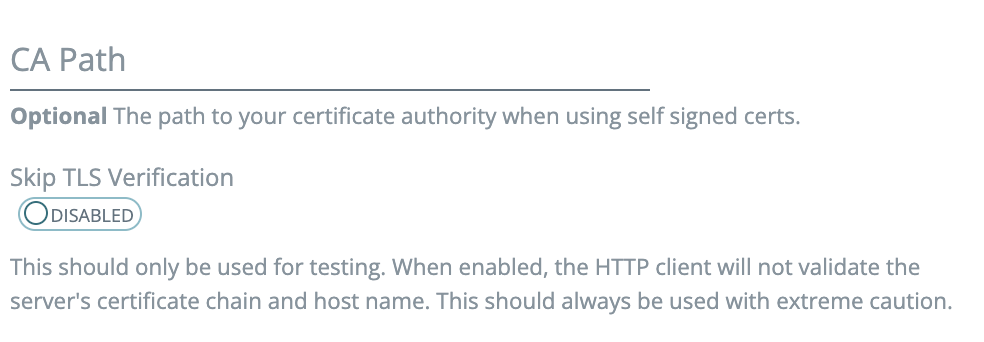
Applications
- You can now specify TLS settings in header-based apps
- Add a path to a CA cert
- Skip TLS verification (enableSkipVerify):
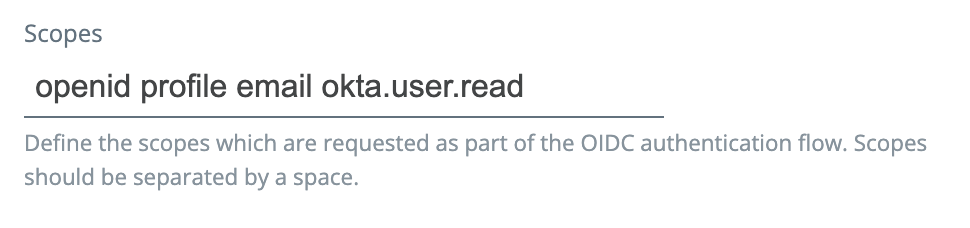
Fabric
- Fabric now includes the
logoutURL(for example, https://auth0tenantname/v2/logout) required by Auth0. - You can now specify scopes in OIDC providers.
Other features
- Mac, Windows, and Linux now have the same easy 3-step experience. Our updated Linux evaluation bundle now includes a raw orchestrator Linux executable. There’s no need to install an RPM enabling you to launch it from a command line.
- Login and isLoggedIn service extensions are always used together and have now been combined into a single form called Upstream Application Login.
Resolved issues
- Updated service extension names and descriptions
2023-09-11: Service Extension parity
We’ve now achieved 90% parity with the service extension points available via the YAML API.
Introducing API application type (ServeSE), isLoggedIn, and Login
Develop an API app to facilitate identity flows by creating custom HTTP endpoints, serving HTML pages, or executing custom scripts.
To use it:
- Go to Applications and select API from the application type column.
- Enter a name, description, and function name (for example, Serve).
- Add your Go code in the code editor and click Create.
- Create a new user flow and select the app you created in step 3.
- Commit and deploy. You can now deploy user flows that can integrate with these APIs.
You can also add Login service extension points to your header-based app user flows.
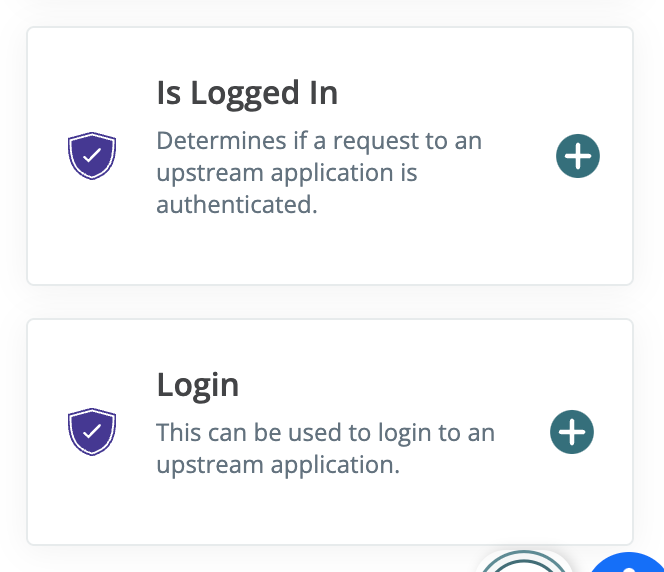
Select from Service Extensions.
Add to your header-based app’s user flow.
When a service extension code has been modified, any user flows that reference them will be updated with the status of ‘Uncommitted changes.’ This will signify that you need to commit and deploy to have the changes take effect.
Finally, in order to simplify the experience, the identity fabric code view has been removed. You can still see the code on the user flow deploy step.
2023-09-05: Improved Windows evaluation bundle
The Windows evaluation experience has been improved. You no longer have to:
- Run an installer
- Delete system environment variables (e.g. default yaml config and license files)
- Edit registry values
- Edit
maverics.env- all paths to certs and keys just work
To use it:
- Download the zip file and right click and select “Extract all…”
- Open the Command Prompt.
- Use
cdto navigate to where you extracted the eval bundle. - Run
call maverics.bat && maverics-orchestrator.exe - Go to Orchestrator Telemetry and check for the green dot.
Other enhancements
- You can now modify requests and responses using service extensions in header-based apps.
Resolved issues
- Fixed an issue selecting a provider when creating an authorization rule.
2023-08-24: Commit to Deploy
To improve the usability of Maverics, we have reworked Save Revision, Publish to Commit->Deploy. This includes:
- For easy access, it is now pinned to the top of the user flow screen and the Edit a resource location policy screen.
- Save a revision is now a Commit in a model dialog
- Inspector results are accessible on hover when there are errors on a user flow. Note: before you can commit you must clear all the errors.
Other enhancements
- You can now specify attribute provider and username mapping in SAML and OIDC app type user flows,
- The maverics.env in the Windows evaluation bundle has been improved to make it easier to copy and paste. We also have a new Learning Center topic in the Learning Center to walk you through the Windows process.
- You can now specify signing certs in AD FS and Azure AD SAML configs to verify that the authentication requests are signed.
2023-08-21: Evaluation Experience
There is now a step-by-step guide the Orchestrator Evaluation Bundle installation on Windows.
Resolved issues
- Addressed an issue where you could not add a header to a user flow.
2023-08-16: New Service Extensions
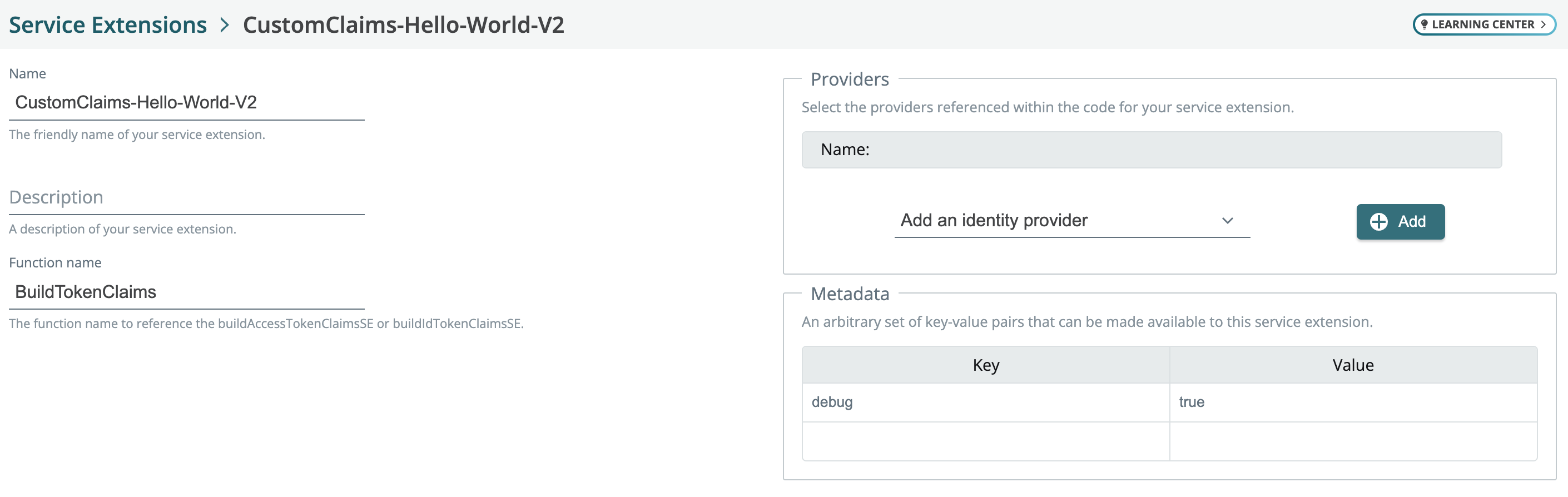
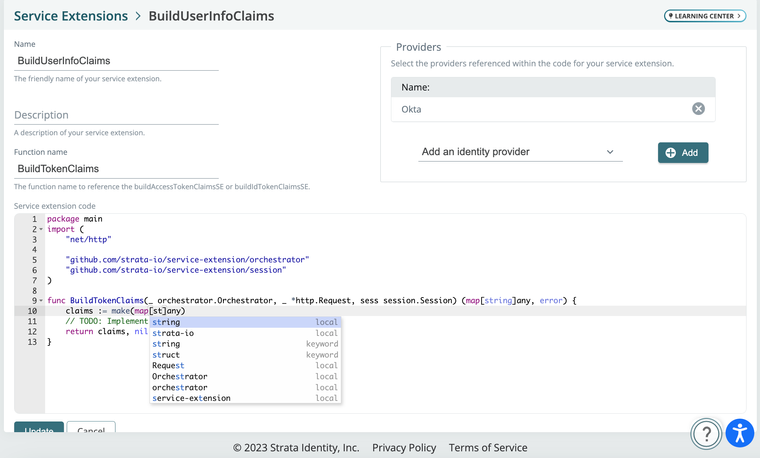
You can now leverage the buildAccessTokenClaimsSE or buildIdTokenClaimsSE service extension points in the platform to build custom token claims for OIDC and SAML app type user flows. To use:
- Go to Service Extensions, and select Custom Claims from the Service Extension list.
- Enter a name and description, and click Create.
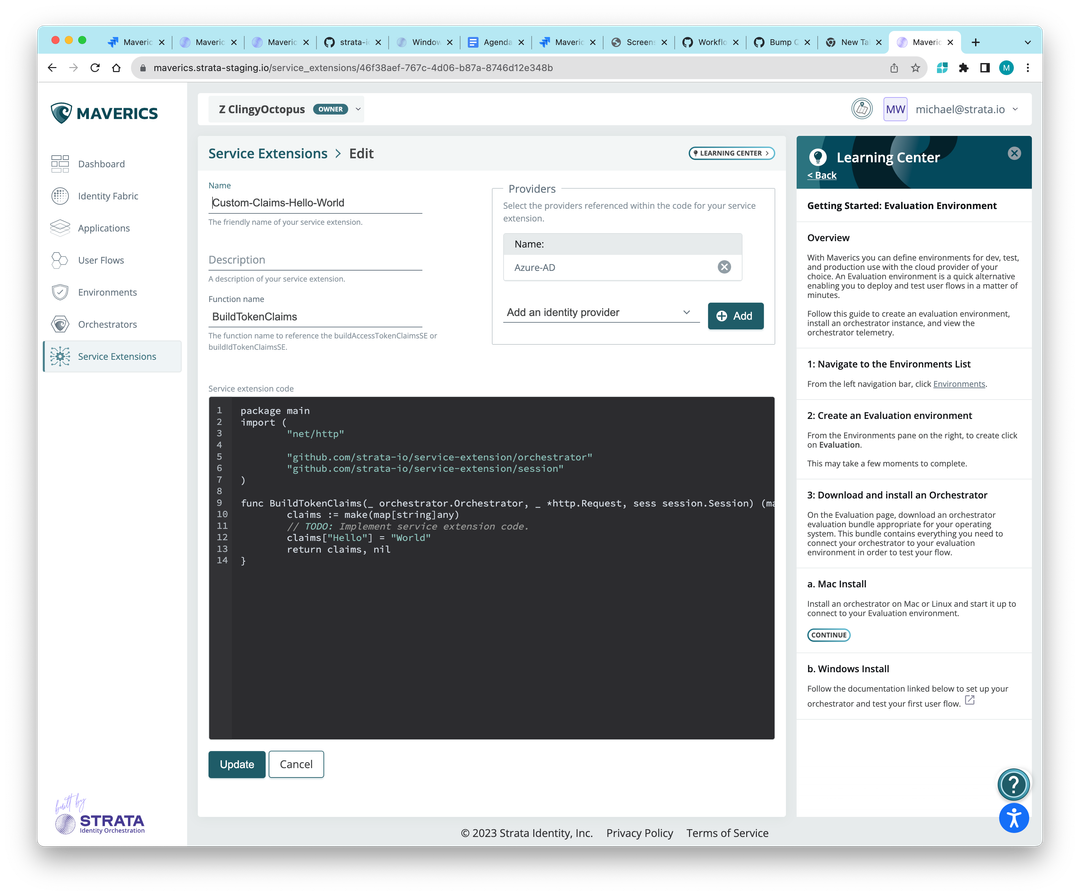
- Paste in your Go code. Here is a “Hello World” example that prints a log event after a user logs in:
package main
import (
"net/http"
"github.com/strata-io/service-extension/orchestrator"
"github.com/strata-io/service-extension/session"
)
func BuildTokenClaims(_ orchestrator.Orchestrator, _ *http.Request, sess session.Session) (map[string]any, error) {
claims := make(map[string]any)
// TODO: Implement service extension code.
claims["Hello"] = "World"
return claims, nil
} - Go to Applications and create an OIDC-based app type.
- Go to User Flows and create a new user flow. Select the app you created in step 4, and specify an IDP in the following screen.
- On the User Flow page, scroll to Claims. Select the service extension you created in step 3 for either an Access Token or ID Token.
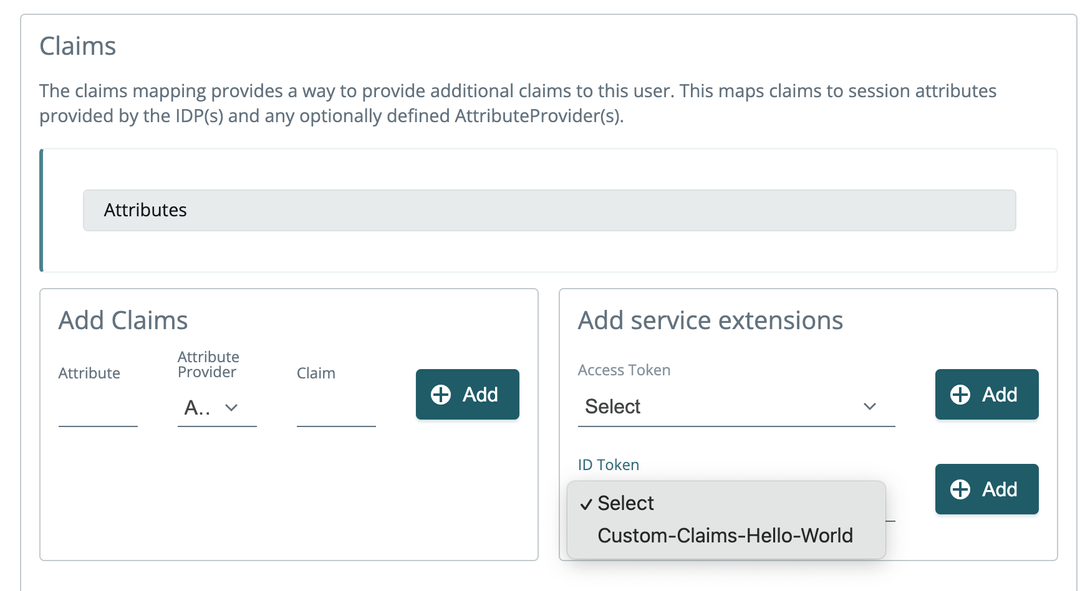
- Click Save Revision and publish the user flow and login to your app.
- In the orchestrator log, you will see:
ts=2023-08-16T22:51:59.768756Z level=debug msg="adding claim Hello:World to ID token" client=client-idEvaluator Experience: Welcome to Maverics!
There is a new guided tour for new account sign-ups that draws people to the Learning Center.
The Learning Center has many content and style updates to make the topics easier to read and understand. There is now a back button so you can navigate more easily between topics.
Resolved issues
- Unable to add multiple rules or conditions to a access policy
Known issues
- Currently you are unable to add a header to a header based user flow. As a workaround, you can add them to a resource location policy to achieve the same result.
2023-08-10: Evaluator experience
The responsiveness of Maverics has been optimized for laptop use. We’ve fixed several issues where page headers and columns were displaying incorrectly when the Learning Center was open. Additionally, we’ve improved the styling on the Learning Center.
2023-08-07: CPU utilization telemetry and service extensions update
A CPU utilization chart is now available in Orchestrator telemetry (Note: Due to limitations of Mac OS, no data will be reported for this metric).
Additionally, IDPs referenced in a service extension definition are now automatically included in the deployment. We’ve also made the app more responsive with a collapsible navigation, improved break points, and layout adjustments.
Resolved issues
- Fixed issue that prevented people from downloading a Docker image for non-evaluation environments
2023-08-01: Learning center now available with two lessons
The first iteration of the Learning Center is available with two lessons:
- Create an eval environment: a complete how-to process for Mac
- Use the app modernization recipe: a new recipe that uses hosted demo assets and does not require Docker for the apps and IDPs
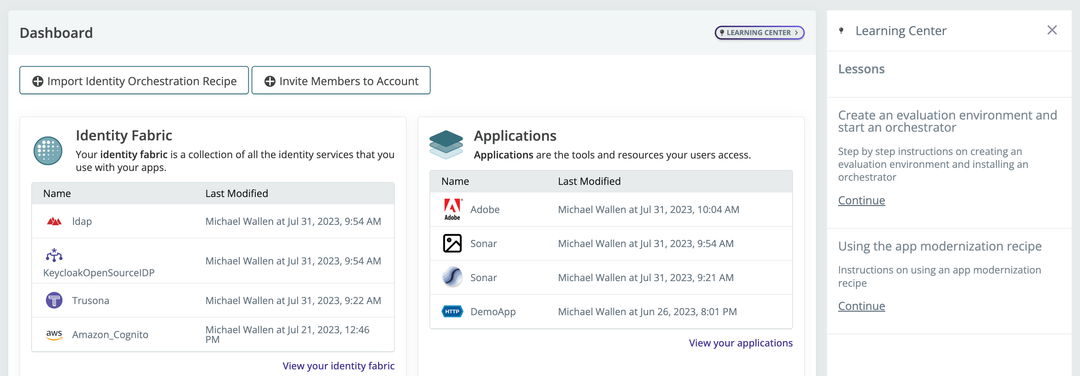
Orchestrator telemetry is also now available
New graphs in Orchestrtor telemetry show the session count over time. To test it:
- Start your orchestrator connected to an environment; give it a few minutes for the data to populate.
- Deploy a user flow that requires authentication, and sign in and out a few times.
- Go to Orchestrators and click on the Orchestrator ID to view the session graphs and other data.
Resolved issues
- Maverics correctly reports the number of days left on subscription pages
- Maverics now remembers the last logged in account
2023-07-24: Evaluation environments now available
In just a few minutes of setup, you can test your user flows with Evaluation Environments. Evaluation environments provide a ready-made cloud storage environment and companion orchestrator package. This enables you to quickly publish user flows and have them connect to orchestrators pre-configured to consume configuration from this environment.
To get started on Mac or Linux:
- Go to Environments
- Select Evaluation Environment from the list on the right.
- Download the appropriate orchestrator bundle for your OS.
- Unzip all the zipped files.
- Open the Terminal and navigate to the location of the unzipped files
- Source the maverics.env and start the orchestrator with the following command:
source ./maverics.env ./maverics_darwin_amd64
When creating this environment, Maverics will:
- Set defaults for Orchestrator URL (https://localhost) and logout URL (/logout) as well as other settings. You can change these settings by clicking the Edit button in the top right hand side.
- Push an empty maverics.tar.gz to the cloud storage bucket (a Strata controlled AWS bucket) so the orchestrator will start up successfully in case there is no user flow published yet.
- Create a downloadable bundle with a maverics.env preconfigured to connect to this environment
You can only have one eval environment at a time. After you create one, you will not be able to access Evaluation Environment from the right side bar.
See it in action:
Other enhancements
- The new load attributes service extension point enables you build custom flows such as the IDP picker. Sample code and instructions are coming soon!
Resolved issues
- Paid customers will no longer see a trial banner in the UI.
2023-07-17: Token settings are now available when creating an OIDC app type
When orchestrating identity in a multi-cloud/IDP world apps have needs and we aim to fulfill those needs without requiring you to change code. In this release, we now expose the access token settings for specifying either a JWT or opaque access token, length, and lifetime.
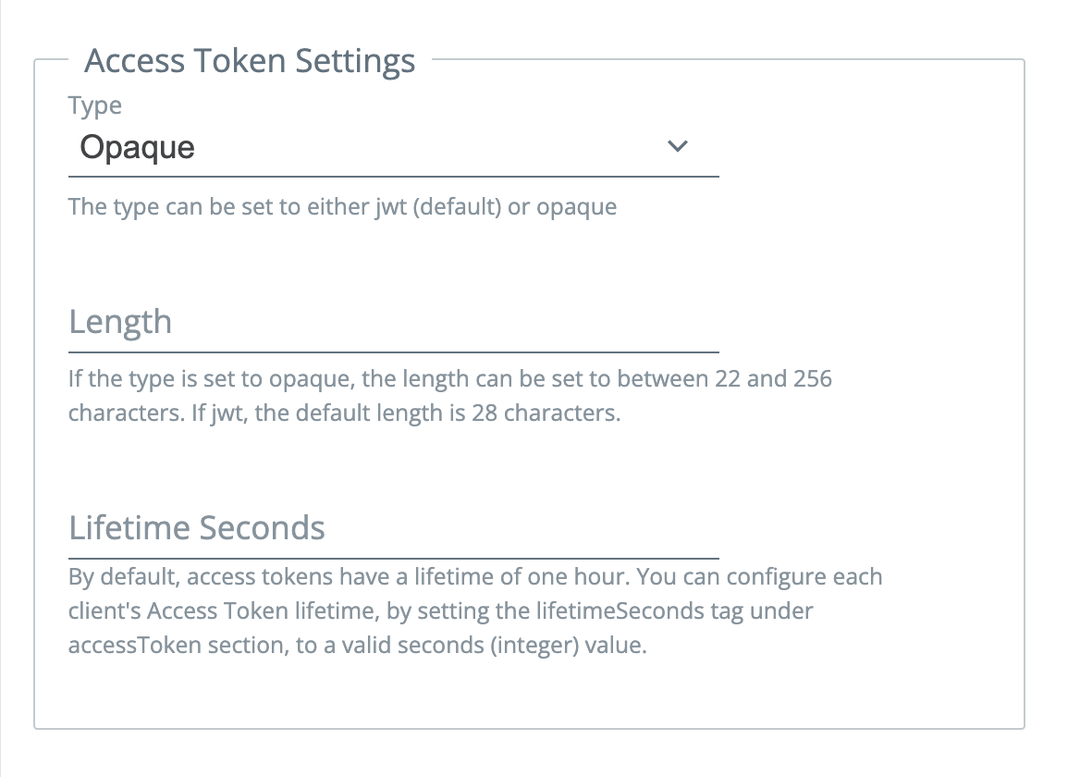
Note: The JWT length options require an upcoming orchestrator build to function properly. For now, select Opaque.
Resolved issues
- Removed non-functioning buttons on “Accounts” page.
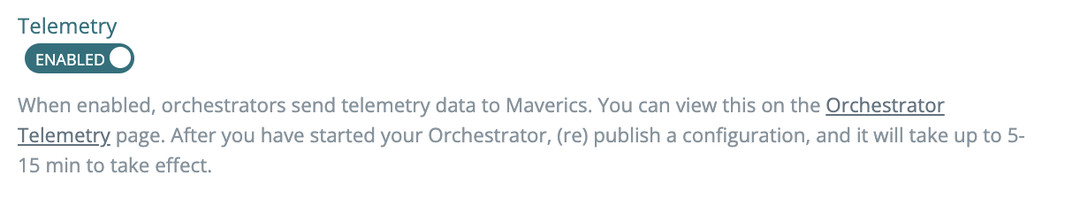
2023-07-11: Enable or disable telemetry
When creating or editing an environment, you will find a toggle switch to enable or disable sending telemtry to Maverics. Telemetry is on by default.
Resolved issues
- If user emails were entered with mixed case (for example, [email protected]), the users were not able to accept invites. This has been fixed.
- Users previously unable to accept invite can now click Accept Invite in the invitation email or if they have an account they can go to https://maverics.strata.io/accounts and click Accept.
- After you accept an invite, Maverics now automatically switches to the invited account.
2023-07-07: Create and update fine grained permissions with ease
We have reduced the steps and made the fine grained permissions capability for header based apps easier to find.
Now, when you create an access policy for a header based app’s resource you can set the policy all on one page. Each choice that you make automatically updates the policy. We have removed the confusing “Update” and “Back” buttons.
The policy code view has been moved to the top of the page and updates automatically on each change.
You can add conditional rules, toggle different authorization policies (like allow all), it will hide the conditions you created, and when you toggle back the conditions will no longer be lost.
See it in action:
2023-07-06: Deploy with confidence!
When publishing a configuration, you can now view the differences in the code view with the selected revision, compared to the selected environment. This helps you quickly scan the config for an attribute or mapping you may have missed.
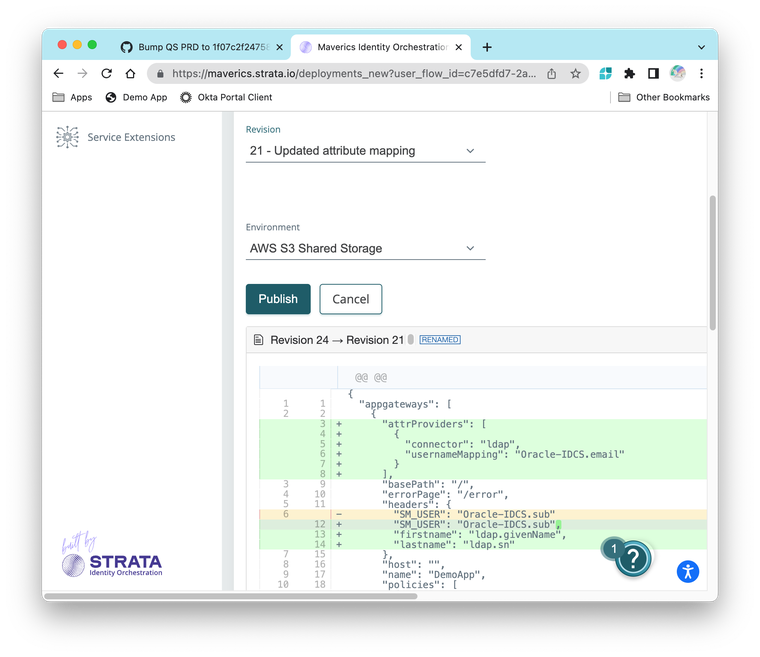
To compare:
- Save a revision (add an optional comment)
- Click Publish.
- On the deploy screen:
- Select the environment to compare against.
- Select a different revision to compare.
- In the code view green and + indicate additions while red and - indicate removals.
Additionally, Oracle ICDS (OIDC-based) Identity Service has been released. For more information, view the demo below.
Resolved issues
- Slow loading of pages with default and custom app icons. Note that with this change, any uploaded custom app icons will revert to default icons. You will need to re-upload any custom app icons you may have previously uploaded.
- After editing an environment, you are correctly returned to the environment page.
- Attribute provider configuration no loger persists in the deployed bundle after being removed from a user flow.
2023-06-30: Revision comments
You can now capture a revision comment and it will display on publish.
2023-06-29: Orchestrator health data is bigger and better!
Orchestrator health data can now be viewed on the Orchestrators page.
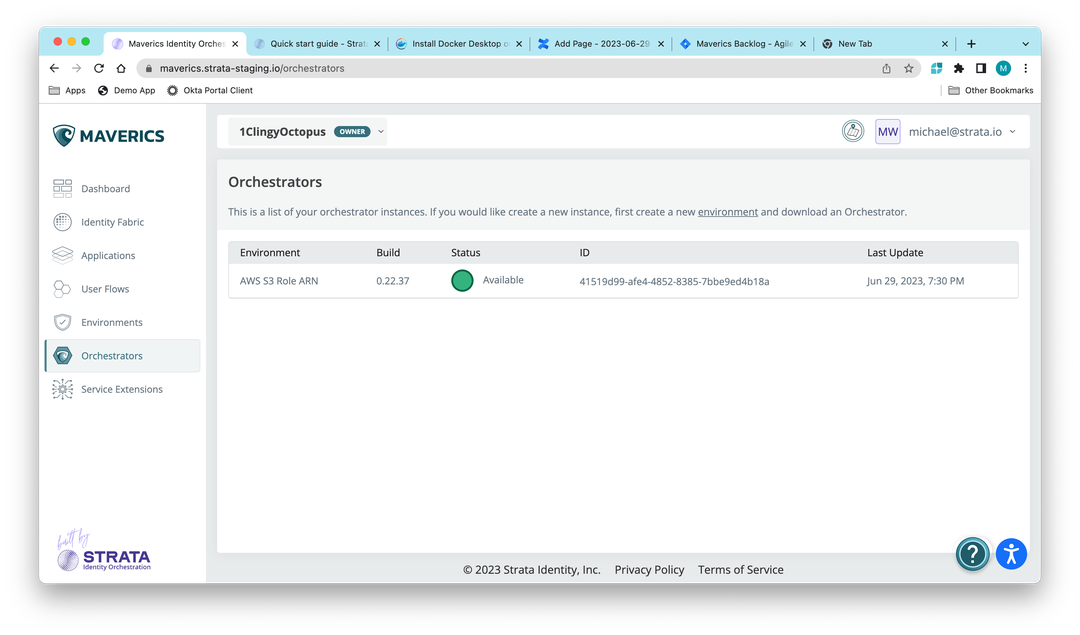
Orchestrator health data is sent to Maverics from Orchestrators and appears on the page after five minutes. If an orchestrator is stopped it will disappear after 15 minutes, however an unavailable state is not yet supported. Additionally, you can click the ID to see memory utilization.
Other enhancements
- We can now offer custom contract terms to customers with custom billing behavior, allowing you to start an annual subscription and pre-purchase up to a certain limit.
- Oracle’s Identity Cloud Service can now be configured as an IDP.
- Known issue: This sometimes triggers unexpected panics in orchestrators.
- You can now specify a destination for logout redirects.
- Known issue: Orchestrator does not yet support hot reload of logout URLs. You will need to manually restart orchestrators to see any change in logout behavior.
Resolved issues
- Headers with a “.” in the name can be deleted.
- You can no longer create a identity service with a name containing a “.” as this sometimes caused config to break downstream when used in a user flow.
2023-06-21: Maverics now supports Trusona
We use a standard OIDC connection to integrate Trusona’s passwordless solution. This enables another great passwordless option for customers who want to modernize their application without having to rewrite any application code.

Other enhancements
- Our interactive onboarding guide (powered by Pendo) just got better. It now points to the app map to start, and each step has an image to guide you through the process. First time visitors will see the onboarding guide every time they log in, until they have dismissed the guide twice. You can always refer to the onboarding guide again by visiting the Guides section in the Resource Center.
2023-06-20: Maverics Passwordless Account now powered by HYPR
Our sign up and login process has been improved! Maverics Passwordless Account powered by HYPR enables you to use Maverics without a password for free – no paid tenant required.
We’ve also added an app map in the top navigation to help guide your journey as a user.
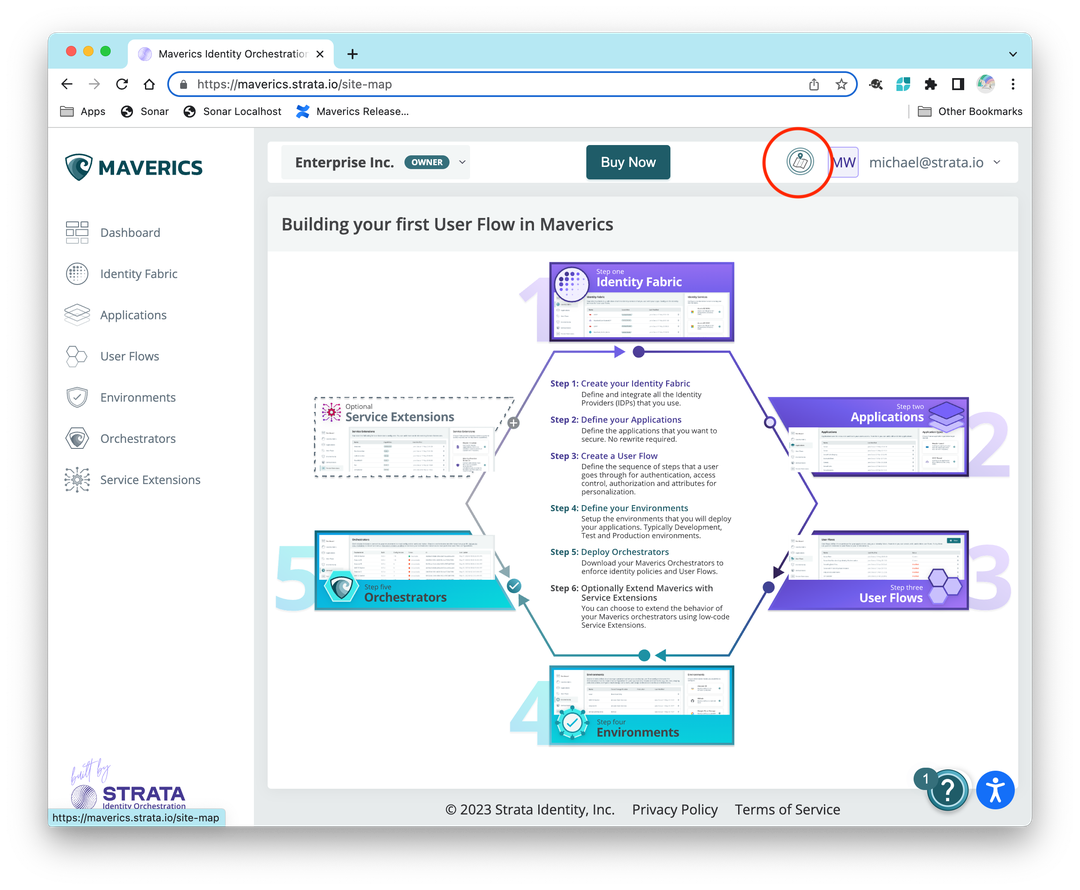
2023-06-14: Two releases!
You can now use your GitHub account to sign up and sign in to Maverics. Support for GitHub OAuth is a common authentication pattern and benefits admins, app owners, and developers using our product.
We’ve also improved instructions for using Microsoft Azure storage. You will also need to re-enter your SAS token any time you edit your environment.
2023-06-13: Accessibility, environments, and custom icons
We’ve implemented the accessWidget by accessiBe to automate web accessibility with AI. We are now over 95% in our scoring for web accessibility guidelines!
Additionally, as an enhancement to our hybrid zero trust architecture, we now support publishing configuration bundles to MS Azure Storage. This completes the end-to-end flow as Oochestrators could already read remote config from a Azure Storage container. Customers who have standardized on Azure now have more viable deployment options.
Finally, no matter how old or what kind of apps you have, Maverics can create user flows that can meet their identity needs. By uploading a custom app icon, you can make the Maverics experience more personal. We’ve also localized the date in time in our tables.
2023-06-09: Aloha Friday release notes
You can now download SAML metadata files from the Environments page. Additionally, you will be prevented from deleting an identity fabric referenced by a service extension.
2023-06-07: SAML and OIDC app types and user flows now fully available!
We now support orchestrating identity for modern applications that require Open ID Connect (OIDC) IDC for authentication (single orchestrator only). Additionally, in the environment settings you can now download SAML metadata. This streamlines the configuration process for some apps that support importing a SAML metadata file .xml format.
Other enhancements
- You can now publish configuations to Gitlab repositories.
- After 1 hr 58 min of inactivity you will be warned that your session will expire. You have 2 minutes to renew it and if you don’t you will be signed out.
Resolved issues
- You will now be prevented from deleting a identity service when it is associated with a user flow.
2023-06-06: Improved security for AWS S3 users
To improve security, Maverics now requires a IAM Role for publishing to a S3 bucket. The orchestrator configuration for reading config does not change, and existing environments configured to use a S3 buckets will continue to publish to S3 with an account ID and secret key. However, creating a new environment with an AWS S3 bucket or editing an existing environment requires cross-account roles. For more information, see Configure an environment.
Other enhancements
- You can now use Maverics to configure an orchestrator to act as a SAML auth provider for your applications.
- You can now specify the single logout endpoint (e.g. /logout) to trigger logout from all apps and IDPS.
- We’ve improved accessibility throughout Maverics to meet American Disability Act (ADA) standards.
- We’ve added Auth0 and Generic SAML as new IDPs.
2023-05-18: Feature refinements continue…
The Pricing link is now available from the Subscriptions page. Profile and Account menus are now clickable. Finally, the Publish button on individual User Flow pages now lives next to the Save Revision button, for better visibility.
Resolved issues
- The Learn more about Deployments link now points to the online help.
2023-05-17: Fixes and feature refinements
Today we addressed feedback we received from our first bug bash.
Resolved issues
- Updated Orchestrator description and fixed help links to creating an environment.
- Clicking Deployments breadcrumb no longer returns an error. The Deployments breadcrumb is now gone and correctly shows the path back to the User Flow.
- Cleaned up all the Learn More links.
- Describe the IAM permissions needed for an AWS S3 bucket. When creating an AWS S3 environment, we now show a Learn more and info icon which points to the AWS bucket policy in Remote configuration.
Other enhancements
- SAML app types are on the way! When creating a new or editing an environment you can now specify the Orchestrator URL.
- The Dashboard now has a short-cut to Invite a Member to your Account. This is a owner only action. If you are not the account owner it will take you to the member list.
2023-05-16: New recipes
As part of our PLG Onboarding initiative we want to make it super easy for evaluators to explore everything that Maverics has to offer. We made a couple small, but impactful changes to the user experience. It is a first step towards our grand plan to build out recipes and how they will simplify the difficult tasks of building a cohesive identity fabric.
- On the Dashboard, Import custom configuration has been renamed to Import Identity Orchestration Recipe.
- The new import screen has an updated description with links to the Quick Start Guide.
- The default import is the same config from the Quick Start Guide. Just click Create and you will have a fully baked and deployable user flow!
Other enhancements
- After creating a new environment, you’ll land on the show page so you can immediately move on to set up an orchestrator.
- Updated Learn More links throughout the app.
- New content and behaviors for the Welcome to Maverics onboarding screens.
2023-05-15: A new Sign Up and Sign In page, and creating environments
Our new Sign Up page is brought to you by an extra special collaboration with Product, Design, Marketing and Engineering.
Additionally, we’ve made several updates to our Environments flow:
- When creating and editing an environment you can now specify session and cookie domain settings used when proxying header based apps.
- When editing an environment you can easily download the public key file, configuration and a orchestrator build.
- You can now more easily download a deployed configuration for local testing.
2023-05-12: Updates to Environments and Service Extensions
You can now download an Orchestrator from an environment. On a new deployment, you can also go to an Environment by clicking its name.
Additionaly, you can now use a Create Header service extension on an Access Policy (e.g. reports). The service extension name now appears in the show field, and we’ve removed the unused Attribute field when adding a Create Header service extension.
Resolved issues
- The Buy Now button disappears if you’ve purchased a subscription.
2023-05-11: Secrets must be entered to update shared storage settings
Secrets must be re-entered to update any shared storage settings.
Resolved issues
When deploying a user flow, it will correctly bundle the latest service extension
2023-05-10: Create and edit environments
We uniquely enable our customers to compose an Identity Fabric and deploy User Flows for their applications, anywhere they are deployed. Our goal is to make this clear in practice when customers use Maverics to set up an environment, configure shared storage, connect orchestrators to the environment, and manage deployed User Flows.
Today we released Part 1 of this journey: Create and edit an environment.
- The Environments list enables you to choose the cloud storage provider or a local environment.
- Creating a new environment now has form input. You no longer have to copy and paste JSON code.
- Editing an environment has two tabs:
- Settings: Shared storage provider settings and orchestrator startup configuration
- Publish: User flows, get a public key for an orchestrator, download a deployed configuration
Other enhancements
- Renamed the Orchestrator download to maverics-orchestrator.
<ext>. This helps differentiate it from the maverics.tar.gz config bundle. - To delete your account and cancel your subscription in Chargebee, follow these steps: go to the Profile Menu, select Accounts, select the name of your Account, and click Delete. This will also remove you from any accounts you have been invited to.
2023-05-05: Buy Now and New User Flow Status
You can now self-service purchase a Maverics Subscription! After your trial period is over, the Buy Now button appears and you can purchase your subscription. The subscription estimate is based on the number of apps and IDPs published to an environment marked for Production. Watch our demo.
The User Flow list page also has a new Status column. The values are as follows:
- Current: The user flow is up to date with the current revision. No action needs to be taken.
- Modified: The user flow has changed and a new revision needs to be published. This can mean:
- The user flow itself has been edited (an access policy, provider, or header could have been added or updated)
- A referenced identity service has been updated. For example, adding a logout URL to a referenced OIDC authentication provider will require the user flow to be published again.
Watch our demo of the new user flow page.
Resolved issues
- The Last Modified columns will never be blank; it will either show the creation date or the last modified date.
- On a new deployment page, the Publish and Cancel buttons have been moved up for better visibility.
2023-05-03: Service extensions on the menu
You can now get to Service Extensions from the main navigation! From here you can create and edit 3 different extension points that can be used in User Flows for Header based apps: CreateHeaders, Authentication (Authenticate+IsAuthenticated), and IsAuthorized.
Resolved issues
- Fixed db migrations that were setting off alerts
2023-05-02: Simplified revise and publish
Revise and publish have been simplified! The previous steps to revise and publish a user flow were confusing and prone to errors. To simplify this experience:
- We’ve moved the Save As a Revision action, Publish action, and Automated Inspector to the top of a user flow.
- We’ve removed the side by side comparison from the bottom.
- We’ve the ability to override a calculated revision in the code view.
- We’ve moved read only code view to the new deploy step.
See a demo of the new user flow page in action.
Other Enhancements
- Branded identity service provider icons now appear on the user flow for easier identification.
- You no longer have to toggle a switch to select an available service extension.
Resolved Issues
- OIDC secrets are now hidden in form view.
- Header in on access controls in the User Flow views are no longer garbled
- New Header type descriptions are rendering properly
2023-04-21: Deploying secure bundles
We are excited to add support for deploying configuration as securely signed bundles! This security enhancement helps to ensure that the configuration being deployed is legitimate and has not been altered by malicious actors. In addition, bundles pave the way for us to deliver Service Extensions.
What do you need to know?
This security enhancement requires that you recreate your Environments with new key names and republish your user flows to those environments. You will need to update your Orchestrator to at least version: v0.19.0 which can be downloaded from the Orchestrators page.
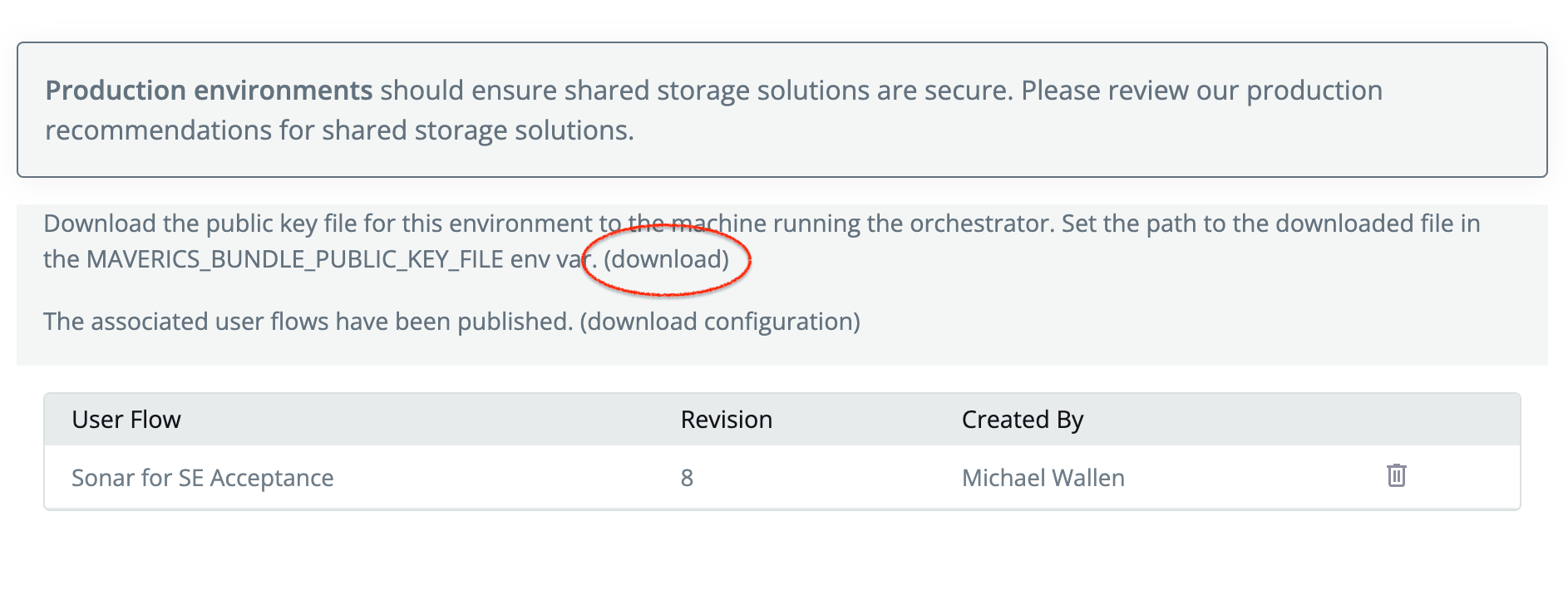
During a deployment Maverics bundles and signs the configuration with a digital signature that is unique to that environment. The bundle file is named “maverics.tar.gz.” When unzipped you see it contains maverics.json which is the configuration, jwt signature file, and a directory of any service extensions referenced in user flows.
The signed bundle is then validated by connected orchestrators configured to use that public key. If the validation fails, the Orchestrator will not load the configuration. To configure your Orchestrator, go to the environment page, download the public key file to the machine running the orchestrator. Set the path to the downloaded file in the MAVERICS_BUNDLE_PUBLIC_KEY_FILE env var.
Environment and Remote Config Key Names
configurationFileObjectKey and configuration_file_object_key are no longer supported.
configurationFilePathis new and is now the only key that specifies the file path to maverics.tar.gz.
Google Cloud Storage
bucket_name is no longer supported and has been renamed to bucketName which is consistent with all other environments.
2023-04-11: Fit and finish Maverics updates
Sidebar lists on right like Identity Services are now more compact and scrollable. App and Authentication sections of user flows are now more compact.
Additionally the Linux download for Maverics is now a tar.gz file.
Resolved issues
- When specifying a header, it is now required to be unique to the user fl ow at the app or resource policy level. The benefit here is that it will prevent you from specifying duplicate headers like SM_USER or firstname. This will avoid conflicts downstream.
2023-04-05: Maverics now supports Ping Federate SAML and OIDC
You can now use Ping Federate SAML and OIDC as an identity provider in your identity fabric.
Other enhancements
- Added SAML-based apps and user flows
- Includes adding/removing claims and attribute providers, and the ability to publish the SAML user flow. NOTE: SAML user flows are limited to one authentication provider
- Support for Oracle Universal Directory (OUD) as an attribute provider
- Added OIDC-based apps
- Added Automation-based apps
- Added Automation Flows: A user flow can be built on the newly introduced Automation app type.
- Support for Service Extensions: You can now upload and delete custom Service Extensions.
- 🚀 Easy Eval: Docker Compose includes Orchestrator, Keycloak - Quicksilver, PostgreSQL, Redis, Minio for shared storage
2023-03-30: Switch accounts in Maverics
This version of Maverics features a new account switcher in the top navigation and table restyling.
Other enhancements
- Fabric names are no longer editable after you create them. This prevents breaking elements downstream to referenced user flows. This is a temporary measure until IDs are implemented as references.
- The top navigation shows how many days are left in your trial. The Buy Now button appears when your trial has ended.
- A Re-publish button has been added to Environments. You can now delete user flows, edit startup configuration, and click Re-publish to push changes to your shared storage. Any waiting Orchestrator instances can pick up those changes.
Resolved issues
- Bug fixes and refinements
2023-03-24: The Mac version of Orchestrator is now available to download
You can now download the Orchestrator for Mac as part of an easy evaluation experience.
Other enhancements
- Inviting members is a few clicks closer! Click on the Account name in the top nav. From there you just click the “Add Members” button.
- We now send 💌 email to new member invitees
- Pendo is no longer be blocked by most ❤️ 🛑 ad blockers. This means that our Onboarding Guides and Resource Center can be shown to more visitors.
- The trial banner reminds you how many days you have left
- Fit and finish
- © 2023 Strata Identity, Inc. Privacy Policy now appears in the footer
- Spelling fixes
- Apps and user flows
- You can now remove a User Flow from an environment
- See a video: https://www.loom.com/share/4bb80cdc77994cb595c9acc304220dc2
Resolved issues
- 🔐 Now protected from cross-site forgery vulnerabilities
2023-03-20: Import custom configuration from the dashboard
You can now upload a custom configuration straight from the dashboard.
Resolved issues
- Less jumpiness when adding and removing headers on a user flow
2023-03-17: User flows now has a configuration inspector
Before you publish a revision, the configuration inspector will tell you if any IDPs or attribute providers are missing required information. The configuration inspector will look in app headers, policy rules, and policy headers for any missing components.
Headers used in a resource access policy also appear on the user flows.
Resolved issues
- Updating a policy preserves existing headers instead of deleting them
- Sign in with Microsoft account now shows Strata Identity instead of “unverified”
2023-03-16: Use Keycloak as an IDP
Maverics now supports adding Keycloak as an identity provider.
We are kicking off an initiative to deliver a self-service try and buy experience for Maverics. The Easy to Trial and Buy initiative will include several future releases with product tours, guides and videos, pre-built user flows, apps, and IDPs. The vision for this initiative is to allow prospects to implement one of our recipes using Maverics.
Soon we will deliver Keycloak as a ready-made, containerized IDP available through Maverics along with our Canary and Sonar demo apps. Evaluators will not have to go through the time and effort to bring their own IDP to trial Maverics.
Additionally, Subscriptions and Accounts have been moved from the left-nav to the user profile in the top-right corner of the Maverics user interface
Resolved issues
hostfield was not being properly written out when creating a header based app. To implement this fix for existing apps, you will need go to the app, add the host field, and revise & publish any user flows.- Fixed typos in UI
2023-03-13: AWS Cognito is now an authentication provider
Amazon Cognito is an OIDC-based IDP. You can now add AWS Cognito to provide authentication in your user flows.
Other enhancements
- Maverics now supports multiple user flows per environment! This means that you can do MORE with your POCs!
- The Orchestrators page no longer lists the User Flow list. To see which user flows are deployed where first go Environments and click on the environment you’d like to inspect.
- You can download the configuration from this page as well by clicking “(download configuration)” above the table.
- Import is on its way back into the product. You can import JSON by going to https://maverics.strata-staging.io/user_flows_import. This will make its way back to the Dashboard very soon.
- The config analyzer now provides context in the inspection results. This will now tell you which part of a user flow and the name of the provider its missing.
Resolved issues
- Fixed remaining gosec errors
- Code editor fixes
2023-03-08: HYPR is now an authentication provider
Customers can now include Hypr as a passwordless authentication provider in their identity fabric. Our partnership with HYPR is even stronger. You can now use Maverics to demonstrate how to modernize those pesky non-standard apps with passwordless authentication.
To give it a try, go to Identity Fabric in Maverics and click “Add” under the HYPR card to configure HYPR. You will need access to Strata’s HYPR Control Center demo tenant to use it. In the Control Center you will need the app’s details and a app user configured to test.
Then, create an app and user flow in Maverics. In the user flow authentication section, select your new HYPR provider. Use it in a policy for a resource. Finally, publish the user flow!
Other enhancements
- Subscriptions: environments can now report app and IDP usage split out between production and development environments
- Identity Fabric: secrets :closed_lock_with_key: such as LDAP passwords and OIDC client secrets are now hidden on form views
- User Flows: broader support for automated user flow inspection. It will now check for missing authentication providers in app headers and policy.
Resolved issues
- Chargebee will no longer fail to create customers from invalid sign up survey results
2023-03-07: Configuration analysis makes it easier for users to create configs
Configuration analysis makes it easier for users to create configurations that will always work when sent to an Orchestrator. In this first version, when you save a revision and the auth provider has been removed from the User Flow, a message will appear showing you that it could be missing from a resource policy or from an attribute provider definition. To see it in action, click here.
Additionally, Environments can now be tagged for Production use. This ensures that we only charge customers for apps and IDPs in their production environments.
Resolved issues
- UX – Marketing feedback on copy updates has been incorporated in this release.
- Several general refactors to improve the dev experience.
- Better performance of the Orchestrators page, by implementing asynchronous calls to the page when fetching Orchestrator status.
2023-03-02: Billing through Chargebee
On trial sign up, new customers and free trial subscriptions are created in Chargebee.
Other enhancements
- Sign up form improvements - you no longer lose your previous entries when attempting to Start Trial with missing fields
- A new Orchestrator available in Orchestrator/downloads. The downloads will always show the latest release.
Resolved issues
- Better messaging when attempting to delete a application that is referenced in a user flow
- Saving a new revision is no longer jumpy- We are updating interactions to HTMX all over the app so it will no longer scroll jump every time you hit a button. More to come!
2023-03-01: Use Github in Environments
Customers can now use a Github repository to publish config that configured orchestrators can consume.
Other enhancements
- Hypr sign up
- Improved step-by-step instructions in intersticial screen and emails
- Temporarily removed signing in using fido2 devices
- Sign up form - remove generated name and make all fields required
- Text and editorial feedback - thanks to a ton of feedback from Marketing, Design and Docs the copy in the UI is much cleaner and consistent
- User Flows - Add multiple rules and conditions to an access policy
Resolved issues
- Make LDAP delimiter optional
- Fixed bad request when editing an account after switching accounts
2023-02-28: Maverics has shipped!
We are excited to announce the first commercial ship (FCS) of https://maverics.strata.io, our newest offering designed to help businesses onboard to the Maverics Identity Orchestration Platform. The initial release provides a comprehensive set of capabilities primarily focussed on modernizing non-standard header based apps.
What do you need to know?
- Maverics is now available for any user to sign up for a free trial. If customers would like to purchase they will need to contact sales.
- A quick start guide available for evaluators at docs.strata.io
- Status of the app’s availability can be monitored at status.strata.io
- Existing customers and partners can open support tickets through our customer portal.
What’s next?
We will be releasing enhancements very often focussed on polished UX, adding more choices like AWS Cognito & Hypr when creating Identity Fabric, additional app types, and so much more! Release notes like these will be published as a Confluence Blog in the #general channel. If you need access to Confluence please reach out to @Eric Leach (Unlicensed) and he can resend an invite.
Orchestrator Builds
v0.27.124
2024-09-27
- [Tests] Use dynamically allocated free port - #2584
v0.27.123
2024-09-26
- Update github PR template - #2582
- [Connectors] Implement login_hint in query for Azure SAML - #2583
v0.27.122
2024-09-23
- [SE] Add ‘postLogoutSEV2’ service extension - #2580
v0.27.121
2024-09-19
- Ensure mTLS can not be bypassed by spoofing the Host header. - #2578
v0.27.120
2024-09-19
- [Connectors] Restore SAML login in PingFed - #2579
v0.27.119
2024-09-19
- [Connectors] Add login hint to OIDC connectors - #2577
v0.27.118
2024-09-17
- [Proxy apps] Allow secrets loading in policy locations - #2576
v0.27.117
2024-09-17
- [SE] Introduce v2 service extension signature for ’evalIdleTimeoutSE’ - #2574
v0.27.116
2024-09-17
- Support retrieving AWS secrets via ARN - #2575
v0.27.115
2024-09-17
- Update ‘golang.org/x’ to latest - #2564
v0.27.113
2024-09-16
- [SE] Introduce v2 session evalMaxLifetime - #2562
v0.27.112
2024-09-13
- [Service Extensions] Fix route registration issue - #2572
v0.27.111
2024-09-12
- Add newline delimiter option in CCP as workaround for multi-line secrets. - #2570
v0.27.110
2024-09-09
- Format the Hypr HTML to make it more readable - #2567
v0.27.109
2024-09-09
- SAML App inherits signing cert from SAMLProvider - #2566
v0.27.105
2024-09-03
- Fix OIDCProvider panic when claims mapping attribute does not use connector notation - #2560
v0.27.104
2024-08-29
- [Bundle Validation] Improve error handling when loading public key - #2558
v0.27.103
2024-08-28
- [TLS] Rename ‘clientCAs’ to ‘clientCAFiles’ in TLS config - #2554
v0.27.102
2024-08-28
- [Continuity] Improve reload behavior - #2555
v0.27.101
2024-08-27
- [Continuity] Check for duplicated status codes - #2549
v0.27.100
2024-08-27
- [Continuity] Add health check to ADFS - #2545
v0.27.99
2024-08-27
- [Connectors] Make cert and keys paths optional for ADFS - #2557
v0.27.97
2024-08-22
- Fix custom endpoint test flake - #2553
v0.27.96
2024-08-22
- Support LoadAttributesSE for OIDC Apps - #2551
v0.27.95
2024-08-22
- Enable service extensions for oidc provider authorization - #2548
v0.27.94
2024-08-21
- Support multiple secrets for OIDC client authentication - #2546
v0.27.93
2024-08-20
- Add load attributes service extension to SAML apps - #2544
v0.27.92
2024-08-19
- Ensure OIDC clients are unique by client ID - #2542
v0.27.91
2024-08-17
- [SAML Apps] Support app level ‘disableSignedAssertion’ and ‘disableSignedResponse’ - #2540
v0.27.90
2024-08-15
- Add authorization rules to OIDC apps - #2541
v0.27.89
2024-08-14
- Sanitize routes registered in Service Extensions - #2539
v0.27.88
2024-08-13
- [SAML Apps] Support app-specific signing certs - #2535
v0.27.87
2024-08-13
- Support client defined grant types for OIDC apps - #2538
v0.27.86
2024-08-13
- [Continuity] Remove body matching response logging - #2537
v0.27.85
2024-08-12
- Update mitchellh/mapstructure to go-viper/mapstructure/v2 - #2533
v0.27.84
2024-08-12
- [Apps] Validate ’name’ uniqueness - #2531
v0.27.83
2024-08-09
- Support ROPC flow for OIDC apps via backchannel authenticate SE - #2532
v0.27.82
2024-08-08
- [Continuity] Increase state parameter length in generic OIDC health check - #2530
v0.27.81
2024-08-06
- [Continuity] Add TLS to custom health check - #2527
v0.27.79
2024-07-31
- Support IsAuthorizedSE in SAML apps - #2525
v0.27.78
2024-07-31
- [Continuity] Add custom health check response body matching - #2522
v0.27.77
2024-07-29
- Use the correct HTTP client for SAML health check - #2523
v0.27.76
2024-07-29
- [Continuity] Add headers to custom health check endpoint - #2519
v0.27.75
2024-07-26
- Add QR authentication mode for Hypr connector - #2518
v0.27.74
2024-07-25
- [Continuity] Add ability to define custom health check - #2515
v0.27.73
2024-07-19
- [Continuity] Change the default health check interval - #2512
v0.27.72
2024-07-19
- [Continuity] Add un/healthy threshold - #2513
v0.27.71
2024-07-18
- Enforce authorization rules in SAML Apps - #2514
v0.27.69
2024-07-17
- Reimplement Cyberark Conjur Secret Provider - #2510
v0.27.68
2024-07-12
- Update Yaegi to 16.1 - #2509
v0.27.66
2024-07-11
- Remove legacy LDAP ‘attrproviders’ implementation - #2506
v0.27.64
2024-07-10
- [SAML APP] Query for nameID attributeMapping attribute if not on session - #2503
v0.27.63
2024-07-09
- Update log level to error when referenced secret is not found - #2505
v0.27.60
2024-07-02
- Expose ldap.Control - #2498
v0.27.57
2024-06-27
- Add AWS Secrets manager secret provider support - #2496
v0.27.56
2024-06-25
- [Telemetry] Update OTel libraries to latest - #2495
v0.27.54
2024-06-24
- [Telemetry] Update local Docker Compose telemetry environment for development - #2494
v0.27.53
2024-06-24
- Support reload for single logout config - #2491
v0.27.49
2024-06-20
- Protect session store with mutex and add session service to config reloader - #2490
v0.27.48
2024-06-19
- Implement session config reload - #2487
v0.27.46
2024-06-18
- [Service Extensions] Expose symbols for JWT encryption - #2485
v0.27.45
2024-06-18
- Wrap session in service.Service - #2483
v0.27.43
2024-06-14
- [MSI] Fix file contention issue - #2482
v0.27.42
2024-06-14
- Re-evaluate policies based on decision lifetime - #2478
v0.27.38
2024-06-11
- [Proxy apps] Remove legacy resilience implementation - #2475
v0.27.36
2024-06-06
- Redirect SAML SSO error responses correctly - #2472
v0.27.33
2024-05-31
- SAMLProvider support LogoutRequest via POST binding - #2470
v0.27.32
2024-05-30
- [Connectors] Move SAML client initialization to constructor - #2469
v0.27.31
2024-05-29
- [Connectors] Gracefully handle failure to retrieve OIDC well-known metadata - #2466
v0.27.30
2024-05-16
- Verify Signed SAML Logout requests via Redirect binding - #2468
v0.27.29
2024-05-16
- [Connectors] Refactor SAML pkg to better handle SP initialization - #2467
v0.27.28
2024-05-14
- [SAML Apps] Store logout request in cache - #2465
v0.27.27
2024-05-14
- Fix SAMLProvider cacheState storage when using multiple IDPs - #2464
v0.27.26
2024-05-13
- Add support for namespace in HashiVault - #2460
v0.27.23-24
2024-05-10
- Unregister SAMLProvider SLO endpoint during stop - #2463
- [Connectors] Better handle logout errors - #2461
v0.27.20-21
2024-05-09
- Update release pipeline to replace the old MSI installer with the new - #2458
- Append query parameters to authn request during IDP Initiated SAML - #2459
v0.27.19
2024-05-08
- Validate bundle file in MSI installer - #2457
v0.27.16-18
2024-05-07
- [SAMLProvider] Add SingleLogoutService to metadata when sloEndpoint is defined - #2456
- [SAMLProvider] Implement SP initiated SLO - #2441
- [MSI] Fix service restart when change and add default remote configs. - #2442
v0.27.13-15
2024-05-06
- [Service Extensions] Expose symbols to enable JWT generation - #2450
- [Connectors] Set transport properties on health check HTTP client - #2449
v0.27.12
2024-05-03
- [SAML Connectors] Fix panic observed when generating unsigned logout requests - #2452
v0.27.5
2024-04-23
- [SAML Apps] Call BuildRelayState extension post-authentication
v0.27.2
2024-04-18
- [SAML Apps] Expose NameID configuration
v0.27.1
2024-04-18
- Include allowedProtectedPackages option for Service Extensions
v0.27.0
2024-04-16
- Introduce cache to SAMLProvider
v0.26.108
2024-04-16
- Expose BuildRelayState service extension for IDP-initiated login flow
v0.26.106
2024-04-12
- Allow IDP-initiated ‘relayStateURL’ field to be optionally defined
v0.26.102-104
2024-04-11
- Fix log key to have correct attrProvider name
- Simplify IDP health check service
v0.26.94-100
2024-04-10
- Implement generic SAML in 1Kosmos and add cache
- Improve idphealthcheck test assertion
- Manually validate timestamp assertions in SAML
- Organize authprovider pkg and improve logging
- Store cacheRequester on samlAuthProvider to simplify CreateClient method signature
v0.26.90
2024-04-04
- Add proxy app support for HTTP request methods
v0.26.87-89
2024-04-03
- Enable PingFederate connector to use SAML package and cache
- Bug fix: Add ‘Authorization’ to list of ‘Access-Control-Allow-Headers’
v0.26.86
2024-04-02
- Set SAML CacheRequester at reload
v0.26.85
2024-04-01
- Add cache for SAML connectors using generic implementation
v0.26.75-77
2024-03-25
- Enhance SAML metadata parsing to support formatted certificates
- Support api.App in IsAuthenticatedSE, AuthenticateSE and v2/BuildClaimsSE for saml apps
- Support api.App in IsAuthenticatedSE, AuthenticatedSE, BuildAccessTokenClaimsSE, BuildIDTokenClaimsSE for oidc apps
v0.26.73-74
2024-03-22
- Update Nancy CI action to use correct version of Go
- Add support RP-initiated logout in OIDC provider
v0.26.66-71
2024-03-20
- Add
github.com/google/uuidsupport to Service Extensions. - Support api.App in loadAttrsSE for proxy apps
- Support api.App in createHeaderSE for proxy apps
- Support api.App in loginSE and isLoggedInSE for proxy apps
- Allow CyberArk CCP to be configured with certificate authentication directly from Windows Cert Store. See docs here.
v0.26.64
2024-03-19
- Add missing Cache WithTTL option to SE symbols
v0.26.63
2024-03-18
- Add functions and structures from ‘golang.org/x/net/html’ to v2 SEs.
v0.26.54
2024-03-14
- Update go-ntlm to the latest version
v0.26.22
2024-02-29
- Update to latest go OTLP libraries
v0.26.17
2024-02-26
- Upgrade Golang to 1.22
v0.26.13
2024-02-22
- Parse the OIDC Auth request params to not only parse from the query but also from the request body
v0.26.4
2024-02-08
- Add configuration options to MSI installer and fix upgrade behavior
v0.26.3
2024-02-08
- Support loading service extension assets as a file system
v0.26.2
2024-02-06
- Add offline_access to scopes_supported in OIDC well-known endpoint
v0.26.1
2024-02-02
- Implement Context interface for service extensions
v0.26.0
2024-01-31
- Support retrieving App name for Proxy Apps in some Service Extensions
- Expose orchestrator cache to service extension (v0.25.39)
- Add client_id to claims in access token (v0.25.38)
- Support login options in service extensions (v0.25.37)
- Fix refresh token length configuration (v0.25.35)
- Close HTTP response body in connectors (v0.25.34)
- Omit env var substitution if the line starts with ‘#’ in YAML config (v0.25.33)
- Close response body when making token request (v0.25.32)
- Update crypto lib to v0.17.0 to handle CVE-2023-48795 (v0.25.31)
- Fix panic when cert not found in Windows cert store (v0.25.30)
- Correctly set RelayState during IDP initiated login (v0.25.29)
- Add env vars for Windows Certificate Store (v0.25.28)
- Improve error handling in OIDC connectors (v0.25.27)
- Add support for reloadable cache (v0.25.26)
v0.25.25
2023-12-14
- Allow SAML client to support both IDP initiated login and verified SP login
- Rename go-jose exported name from v3 to jose (v0.25.24)
- Add Windows Client Authenticator connector to orchestrator (v0.25.23)
v.0.25.5
2023-11-24
- Register SAML endpoints as case insensitive
- Register OIDC endpoints as case insensitive (v0.25.4)
- Fix typo in telemetry logs (v0.25.3)
- Implement TAIProvider interface for Service Extensions (v0.25.2)
- Fix panic observed when running in Windows console as non-admin (v0.25.1)
v0.25.0
2023-11-09
- Rotate refresh tokens on use per OAuth security best practices
- Implement token revocation for JWT tokens (v0.24.35)
- Store JWT tokens in the cache (v0.24.34)
v0.24.32
2023-11-03
- Update google.golang.org/api to fix indirect GRPC vulnerabilities
- Expose GetBytes, GetAny, and SetBytes on Service Extension session provider implementations (v0.24.32)
- SAMLProvider validates signed authn requests received via HTTP-Redirect binding (v0.24.29)
- Implement v2.Session API for Service Extensions for OIDC Provider (v0.24.28)
- Add post logout redirect URL to proxy apps (v0.24.27)
- Return all claims for opaque access token (v0.24.26)
- Add logout to proxy apps (v0.24.25)
- Add clock skew leeway for SAML Authn requests (v0.24.23)
- Stop Maverics process on failure to bind to a port (v0.24.22)
v0.24.21
2023-10-26
- Add support for IDP initiated login for app of type SAML
- Add support for HTTP Redirect binding in the SAML auth provider (v0.24.20)
- Improve attribute loading error handling in proxy apps (v0.24.18)
- Add query params matching in proxy apps policies (v0.24.17)
- Add handleUnauthorizedSE to proxy apps (v0.24.16)
v0.24.15
2023-10-20
- Add upstream login extension to proxy apps
- Add support for IDP initiated login for the SAML provider (v0.24.14)
- Add ModifyRequest and ModifyResponse Service Extensions to proxy apps (v0.24.13)
- Add LoadAttrsSE to proxy apps (v0.24.12)
- Expose ‘goPath’ on v2 Service Extensions (v0.24.11)
- Add CreateHeader service extension to proxy apps (v0.24.10)
- Add IsAuthorized service extension to proxy apps (v0.24.9)
- Add IsAuthenticated and Authenticate extensions to proxy apps (v0.24.8)
- Update goxmldsig library to fix signature validation bug (v0.24.7)
- Add TLS to proxy apps (v0.24.4)
- Patch CVE-2023-45683 (SAML XSS bug) (v0.24.2)
- Support multiple route patterns on a proxy app (v0.24.1)
- Add Orchestrator Groups cache support (v0.24.0)
- Add regexp policy matching to proxyapps (v0.23.75)
- Add attribute provider to proxy apps (v0.24.74)
v0.23.73
2023-10-13
- Update golang.org/x/net to the latest to address CVE-2023-39325
- Upgrade Yaegi to 15.1 (v0.23.72)
- Support policy-level header definitions on proxy apps (v0.23.71)
- Implement revoke endpoint support for OIDC refresh tokens (v0.23.70)
- Add unauthorized page to proxy apps (v0.23.68)
- Add headers to proxy apps (v0.23.67)
- Improve authorization and authentication policy validation for proxy apps (v0.23.66)
- Add authorization to proxy apps (v0.23.65)
v0.23.62
2023-09-29
- Add basic authentication to proxy apps in new app-centric configuration format
- Allow fabric consumer (RP Orchestrator) to define and use unauthorizedPage (v0.23.61)
v0.23.60
2023-09-25
- Update OIDCProvider service extensions to work with cache
- Fix OIDCProvider userinfo endpoint to reject ID Bearer tokens (v0.23.59)
- Support the refresh token flow using the cache (v0.23.58)
- OIDCProvider uses cache to build user claims (v0.23.56)
v0.23.55
2023-09-15
- Support AuthCode w/ PKCE using cache implementation
v0.23.54
2023-09-15
- Make logging more verbose in Azure connector
v0.23.53
2023-09-11
- Remove logic that prevents ‘ServeSE’ from being defined with other AppGateway extensions
- Set session cookie regardless of policy (v0.23.52)
v0.1.0 (Maverics TAI Module)
2023-09-07
- Add support for verifying signed JWT headers to prevent impersonation via side channel requests.
v0.23.50
2023-09-07
- Expose TAI pkg in Service Extensions to enable JWT generation
- Fix decryption using older keys in AES256GCMEncryptor (v0.23.49)
- Export go-jose JWT library v3 symbols (v0.23.48)
- Export go-ldap library v3 symbols (v0.23.47)
v0.23.44
2023-08-29
- Expose ’ldap.NewModifyRequest’ in Service Extensions
- Add metadata to V2 service extensions (v0.23.43)
- Signed binaries for Maverics Evaluation bundle downloads (v0.23.42)
- Fix Telemetry panic on SIGTERM (v0.23.38)
- Update SAML Provider buildClaims v2 signature to match OIDC Provider. (v0.23.37)
- Enable attribute loading in v2 Service Extensions (v0.23.34)
- Make API Service Extensions reloadable (v0.23.31)
- ServeSE v2 in APIs block (v0.23.28)
- Add ldap.NewPasswordModifyRequest symbol (v0.23.27)
- Add support for BuildUserInfoClaimsSE for OIDC apps (v0.23.25)
v0.23.34
2023-08-15
- Enable attribute loading in v2 Service Extensions - #2147
v0.23.31
2023-08-11
- Make API Service Extensions reloadable - #2140
v0.23.30
2023-08-11
- Unregister HTTP endpoints when API Service Extensions are stopped - #2139
v0.23.29
2023-08-11
- Restart session metrics on telemetry reload - #2119
v0.23.28
2023-08-11
- ServeSE v2 in APIs block - #2134
v0.23.27
2023-08-10
- Add ldap.NewPasswordModifyRequest symbol - #2136
v0.23.26
2023-08-10
- Orchestrator metrics as service - #2122
v0.23.25
2023-08-10
- Add support for BuildUserInfoClaimsSE for OIDC apps - #2135
v0.23.22
2023-08-03
- Fixed issue preventing OIDC client creation with JWT access token - #2110
v0.23.20
2023-08-03
- Return a non-nil action in the HYPR connector when Lookup is successful - #2130
v0.23.19
2023-08-03
- Add BuildClaims SE to SAML apps - #2128
v0.23.18
2023-08-02
- Move authn fields under new authenticationPolicy in policy struct - #2123
v0.23.15
2023-07-28
- Add Authentication Service Extensions to SAML Apps - #2121
v0.23.14
2023-07-28
- Add BuildIDTokenClaims and BuildAccessTokenClaims extensions to apps of type OIDC - #2120
v0.23.13
2023-07-28
- Remove Public Signing Key from Auth Provider Config - #2117
v0.23.11
2023-07-26
- Add IsAuthenticated and Authenticate SE to OIDC apps - #2118
v0.23.9
2023-07-25
- Support subtree searching for LDAP connector as IDP - #2114
v0.23.8
2023-07-24
- initialize metrics during orchestrator startup - #2115
v0.23.6
2023-07-19
- Create v2 Service Extension package and expose parsing method - #2113
v0.23.2
2023-07-17
- SAML AuthProvider: Ensure XML dateTime attributes use millisecond precision - #2111
v0.23.1
2023-07-13
- Remove connector and app count logging - #2098
v0.23.0
2023-07-12
- Enable NameID Format to be defined on SAML AuthProvider clients - #2103
v0.22.48
2023-07-12
- Only set SameSite cookie attribute when cookie is Secure - #2101
v0.22.47
2023-07-12
- Remove “reload count” metric - #2099
v0.22.46
2023-07-12
- add config version to health - #2096
v0.22.41
2023-07-07
- Ensure Lookup validation is successful before using connector as IdentityProvider - #2091
v0.22.40
2023-07-07
- Refactor telemetry into a service and change the Reloader to reload telemetry based on new config. - #2093
v0.22.38
2023-07-05
- Fix LDAP IDP login bug - #2085
v0.22.37
2023-06-28
- SAML logout in Okta - #2075
v0.22.34
2023-06-27
- Emit Orchestrator health to OTLP - #2065
v0.22.33
2023-06-26
- Remove old HealthSvc - #2082
v0.22.32
2023-06-26
- Prevent SAML auth provider from panic if no IDPs provided. - #2080
v0.22.29
2023-06-23
- Add ldap.DialWithTLSConfig to Service Extension symbols - #2077
v0.22.26
2023-06-20
- Add redirectScheme to consumer fabric - #2069
v0.22.22
2023-06-19
- Organize and add Godoc for configuration fields in AppGateway - #2070
v0.22.19
2023-06-16
- Fix issue where Fabric Consumer (RP Orchestrator) fails to load TLS config - #2064
v0.22.18
2023-06-16
- Add os/exec to service extension symbols if enableOSLib:true - #2063
v0.22.17
2023-06-16
- Return ErrMetricsInvalidExporter if exporter not specified in telemetry metrics configuration - #2066
v0.22.16
2023-06-15
- Refactor telemetry config to allow multiple OTLP exporters; reference… - #2057
v0.22.14
2023-06-15
- Improve error handling in Fabric Consumer when nonce is not found - #2060
v0.22.11
2023-06-14
- Add ldap.NewSearchRequest to service extension symbols - #2052
v0.22.9
2023-06-14
- Don’t log message about metrics when telemetry not enabled. - #2050
v0.22.8
2023-06-13
- Add support for domain hint in SAML SP - #2053
v0.22.7
2023-06-13
- Support SAML login in Okta connector - #2051
v0.22.6
2023-06-13
- Leave maverics.yaml untouched on uninstall - #2049
v0.22.5
2023-06-08
- Support IDP-initiated SAML login in ADFS connector - #2047
v0.22.4
2023-06-08
- Support IDP-initiated SAML login in Azure connector - #2048
v0.22.3
2023-06-08
- Add default maverics.yaml on Windows installation - #2046
v0.19.17
2023-05-03
- Ensure keys in JWKS have unique IDs - #1990
v0.19.16
2023-05-03
- Add support for apps of type OIDC - #1987
v0.19.15
2023-05-03
- fix cache timing logic - #1992
v0.19.14
2023-05-03
- Describe Service Extension dependencies for AuthProviders - #1991
v0.19.13
2023-05-02
- [OIDC Auth Provider] Inject unused cache.Cache - #1988
v0.19.12
2023-05-02
- [OIDC Auth Provider] Move cache creation into NewOIDCProvider - #1984
v0.19.11
2023-05-02
- add URLPath to otel http config - #1980
v0.19.10
2023-05-02
- Add Orchestrator ID to metrics resources - #1976
v0.19.9
2023-05-01
- Add username search key value to session for LDAP - #1985
v0.19.8
2023-05-01
- Handle error from service extension panic recovery - #1986
v0.19.7
2023-05-01
- Add source assets for the docker grafana quickstart in docs repo. - #1978
- Serve discovery endpoints on app-centric OIDC Provider - #1983
v0.19.6
2023-04-27
- Add ability to create clients on OIDC AuthProvider - #1982
v0.19.5
2023-04-27
- add mock cache implementation - #1981
v0.19.4
2023-04-26
- Removes the AuthProvider feature flag - #1979
v0.19.3
2023-04-26
- add initial caching foundation - #1968
v0.19.2
2023-04-21
- Add MAVERICS_CONFIG to multiple environment variable check - #1975
v0.18.48
2023-04-21
- Distinguish between validation and unmarshalling in OIDCProvider by @patrick-strata in #1969
- Remove undocumented and unused logical operators from OIDC AuthProvider authentication policy by @patrick-strata in #1970
- Query escape configuration_file_object_key for GCP provider by @wfernandes in #1972
- Decouple unmarshaling from construction in OIDC AuthProvider in support of OIDC apps by @eliasjf in #1973
- Support configurationFilePath key in provider configs by @wfernandes in #1971
- Implement bundle verification by @kewun in #1967
- Organize tests into separate files for OIDC AuthProvider by @eliasjf in #1974
Full Changelog: https://github.com/strata-io/maverics/compare/v0.18.47...v0.18.48
v0.19.1
2023-04-21
- Distinguish between validation and unmarshalling in OIDCProvider by @patrick-strata in #1969
- Remove undocumented and unused logical operators from OIDC AuthProvider authentication policy by @patrick-strata in #1970
- Query escape configuration_file_object_key for GCP provider by @wfernandes in #1972
- Decouple unmarshaling from construction in OIDC AuthProvider in support of OIDC apps by @eliasjf in #1973
- Support configurationFilePath key in provider configs by @wfernandes in #1971
- Implement bundle verification by @kewun in #1967
- Organize tests into separate files for OIDC AuthProvider by @eliasjf in #1974
Full Changelog: https://github.com/strata-io/maverics/compare/v0.18.47...v0.19.1
v0.18.47
2023-04-18
- Simplify SAML Provider signature configuration - #1966
v0.18.46
2023-04-18
- Add encryption to SAML Apps - #1965
v0.18.45
2023-04-17
- Update Swarm to latest - #1964
v0.18.44
2023-04-17
- Remove antiquated autogenerated LDAP test mock - #1962
- Remove outdated telemetry docs - #1961
- Enable encryption config to be defined on SAML AuthProvider client - #1963